How to Leverage the MITRE ATT&CK Framework for Purple Teaming
Suleyman Ozarslan
April 19, 2022
While red and blue teaming are well-established notions in cybersecurity, a more collaborative approach – purple teaming – has emerged in recent years. A red team is an offensive team that assesses the effectiveness of the organization’s defensive capabilities and identifies cybersecurity gaps by thinking and acting like attackers. A blue team is a defensive team that detects and blocks cyberattacks using defensive technologies, strategies, and tactics. Purple teaming is maximizing the efficacy of the red and blue teams by merging the defensive strategies and tactics of the blue team with the knowledge of cybersecurity gaps identified by the red team into a coherent narrative. As a result, the purple teaming approach continuously improves the organization's cyber resilience against cyber threats.
Our previous blog describes red team, blue team, and purple teaming concepts in detail. This blog aims to explain how organizations utilize the MITRE ATT&CK framework to perform purple teaming exercises with examples.
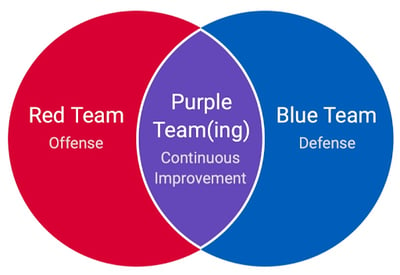
Purple Team - A Dedicated Team or a Function?
Although a separate team comes to mind when the “purple team” concept is mentioned, the purple team doesn’t need to take place as a dedicated team. A purple team is a function that helps an organization's red and blue teams share information and work together more effectively. However, some mature organizations may prefer to utilize a dedicated unit for the purple teaming function.
How to Build a Purple Team Engine
Learn how Picus can help you operationalize threat intelligence for continuous purple teaming?
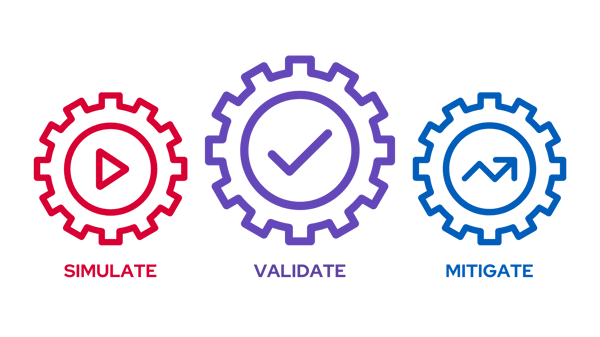
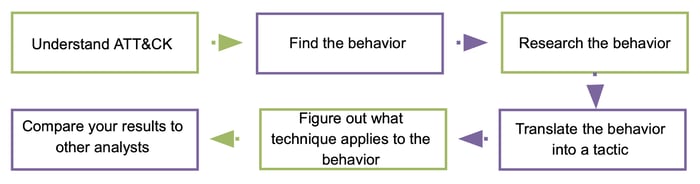
Organizations can build a purple team engine in three steps, as shown in the above figure.
Step 1 - Simulate: In this step, red teams assess the effectiveness of an organization's defenses by emulating/simulating adversary Tactics, Techniques, and Procedures (TTPs). Therefore, red teams simulate adversary attacks and assess the organization's security posture.
Step 2 - Validate: Red teams analyze simulation results and inform blue teams about successful/unsuccessful attacks and gaps found in the organization’s defenses in this step. Blue teams understand the adversary TTPs with the help of red teams and measure the security controls’ coverage of individual attack techniques and attack campaigns of threat actors. Therefore, cooperation between red and blue teams is essential in this step.
Step 3 - Mitigate: In this step, blue teams address the gaps found in the previous step, such as prevention gaps, logging gaps, and detection gaps. They mitigate identified cybersecurity risks by utilizing defensive technologies, strategies, and tactics. Moreover, blue teams inform red teams about counter-defense against simulated attacks to enable red teams to enhance their attacks in response to blue teams’ defenses.
The following sections will explain how organizations can build a purple team engine by leveraging the MITRE ATT&CK Framework.
