Security Control
Validation
Automatically and continuously validate the effectiveness of your prevention and detection controls.
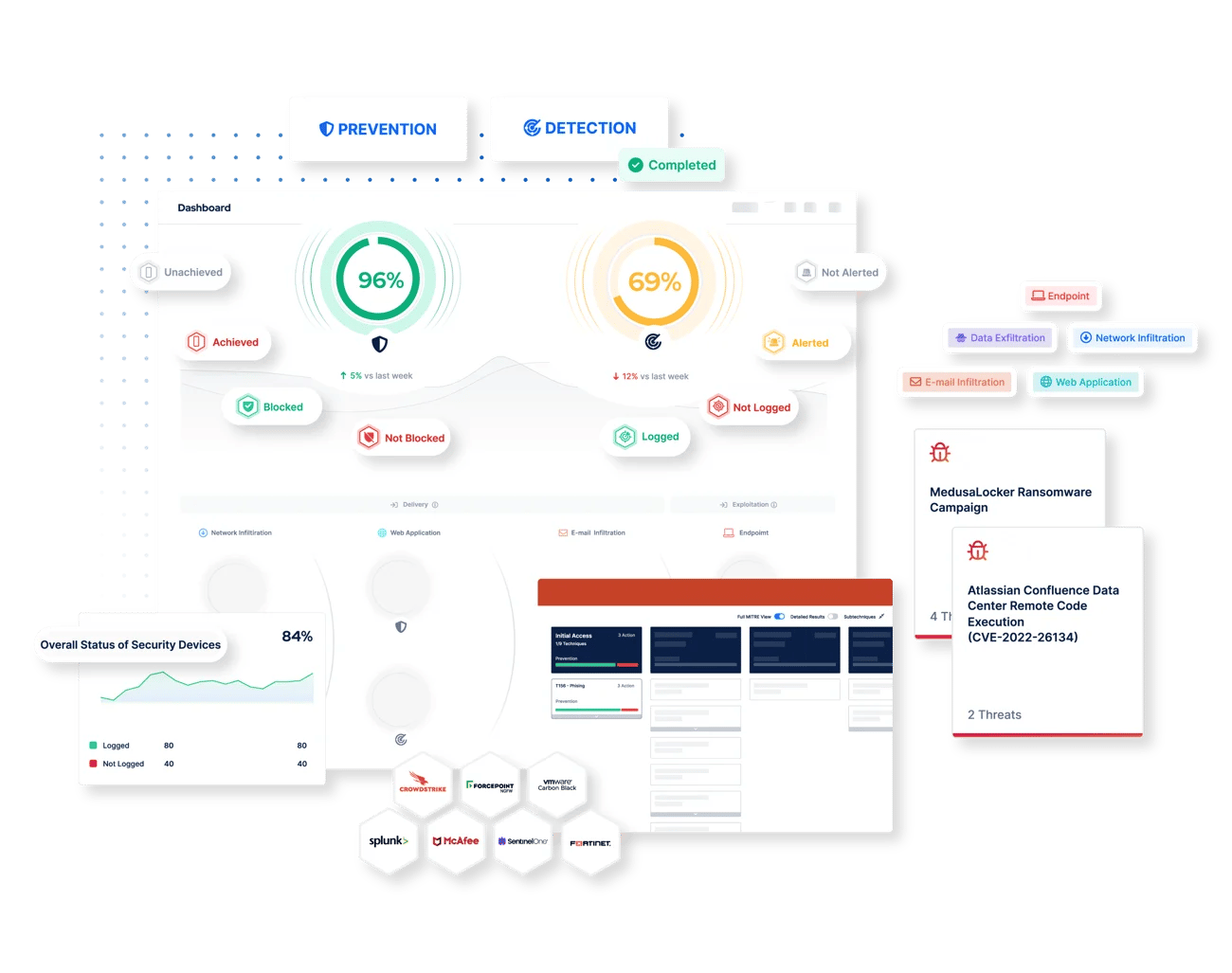
Validate and Optimize Your Defenses to Ensure You Stay Threat Ready
Your organization’s security controls are fundamental to your defense against cyber threats. But in a rapidly evolving landscape, are you sure that they are providing the level of protection you need to safeguard your most critical assets? To minimize the risk of serious breaches and demonstrate assurance, testing the performance of your controls on a regular basis is now considered vital.
Picus Security Control Validation (SCV), powered by award-winning Breach and Attack Simulation (BAS) technology, helps you to measure and strengthen cyber resilience by automatically and continuously testing the effectiveness of your security tools.
Why Security Control Validation?

Reasons to Choose The Picus Platform to Validate Your Existing Controls
.png?width=2000&name=An%20extensive%20library%20of%20real-world%20threats%20(2).png)
.webp?width=2000&name=Mitigate%20and%20optimize%20before%20a%20breach%20(2).webp)
.png?width=2000&name=Customizable%20threats%20and%20attack%20scenarios%20(2).png)
.png?width=2000&name=MITRE%20ATTACK%20Mapping%20(2).png)
.png?width=2000&name=Executive%20reports%20and%20dashboardsand%20(2).png)
With Picus SCV's Threat Builder, test your security controls against custom-created threats. This powerful feature enables security professionals without red teaming expertise to chain together attack actions and upload custom payloads.
