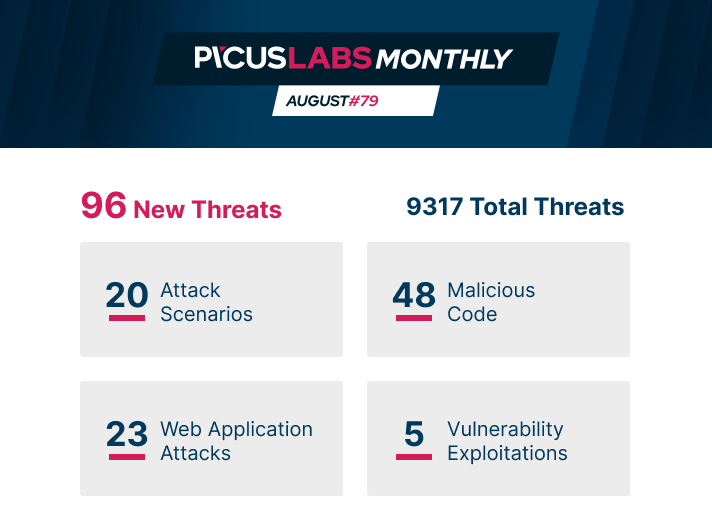
AUGUST'S THREAT: FASTCash 2.0 |
BeagleBoyz Threat Group Robbing BanksBeagleBoyz is a newly identified group that is responsible for attempting to steal nearly $2 billion from various financial institutions in coordinated cash-out attacks in over 30 countries worldwide. These cyber-enabled ATM cash-out campaigns were recognized openly as FASTCash. You can test the effectiveness of your security controls against the FASTCash campaigns with '265977 BeagleBoyzThreat Group FASTCash 2.0 Campaign Attack Scenario" in Picus Threat Library. You can also validate your defenses against PowerRatankba Trojan Downloader used in this attack campaign with threats 255145, 461582, and 66239 in Picus Threat Library. |
AUGUST'S THREAT ACTORS |
Transparent Tribe
DeathStalker
RedCurl
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques. Download Now: The Red Report: Your Handbook to Utilize MITRE ATT&CK Framework |
ATTACK SCENARIOS |
BeagleBoyz Threat Group FASTCash 2.0 CampaignPicus Threat ID: 265977ACTIONS 1. Display the Groups using "whoami /groups" Technique: T1033 System Owner/User Discovery Tactic: Discovery
2. Execute a Keylogger uses GetAsyncKeyState() Technique: T1056 Input Capture Tactic: Credential Access, Collection
3. Connect to RDP using mstsc.exe Technique: T1076 Remote Desktop Protocol Tactic: Lateral Movement ... 18. C2 Communicate Over HTTPS Port 443 Technique: T1043 Commonly Used Port Tactic: Command and Control Conni RAT ScenarioPicus Threat ID: 506809
ACTIONS 1. Copy Certutil.exe to TEMP by using Word Macro Technique: T1024 User Execution Tactic: Execution
2. Download First Stage Payload using Certutil.exe Technique: T1105 Remote File Copy Tactic: Command and Control, Lateral Movement 3. Create New Service for Persistence Technique: T1050 New Service Tactic: Privilege Escalation ... 7. Exfiltrate CAB File Over TCP Port 21 Technique: T1043 Commonly Used Port Tactic: Command and Control
Atomic AttacksAMSI Bypass via Obfuscated Powershell Reflection Method with WMF5 Autologging Bypass
For more information on MITRE ATT&CK T1562 Impair Defenses, here is the blog post you can read: MITRE ATT&CK T1562 Impair DefensesSecurity Support Provider Technique by using the ImplantSSP Tool
Credential Dumping by using the SharpKatz Tool
For more information on MITRE ATT&CK T1003 Credential Dumping, here is the blog post you can read:
|
MALICIOUS CODE |
|
Bisonal Backdoor Malware
M00nd3v Logger Infostealer Malware
MATA: Multi-platform targeted malware framework
Watch our webinar, we dig down into T1055 Process Injection as the no. 1 technique in the Picus 10 Critical MITRE ATT&CK Techniques list.
|
WEB APPLICATION ATTACKS |
|
Microsoft SharePoint DataSet/DataTable Remote Code Execution (RCE)
Apache Kylin Remote Code Execution (RCE)
Nagios Log Server 'username' Persistent Cross-Site Scripting (XSS)
|
VULNERABILITY EXPLOITATIONS |
|
Windows Setup Elevation of Privilege
Sudo PwFeedback Buffer Overflow Vulnerability
Windows Update Orchestrator Service Privilege Escalation
 |
SIGMA RULES |
|
System Information Discovery from Registry via PowerShell
In this webinar, Dr. Erdal Ozkaya from Standard Chartered Bank joined Picus for the webinar and we talked about T1082 System Information Discovery.
Suspicious Process Execution via WMI
Sandbox Evasion by Querying Debuggers
|