STEP 1 - SIMULATE
Red teams evaluate the organization's defense efficacy in this step by simulating adversary TTPs. This step includes two operations:
-
Threat Intelligence
-
Attack Simulation / Adversary Emulation
Threat Intelligence
Regardless of the maturity level of cybersecurity teams, ATT&CK can help any organization with threat intelligence. The MITRE ATT&CK team has determined the following maturity levels:
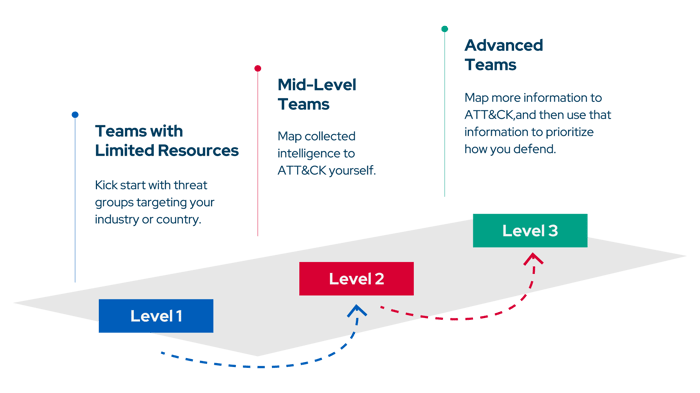
Level 1 Threat Intelligence
If your organization has limited human resources for threat intelligence, you can start with a single threat group targeting your organization’s industry and/or country. Then, you can look at the techniques used by the threat group.
Example - Level 1 Threat Intelligence with ATT&CK
Assume you work for a US telecommunications company. Let's search for "telecommunications" on the MITRE ATT&CK homepage.
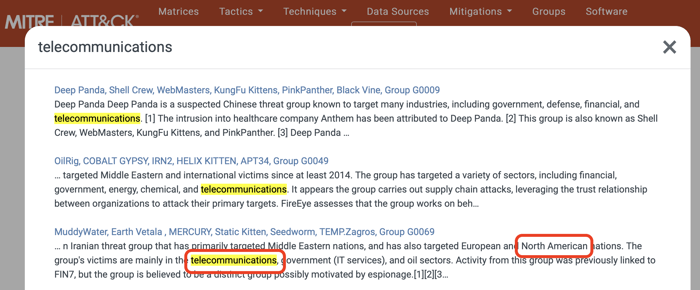
You will find several threat groups targeting our sector. For example, the MuddyWater group targets the telecommunications sector in North America. So, this group is very relevant to your organization. You can start with MuddyWater. Let's go to the MuddyWater page by clicking on the link.
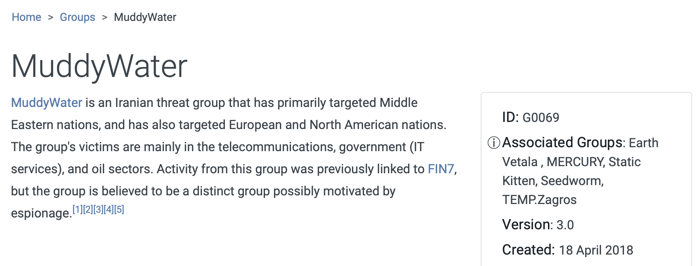
As seen on the page, ATT&CK provides attribution of the group, targeted geographies, and targeted sectors. You can learn more about the group by looking at their techniques. ATT&CK covers techniques used by each threat group.
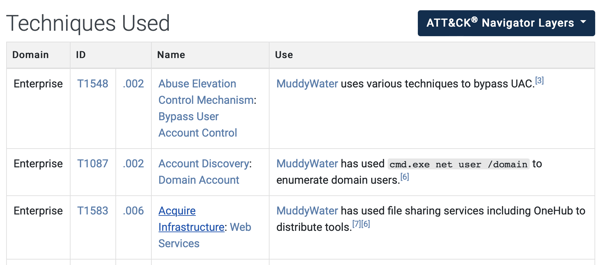
Level 2 Threat Intelligence
If your organization has a mid-level team with threat analysts, you can map threat intelligence to ATT&CK yourself rather than relying on what others have previously mapped as a next-level activity you may take.
How to map a threat report to ATT&CK
Suppose you saw a blog about an emerging malware threat relevant to your organization. This blog can be a valuable threat intelligence resource for you. How can you map this malware analysis blog to MITRE ATT&CK? The MITRE ATT&CK team suggests the following steps for mapping a threat intelligence source to ATT&CK.
Please read the “How to Leverage the MITRE ATT&CK Framework for Threat Intelligence” article for a detailed explanation of these steps with examples.
Level 3 Threat Intelligence
If your organization has a proficient CTI team, you may start mapping new data to ATT&CK and use it to prioritize your defenses. Internal and external data sources can be mapped to ATT&CK using the above steps. Then you can compare threat groups and prioritize common techniques.
The data can then be combined to reveal the most frequently used techniques, helping defenses focus their efforts. This lets you prioritize techniques and inform defenders which ones they should concentrate on detecting and mitigating.
