SCV for
Detection Controls
Boost Detection Effectiveness. Increase your detection capabilities.
Get rid of false positives. Mitigate risks swiftly.
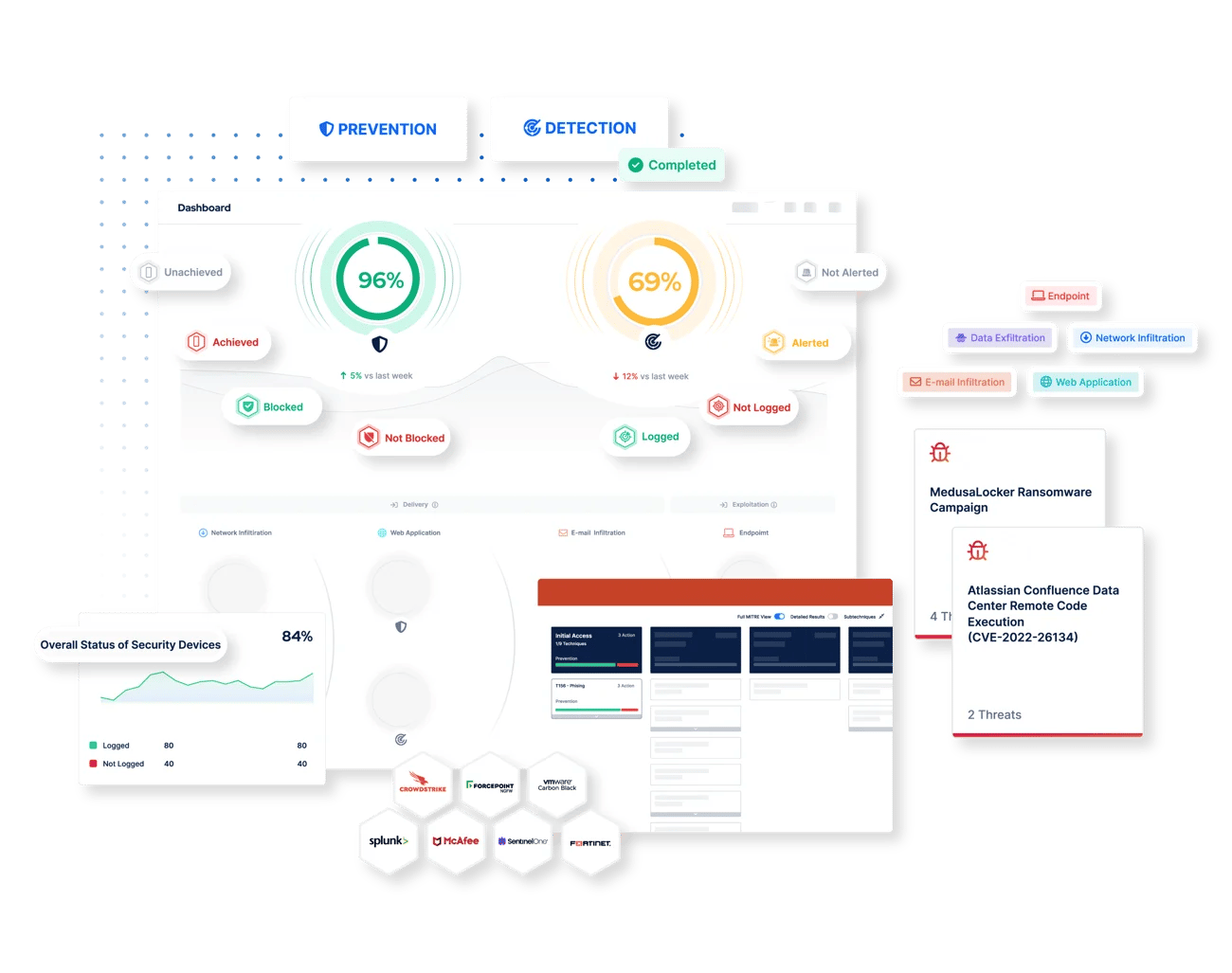
How The Picus Platform Optimizes Threat Prevention
Security Incident and Event Management (SIEM)
Alert Validation
In order to detect threats early and reduce attacker dwell time, it's also vital to ensure that appropriate SIEM correlation rules are in place to alert on the latest adversary behaviors. With the Picus Platform, quickly identify:
- Missing, redundant and obsolete rulesets
- Logged events that don't generate alerts
- Delays between security events and alert generation
Log Validation
Without the right data it's impossible to identify threat activity in your networks. By simulating real-world threats and analyzing the security logs captured by your SIEM, The Picus Platform enables you to:
- Determine in a timely fashion if logs from relevant sources are being ingested
- Understand and prioritize new data sources required to address logging gaps
- Ensure that logs contain the requisite level of data granularity
Endpoint Detection and Response (EDR)
Telemetry, Alert and Detection Rule Validation
Detecting and responding to attacks early in the cyber kill chain also relies on rich telemetry from endpoints. To facilitate the detection of threats that target your organization's devices, the Picus Platform integrates with leading EDR solutions to:
- Validate that the most relevant endpoint is being captured and analyzed
- Identify missing, redundant and obsolete rulesets and watch lists
- Measure the time between security events and alert generation
- Highlight behaviors that are detected but not blocked by prevention controls
Log Validation
Without the right data it's impossible to identify threat activity in your networks. By simulating real-world threats and analyzing the security logs captured by your SIEM, The Picus Platform enables you to:
- Determine in a timely fashion if logs from relevant sources are being ingested
- Understand and prioritize new data sources required to address logging gaps
- Ensure that logs contain the requisite level of data granularity
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
