As a security professional, you know better than anyone about the dangers of harmful online content. But you’ll also know that relying on user education alone to mitigate your organization’s cyber risk is not enough. It’s why supporting controls to prevent employees from knowingly and unknowingly accessing malicious websites and content that violates your internet usage policy is also essential.
By blocking inbound and outbound communications requests, firewalls and secure web gateways are an important line of defense against threats such as spoof websites, drive-by downloads, and command and control activity (c2). Constant changes in the threat landscape and within your IT environment can make it challenging to keep these controls optimized, however.
URL Filtering, a new attack module offered as part of Picus Security Control Validation (SCV), enables you to alleviate the effort required to keep controls working optimally by simulating outbound HTTP/S requests to harmful and objectionable websites. In doing so, it validates that your prevention capabilities are functioning as they should and highlights coverage gaps so you can address them quickly.
Validate the effectiveness of your prevention controls to block URL filtering attacks.
Divided across 29 URL categories, URL Filtering simulates hundreds of pre-set URLs - all carefully selected by Red and Blue Teamers at Picus Labs based on the risk they pose to organizations. Categories include Hacking, Phishing, Piracy, Gambling, Torrents, and more. Have your own set of URLs that you’d like to test? No problem. Simply enter your list and set simulations to run on a regular basis.
Validate your controls against the latest attacks
Picus URL filtering is the latest of six individually licensable Attack Modules available as part of SCV. From infiltration to exfiltration, validating your prevention and detection capabilities against adversary techniques used across the cyber kill chain is quick and straightforward - all via one unified platform powered by Picus’ pioneering Breach and Attack Simulation technology.
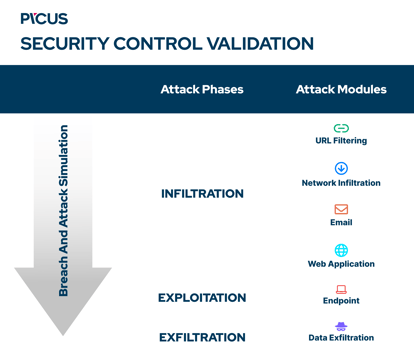
So you can keep defenses optimized against emerging threats, The Picus Security Validation Platform offers a rich Threat Library that includes over 5,000 threats and 22,000 TTPs. New emerging threats with actionable IOCs are added within 24-hours and at no additional cost. Support for the latest security technologies, AI-driven threat profiling, and actionable mitigation recommendations - including vendor-specific signatures and detection rules - provide the flexibility, guidance and content you need to not only validate controls but also keep them optimized with less manual effort.
Learn more about security control validation
Constant configuration and optimization of your security controls can be a considerable time and resource drain, but with Picus, get the insights you need to ease the strain and be confident that your defenses are ready to prevent and detect the latest threats.
To learn more about URL Filtering or any of the other Attack Modules offered as part of the Picus Security Validation Platform, please reach out to a member of our team or submit a demo request.




