How to Leverage the MITRE ATT&CK Framework for Threat Intelligence
Suleyman Ozarslan
April 19, 2022
The MITRE ATT&CK Framework allows us to understand the adversary behavior by revealing:
-
What are their motivations?
-
Which countries and sectors do they target?
-
Which techniques do they use?
-
Which tools do they utilize?
Regardless of the maturity level of cybersecurity teams, ATT&CK can help any organization. The MITRE ATT&CK team has determined three different maturity levels and made recommendations for these levels. This blog explains how organizations can utilize the MITRE ATT&CK Framework as a threat intelligence source for each level.
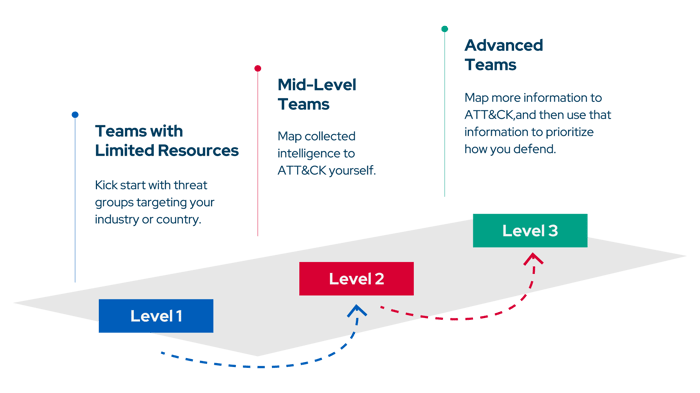
Level 1 Threat Intelligence
If your organization lacks a threat intelligence team, you can start with a single threat group targeting your organization, industry, or region. Then you can look at the threat group's techniques.
Example - Level 1 Threat Intelligence with ATT&CK
Assume that your organization is a U.S. telecommunication company. Let’s go to the MITRE ATT&CK homepage and search the “telecommunications” keyword.
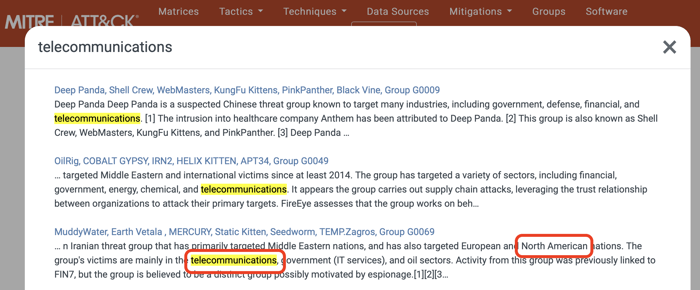
You will find several threat groups targeting our sector. Then, you need to review these groups. For example, the MuddyWater group targets the telecommunications and oil sectors in North America. So, this group is very relevant to your organization. You can start with MuddyWater. Let’s click on the MuddyWater link and go to the page of this group.
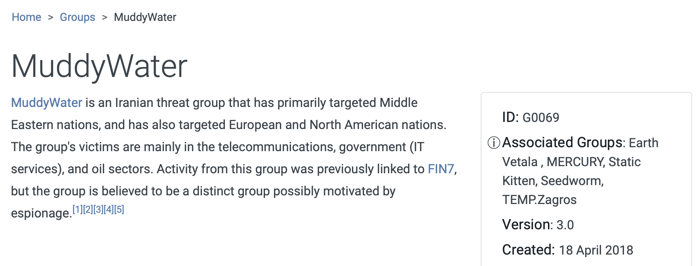
As seen on the page, ATT&CK provides attribution of the group, targeted geographies, and targeted sectors. The MuddyWater APT group is attributed to Iran, targeted regions are the Middle East, Europe, and North America, and targeted sectors are telecommunication, government, and oil.
On a group’s page, ATT&CK also provides associated groups, which are the same or very similar groups in various threat intelligence reports. Knowing the associated group names is essential for threat intelligence since vendors have no consensus about threat group naming.
On the group's page, you can discover more about them by looking at their techniques. For each threat group, ATT&CK includes techniques used by the group and briefly describes how the group used techniques.
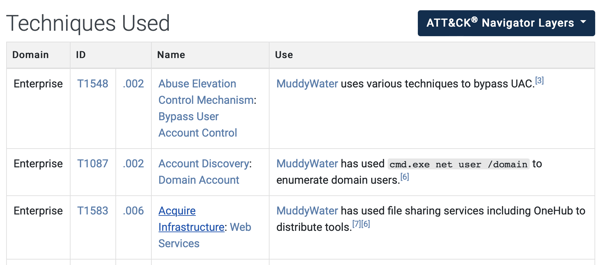
In addition, ATT&CK visualizes the techniques used by the group on the ATT&CK Navigator. To see techniques on the ATT&CK Navigator, click the “ATT&CK Navigation Layers” button on the group’s page. Blue techniques indicate the utilized techniques by the MuddyWater threat group.
