
CyberEdge 2024 Cyberthreat Defense Report
Read More
Reports

CyberEdge 2024 Cyberthreat Defense Report
Read More
Reports

Picus Security Introduces Picus Numi AI, Transforming Security Prioritization with Contextual Insigh..
Read More
On demand: Top Ten ATT&CK Techniques: The Rise of ‘Hunter-Killer’ Malware
Watch Now
Webinar

The Red Report 2024: The Top 10 Most Prevalent MITRE ATT&CK Techniques
Read More
Reports

Surge in “Hunter-killer” Malware Uncovered by Picus Security
Read More

Picus Security Is Named 2024 Gartner® Peer Insights™ Customers’ Choice for Breach and Attack Simulat..
Read More
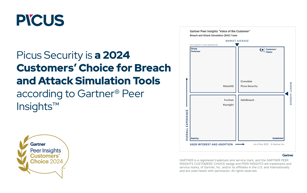
2024 Gartner® Peer Insights™ Voice of the Customer for Breach and Attack Simulation (BAS) Tools
Read More
Reports

On demand: Lateral Movement Attacks: Silent, Persistent Destructive
Watch Now
Webinar
Ransomware Incidents Reported to UK Financial Regulator Doubled in 2023
Read More
Article

Gartner: How to Select the Right Penetration Testing Provider for Your Organization
Read More
Reports

Picus Launches New MSSP Program to Make Starting Security Validation Simple
Read More

Whitepaper: Building a Robust Defense-in-Depth Strategy with Breach and Attack Simulation (BAS)
Read More
Reports