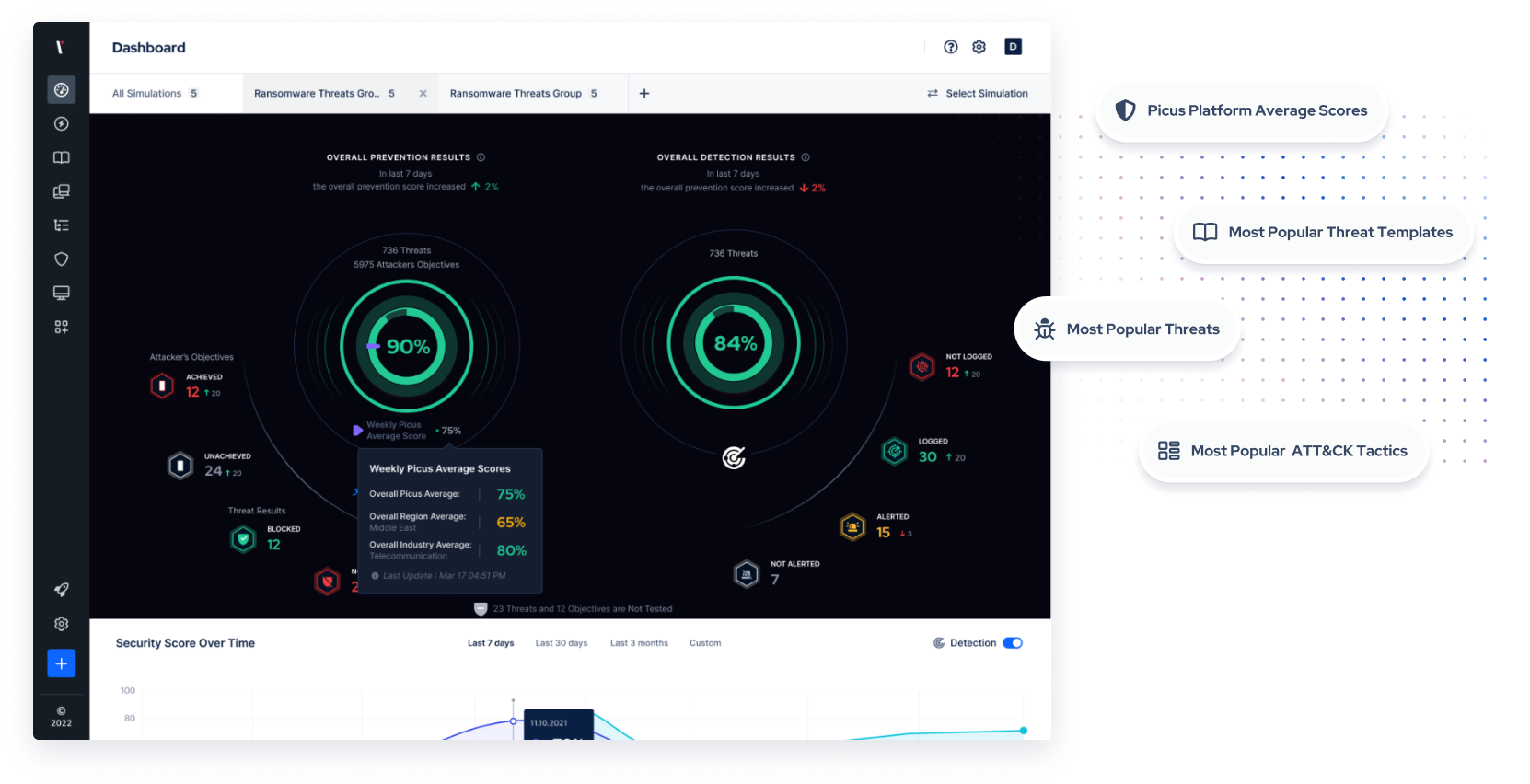
To help visualize threat coverage and visibility, Picus SCV automatically maps simulation results against The MITRE ATT&CK Framework. Quickly identify gaps and prioritize the mitigation of techniques that pose the greatest risk.
Quickly gauge your organization’s threat readiness and measure performance trends over time. Picus SCV includes automated reports and custom dashboards that enable you to stay on top of your security posture and keep stakeholders across your business informed.
Compare your security scores with industry peers, regional counterparts, and other Picus users. Gain insights into the most simulated threats, threat templates, and popular ATT&CK tactics within your region, industry, and Picus community. This allows you to better understand the prevalent threats and helps you prioritize your security efforts accordingly.
USE CASES
Address Challenges with Security Validation
See and prioritize exposures across your security operations.
Attack
Simulation
Simulate attacks to measure and optimize security controls.