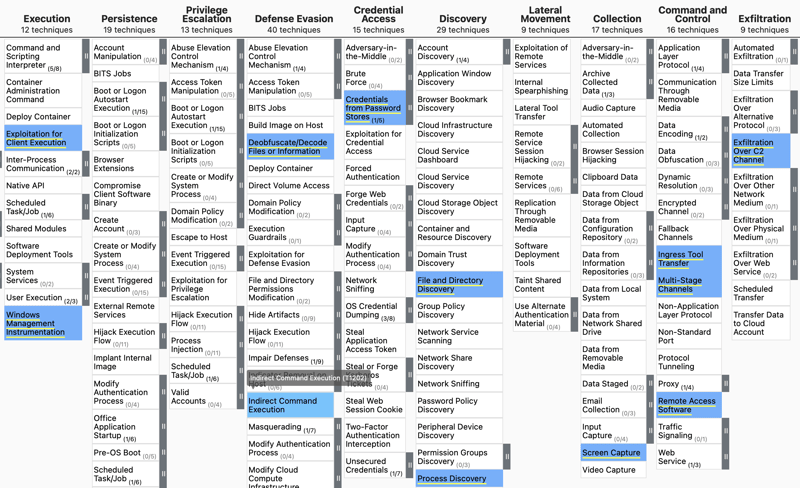
Currently, there are 129 groups in the ATT&CK Framework. They are threat groups, activity groups, or threat actors related to an intrusion activity and are tracked by a common name or names in the security community.
Level 2 Threat Intelligence
If your organization has a mid-level team with threat analysts, you can map threat intelligence to ATT&CK yourself rather than relying on what others have previously mapped as a next-level activity you may take. For example, if your organization has a report on an incident, this report can be an excellent internal source to map to ATT&CK. You can also utilize an external report, such as a blog post.
How to map a threat report to ATT&CK
Suppose you saw a blog about an emerging malware threat relevant to your organization. This blog can be a valuable threat intelligence resource for you. How can you map this malware analysis blog to MITRE ATT&CK? I’ll explain the mapping process in the following part of an actual blog:
The MITRE ATT&CK team suggests a step-by-step guide assist you with mapping a threat intelligence source to ATT&CK.
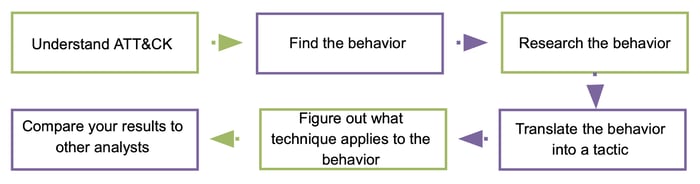
1. Familiarize yourself with the fundamentals of ATT&CK: tactics (the adversary's technical goals), techniques (how those goals are attained), and procedures (how those goals are implemented).
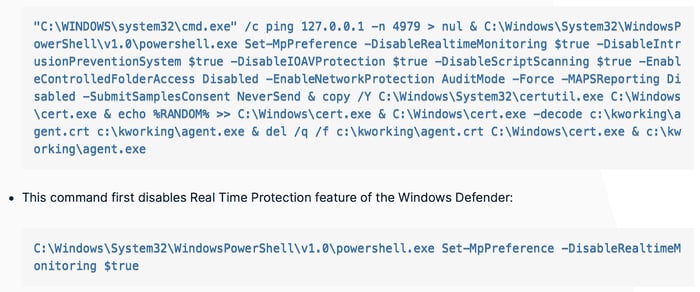
2. Find adversary behavior (TTPs) in the threat report. The TTP in the blog is “... disables Real Time Monitoring / Protection feature of the Windows Defender”.
3. Now, you should research the adversary behavior. If you're unfamiliar with the behavior, you may need additional research. A little investigation in our case reveals disabling Real-Time Protection impairs Windows Defender.
4. In the fourth step, you should translate the adversary behavior to an ATT&CK tactic. The good news is that Enterprise ATT&CK has only 14 tactics. As in the disabling Real-Time Protection example, disabling a security control would fall under the Defense Evasion tactic.
5. Now, you should figure out what technique applies to the behavior. This can be challenging, but you should be able to do it with your analytical skills and the ATT&CK website examples. The sub-technique “T1562.001 Impair Defenses: Disable or Modify Tools” appears when searching for “real-time monitoring” on the MITRE ATT&CK website. If you look at the technique description, you'll notice that this may be where the adversary behavior belongs.
6. The last step is “compare your results to other analysts”. Of course, your interpretation of behavior may differ from that of other analysts. If your adversary behavior to ATT&CK technique mapping is different from another analyst, you can discuss the difference.
By following the above steps, you determined that the adversary used the MITRE ATT&CK “T1562.001 Disable or Modify Tools” sub-technique under the “T1562 Impair Defenses” technique.
Level 3 Threat Intelligence
If your organization has an advanced Cyber Threat Intelligence (CTI) team, you can begin mapping additional data to ATT&CK and then use that data to prioritize how you defend. Using the steps outlined above, you can map both internal and external data to ATT&CK, such as incident response data, reports from OSINT or threat intel subscriptions, real-time alerts, and your company's historical data. After mapping out this information, you can compare threat groups and prioritize commonly used techniques.
You may then combine the data to discover the most regularly employed techniques, which will aid defenders in deciding what to focus on. This allows you to prioritize tactics and inform defenders about which ones they should concentrate on detecting and mitigating.








