MAY'S THREAT: MAZE |
The Rise of Maze RansomwareUnfortunately, Maze ransomware has been in the news quite often in the last months. In May, the Maze ransomware gang have started posting payment card data stolen during a breach at state-owned Banco de Costa Rica. The data leak, which consists of a 2 GB CSV file containing details of various Mastercard and Visa credit or debit cards, has been verified by security researchers. The recent Maze ransomware attack on tech major Cognizant Technology Solutions hurt the company's revenues and corresponding margins by $50-$70 million. Lastly, nuclear missile contractor Westech has been breached by the Maze gang.
You can test the effectiveness of your security controls against Maze ransomware with '390945 Maze Ransomware Scenario' in Picus Threat Library. |
MAY'S THREAT ACTORS |
Lazarus Group
Naikon
Hangover
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques. Download Now: The Red Report: Your Handbook to Utilize MITRE ATT&CK Framework |
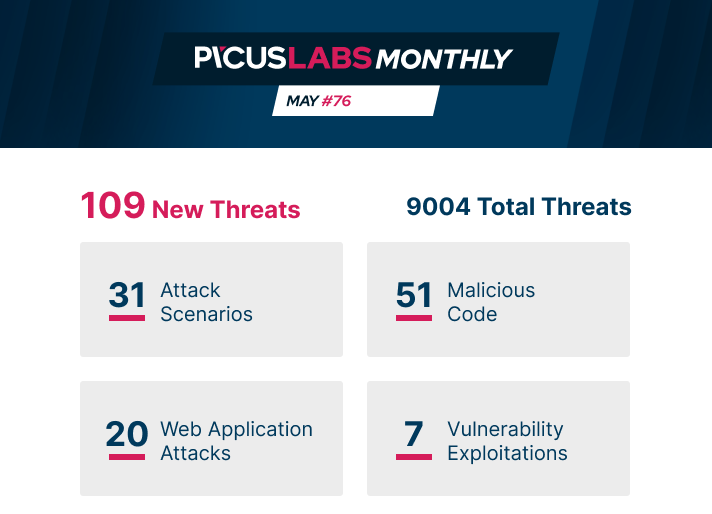
ATTACK SCENARIOS |
APT29 Threat GroupPicus Threat ID: 647501ACTIONS 1. Execute Invoke-UserHunter Function (PowerView) Technique: T1087 Account Discovery Tactic: Discovery
2. Display the names of all network shares using "net share" command Technique: T1049 System Network Connections Discovery Tactic: Discovery
3. Kerberoasting Attack by using Invoke-Kerberoast Technique: T1028 Kerberoasting Tactic: Credential Access ... 8. C2 Communicate Over HTTPS Port 443 Technique: T1043 Commonly Used Ports Tactic: Command and Control Maze RansomwarePicus Threat ID: 390945
ACTIONS 1. Delete Shadow Copy using Windows Management Instrumentation (WMI) Technique: T1490 Inhibit System Recovery Tactic: Impact
2. Connect to RDP using mstsc.exe Technique: T1076 Remote Desktop Protocol Tactic: Lateral Movement 3. Gather credentials using Mimikatz Tool Technique: T1003 Credential Dumping Tactic: Credential Access ... 9. Disable Automated Windows Recovery Features Technique: T1490 Inhibit System Recovery Tactic: Impact
Atomic AttacksProcess Injection by using EtwpCreateEtwThread Function
Dism.exe OS Binary (Lolbas) used in Signed Binary Proxy Execution
Session File Dumping by using Sessionsearcher Tool
|
MALICIOUS CODE |
|
Pwndlocker Ransomware
Aria-body Backdoor
Dacls Remote Access Trojan
|
WEB APPLICATION ATTACKS |
|
Pulse Secure SSL VPN Command Injection
Microsoft SharePoint Remote Code Execution
Django GIS Functions SQL Injection
|
VULNERABILITY EXPLOITATIONS |
|
Google Chrome WebAudio UAF
Exim Privilege Escalation
Windows Installer Elevation of Privilege
 |
SIGMA RULES |
|
Windows Hash Database Files Dumping via Volume Shadow Copy
DLL Injection with PowerShell
Proxy Execution of Application
|