Testing
Stay on top of exposures while alleviating manual testing requirements.
Validation
Improve decision making with a holistic view of your security posture.
Individually Licensable Attack Modules
Tests your controls against a regularly maintained attack library, comprising thousands of real-world threats and attack actions.
Web Application Attacks
OWASP Top 10 Attacks, XSS Evasion Attacks, XXE, SQL & PostgreSQL Injections, Command Injection, File Inclusion, Path Traversal, SSRF, CMS Attacks, HTTP Server Smuggling, Webshells, WAF Vendor Vulnerability Exploitation.
Realistic Network Traffic for APT Groups, Ransomware Download Threats, Malware Loaders, Infostealers, Remote Access Tools (RATs), Trojans, Backdoors, and more.
Ransomware & Malware Campaigns, Full Attack Killchain Coverage, APT & Threat Group Campaigns, Linux, macOS, and Windows Threats, DLL Side-Loading Attacks, Rootkits, Testing EDR, XDR, IDS, and AV Solutions.
File Formats (e.g., PDF, XLS(X), DOC(X), and more), Country-Specific, PII, PCI, Critical OS Data, Source Code Exfiltration, and more.
Gateway
Security
Malicious Links, Malicious Attachments, Executable Malicious Code, Rootkits, Cryptominer Threats, Botnets, Malware Droppers, and Loaders.
Filtering
Testing
Outbound HTTP Requests to Malicious URLs, Social Media URL Filtering, Dating & Travel Site URL Filtering, Malicious Command-and-Control, Malware, and Ransomware Site URL Testing.
Simulate, Mitigate, and Strengthen Your Defenses
Quickly identify your security gaps, simulate real-world threats, and instantly implement actionable mitigations with Picus Libraries.
Picus Threat
Library
Simulate real-world cyber attacks to test and validate the effectiveness of your security controls.
Picus Mitigation Library
Get actionable mitigations to proactively defend your organization against emerging threats.
What Our Customers Say
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer
The implementation was very fast, the platform is easy to integrate and results quite intuitive to be analyzed.
CIO
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated..
ICT Security Engineer
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist
With the help of this product we can perform continuosly endpoint attack via latest tactics and techniques which are used by threat actors..
Manager, IT Security and Risk Management
.. It is possible to customise the campaign or schedule the assessment periodically, to test protection measure implemented on network, endpoint and email.
ICT Security Engineer
Picus is such a great product for organizations that are looking to have constant checks and validation on their security posture in the organization.
Cybersecuirty Pre-sales Engineer
Picus is a real safety measurement tool. Ever since we took Picus into our inventory, Security has helped significantly to increase our maturity level.
Cyber Defense Senior Specialist
It strengthened our security perspective and allowed us to follow trend attacks. We can test zeroday malicious threats very early because Picus could add them their attack database quickly.
Security Specialist
Awarded By The Industry
Customer's Choice
2025 Gartner Peer Insights Voice of the Customer for Adversarial Exposure Validation
RESOURCES
Latest Security Control Validation Resources
.png?width=353&height=200&name=picus-cyber-fundamentals-BAS-ROI-CISOs-preview-march5%20(1).png)


.png?width=353&height=200&name=picus-cyber-fundamentals-BAS%20Services%20Explainedpreview-feb23%20(1).png)

.png?width=353&height=200&name=G2-DEC-badge-update-preview%20(1).png)



Validate Effectiveness Across Your Security Program
Validation
Enhance visibility of internal and external cyber assets and the security risks they pose.
Validation
Identify cloud misconfigurations and overly permissive identity and access management policies.
Validation
Measure and optimize the effectiveness of security controls with consistent and accurate attack simulations.
Validation
Eliminate high-risk attack paths that attackers could exploit to compromise users and assets.
Validation
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
Security control validation is a term used in cyber security to describe the testing of security controls. Security control validation enables security teams to understand whether the tools they use to prevent and detect threats are functioning as expected. With this knowledge, they can take action to address any gaps and achieve the best possible protection and value from investments.
Security control validation is essential because it helps security teams to identify policy weaknesses that could enable attacks to go unprevented and undetected. Security control validation ensures that defenses are optimized against evolving threats and that misconfigurations resulting from infrastructure drift are addressed before breaches occur.
Security control validation should be performed on a regular basis to ensure that prevention and detection gaps are identified and addressed swiftly. Automated security validation with Breach and Attack Simulation augments manual approaches such as pentesting to enable security teams to identify policy weaknesses continuously.
By continuously testing and helping to improve the effectiveness of security controls, Picus Security Control Validation Platform helps organizations to comply with a wide range of regulations and standards.
Laws such as The General Data Protection Regulation (GDPR) state that organizations should have a process for regularly testing, assessing and evaluating the effectiveness of technical and organizational measures. ISO-27001 and the PCI DSS, as well as frameworks such as NIST 800-53, also have similar requirements.
.png?width=161&height=136&name=gartner-logo-2025%201%20(1).png)
