CVE-2023-27350 PaperCut Vulnerability Exploited by Bl00dy Ransomware - CISA Alert AA23-131A
On May 12th, 2023, The Cybersecurity and Infrastructure Security Agency (CISA) released a joint advisory on an actively exploited critical vulnerability found in PaperCut [1]. CVE-2023-27350 is a zero-day vulnerability affecting over 100 million users worldwide, and it is exploited by a ransomware group named, Bl00dy.
In this blog, we explain how the PaperCut RCE vulnerability works and how Bl00dy ransomware exploits the CVE-2023-27350 vulnerability.
Simulate Vulnerability Exploitation Attacks with 14-Day Free Trial of Picus Platform
What is PaperCut CVE-2023-27350 Remote Code Execution Vulnerability?
PaperCut is a popular printer management software that is used by more than 70000 organizations and has more than 100 million users worldwide. In March 2023, PaperCut reported a critical zero-day vulnerability affecting their PaperCut NG and MF products. CVE-2023-27350 is a remote code execution vulnerability and has a CVSS score of 9.8 (Critical). When exploited, the CVE-2023-27350 vulnerability allows adversaries to run arbitrary commands through the built-in scripting interface of PaperCut. This command execution runs with SYSTEM privileges and does not require authentication. The affected versions of PaperCut are given below.
|
Product Name |
Vulnerable Version |
Fixed Version |
|
PaperCut MF PaperCut NG |
version 8.0.0 to 19.2.7 version 20.0.0 to 20.1.6 version 21.0.0 to 21.2.10 version 22.0.0 to 22.0.8 |
version 20.1.7 version 21.2.11 version 22.0.9 version 22.0.10 version 22.0.11 |
PaperCut CVE-2023-27350 Exploit - How Does It Work?
During the initial setup of PaperCut, users are asked to create an admin user and configure the service. After the setup is completed, users are taken to a page named "SetupCompleted". This page has a "Login" button that takes the user to the Dashboard of PaperCut service.
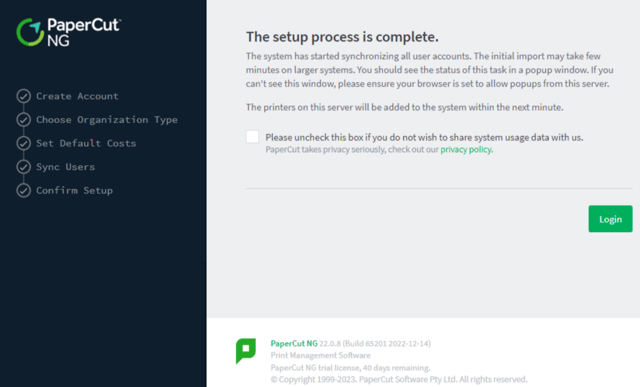
Figure 1: SetupComplete page in PaperCut NG [2]
In vulnerable PaperCut versions, the improper access controls in the SetupCompleted class result in a vulnerability. Adversaries can directly visit the "SetupComplete" page and bypass the authentication by clicking the "Login" button. After bypassing the authentication, threat actors can use the scripting feature of PaperCut to execute commands with SYSTEM privileges.
CVE-2023-27350 vulnerability is fairly easy to identify and exploit. That's why the vulnerability has a CVSS score of 9.8 (Critical). A quick Shodan search shows that more than 1800 PaperCut servers are publicly exposed, which makes them a potential target for adversaries. Organizations are advised to patch their vulnerable PaperCut services as soon as possible.
Bloody Ransomware Group
In their advisory, CISA stated that an opportunistic ransomware group named Bl00dy exploits the vulnerable PaperCut services operated by educational institutions. Bl00dy ransomware gang began their operations in May 2022 by targeting healthcare organizations in New York. Compared to other ransomware groups, Bl00dy appears to conduct their ransomware operations manually and does not develop their own ransomware independently. Instead, Bl00dy uses leaked ransomware builders and source codes of other ransomware payloads such as Babuk and Conti. In September 2022, Bl00dy ransomware group came up with a new ransomware variant that uses the leaked LockBit 3.0 ransomware builder. In their recent attack campaign, Bl00dy uses LockBit 3.0 encryptors and appends victims' encrypted files with ".bl00dy" extension.
How Picus Helps Simulate PaperCut CVE-2023-27350 RCE Vulnerability Exploitation Attacks?
We also strongly suggest simulating CVE-2023-27350 vulnerability exploitation attacks to test the effectiveness of your security controls against real-life cyber attacks using the Picus The Complete Security Validation Platform. You can also test your defenses against hundreds of other vulnerability exploits, such as Follina, Log4Shell, and ProxyShell, within minutes with a 14-day free trial of the Picus Platform.
Picus Threat Library includes the following threats for CVE-2023-27350 vulnerability exploitation attacks:
|
Threat ID |
Threat Name |
Attack Module |
|
48294 |
PaperCut Web Attack Campaign |
Web Application |
Picus Threat Library includes the following threats for Bl00dy ransomware attacks:
|
Threat ID |
Threat Name |
Attack Module |
|
87436 |
Bl00dy Ransomware Download Threat |
Network Infiltration |
|
51318 |
Bl00dy Ransomware Email Threat |
Email Infiltration (Phishing) |
Picus also provides actionable mitigation content. Picus Mitigation Library includes prevention signatures to address LockBit ransomware and other ransomware attacks in preventive security controls. Currently, Picus Labs validated the following signatures for PaperCut CVE-2023-27350 Vulnerability and Bl00dy ransomware:
|
PaperCut CVE-2023-27350 Vulnerability Mitigation Signatures |
||
|
Security Control |
Signature ID |
Signature Name |
|
F5 BIG-IP ASM |
200003443 |
Java code injection - Runtime.getRuntime (Parameter) |
|
FortiGate IPS |
12449 |
backdoor: Remote.CMD.Shell |
|
ModSecurity |
944100 |
Remote Command Execution: Suspicious Java class detected |
|
ModSecurity |
944130 |
Suspicious Java class detected |
|
ModSecurity |
944250 |
Remote Command Execution: Suspicious Java method detected |
|
PaloAlto IPS |
93750 |
PaperCut MG and NG Remote Code Execution Vulnerability |
|
Bl00dy Ransomware Mitigation Signatures |
||
|
Security Control |
Signature ID |
Signature Name |
|
Check Point NGFW |
0A700F738 |
Ransomware.Win32.Stealer.TC.5fb1pDOc |
|
Forcepoint NGFW |
|
File_Malware-Blocked |
|
Fortigate AV |
8273597 |
W32/Conti.F!tr.ransom |
|
McAfee IPS |
0x4840c900 |
MALWARE: Malicious File Detected by GTI |
|
SourceFire IPS |
W32.Auto:139a8b.in03.Talos |
|
Start simulating emerging threats today and get actionable mitigation insights with a 14-day free trial of Picus The Complete Security Validation Platform.
References
[1] "Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG," Cybersecurity and Infrastructure Security Agency CISA. [Online]. Available: https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-131a. [Accessed: May 12, 2023]
[2] "Critical Vulnerabilities in PaperCut Print Management Software." [Online]. Available: https://www.huntress.com/blog/critical-vulnerabilities-in-papercut-print-management-software. [Accessed: May 12, 2023]








