.png?width=2000&name=Quantify%20Cyber%20Risk%20(1).png)
Quantify Cyber Risk
Simulate real-world attacks to measure effectiveness across your security operations, gauge threat readiness, and prove your security posture to business leaders.
Measure your threat readiness, make prioritized decisions, and strengthen your resilience in the areas that matter most.
Simulate attacks to measure and optimize security controls.
Stay on top of exposures while alleviating manual testing requirements.
Improve decision making with a holistic view of your security posture.
.png?width=1530&height=813&name=BlackHat-Homepage-Visual%20(1).png)
📅 Date: August 3-8, 2024
📍 Location: Mandalay Bay, Las Vegas, NV
Visit us at Booth #2715 to discover how Picus Security can help you stay ahead of cyber threats. Don't miss our live demos and expert talks!
.png?width=2000&name=Quantify%20Cyber%20Risk%20(1).png)
Simulate real-world attacks to measure effectiveness across your security operations, gauge threat readiness, and prove your security posture to business leaders.
.png?width=2000&name=Reduce%20Threat%20exposure%20(1).png)
Make prioritized security decisions with validation insights enriched with the latest asset, vulnerability and cyber threat intelligence.
.png?width=2000&name=Amplify%20Team%20Impact%20(1).png)
Automate manual tasks to validate your security at scale. Address threat coverage gaps and misconfigurations with actionable mitigations.
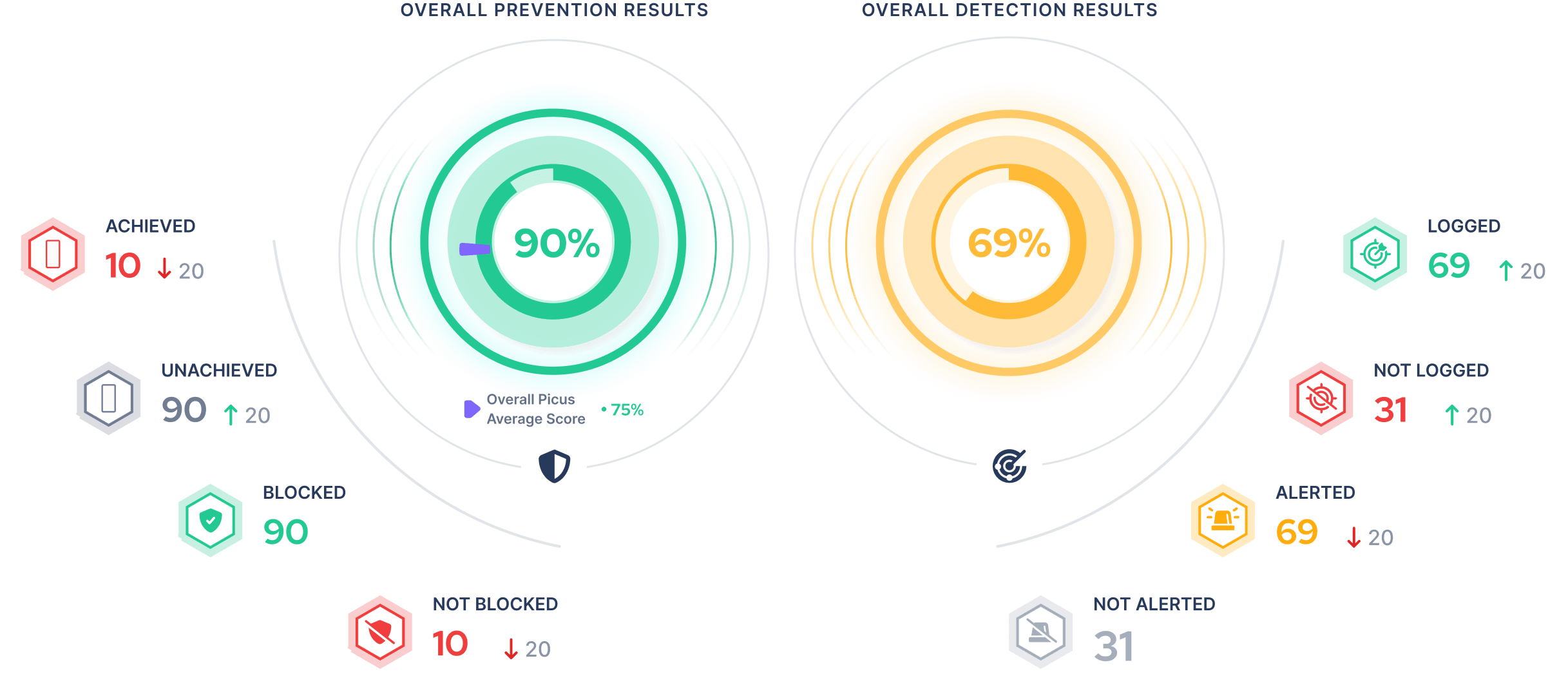
Measure and optimize the effectiveness of your prevention and detection controls with consistent and accurate attack simulations.
Discover high-risk attack paths evasive attackers could exploit to move through your internal network and achieve their objectives.
Maximize detection efficacy with insights about the performance of your SIEM detection rules and the threat coverage they provide.
Get a consolidated view of your internal and external assets, including security and compliance-related insights about the risks they pose.
Identify cloud misconfigurations and overly permissive identity and access management policies that weaken the security of your data and workloads in the cloud.
percent of Gartner® Peer Insights™ reviewers recommend Picus.
organizations and counting trust our platform globally.
threats simulated consistently and accurately.
percent average increase in prevention capability in 3 months.









.png?width=3200&height=323&name=Pattern(1).png)
Submit a request and we'll share answers to your top security validation and exposure management questions.
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.

What Our Customers Say
''Although we always used pen-test and other assessment practices, none of them gave us the depth and width we need to understand our security posture against the possible attack scenarios extensively. The Picus Platform was a game changer.''

The right hand of our security team
''The Picus Platform is an easy to use solution that helps us ensure our defenses keep pace with evolving threats.
Picus has become the right hand of our security team.''

Best choice for attack simulation
''With an expert support team, fully automated attacks, and detailed dashboards, The Picus Platform is the best choice for attack simulation.''