Learn how Picus can help you operationalize threat intelligence for continuous purple teaming?
Attack Simulation / Adversary Emulation
Since you have threat intel -information about adversaries and their tactics, techniques, and procedures (TTPs)- the next step is challenging your defensive security controls against these adversary TTPs.
You should assess how your defenses currently stack up to cyberattacks with two methods:
-
Atomic Tests: Testing a specific security control against a particular technique.
The MITRE ATT&CK team proposes the following cycle for atomic tests [1].
.webp)
1. Choose an ATT&CK technique.
2. Choose a test for that technique.
3. Perform an attack simulation by executing the test procedure.
4. Identify gaps in your defense by analyzing your detections of the procedure.
5. Improve your defenses to close identified gaps.
After mitigation, you can go step 1 and choose a new ATT&CK technique.
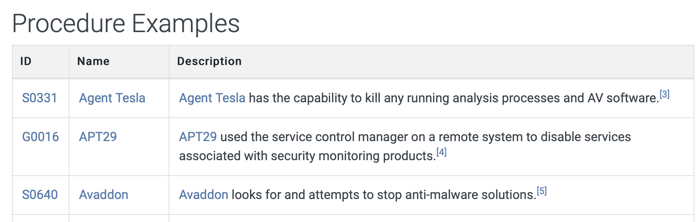
In order to create test procedures, you can use description and procedure examples and their references on the technique’s page. However, they may not be specific enough to construct a test procedure.
-
Attack Scenario Tests: Testing multiple security controls with sequentially executed multiple adversary TTPs consisting of all phases of an adversary attack lifecycle. This option is more complicated and requires several teams to work together. Picus Labs suggests the following cycle for the attack scenario tests.
-2.png?width=700&height=203&name=image%20(2)-2.png)
1. Pick a threat group or malware family targeting your organization, its region, or industry. First, you should choose an ATT&CK technique.
2. Collect all available malware samples and threat intelligence for the selected threat group. To get the complete picture, CTI teams should work on the threat intelligence and combine what they have with what MITRE ATT&CK provides and what is publicly available. Then, identify techniques in collected threat intel and analyze malware samples.
3. Analyze adversary behavior to create their operational flow, a sequence of specific procedures used by the adversary to use the identified techniques, namely adversary attack scenario.
4. Perform an attack simulation by executing the attack scenario.
5. Identify gaps in your security controls and improve your defenses to close the gaps.
STEP 2 - VALIDATE
The second step of an effective purple teaming exercise is to validate your security controls against cyberattacks.
-
Once you have simulated an attack technique (atomic test), you can figure out your coverage of that technique.
-
Once you have simulated an attack scenario, you can determine your coverage of a threat group or malware family.
MITRE ATT&CK suggests that you focus on the following gaps and measure the coverage:
-
Logging gap: You are not currently pulling required logs from the right data sources, which indicates a logging gap.
-
Detection gap: You have needed logs, but your analytics can’t detect the attack technique.
Or, your existing analytics detects the technique, which means there is no gap.
The ATT&CK Navigator tool of MITRE can help you visualize your logging and detection coverage on the MITRE ATT&CK matrix. By assigning different color codes, you can build a heat map that can help you identify your priorities for the next stage of the process, which is the mitigate step.
An example is shown in the below figure.
-
White: You have not tested the technique, which indicates an assessment (simulation) gap.
-
Red: You don’t have logs to detect the technique - a logging gap.
-
Orange: Logs exist, but you don’t have any detection rule to detect the technique - a detection gap.
-
Green: You have the required logs and the detection mechanisms in place to detect the technique - no gap.
.png?width=700&height=488&name=unnamed%20(6).png)
STEP 3 - MITIGATE
The final step of an effective purple teaming exercise is to mitigate by addressing the gaps found in the validate step.
Assessment Gaps
Techniques that have not yet been simulated lead assessment gaps. If there were no time, tools, or people to simulate a technique, that leaves a vacuum in our understanding. You may need to get together the right tools and people to simulate ATT&CK techniques.
Logging Gaps
How do we observe a given technique? In other words, which data sources do we need to observe a technique properly? Once the suitable log sources are identified via the gap analysis, organizations should start collecting those logs and ensure that required logs are collected, and no infrastructural failures stop that flow.
The MITRE ATT&CK Framework provides “data sources” to help identify the required log sources to detect a technique [2]. ATT&CK defines data sources as a source of information obtained by a sensor or logging system that can be used to identify an adversary's activities or the outcome of those activities. For example, data sources provided for the T1562.001 Impair Defenses: Disable or Modify Tools sub-technique [3] are shown in the below screenshot:
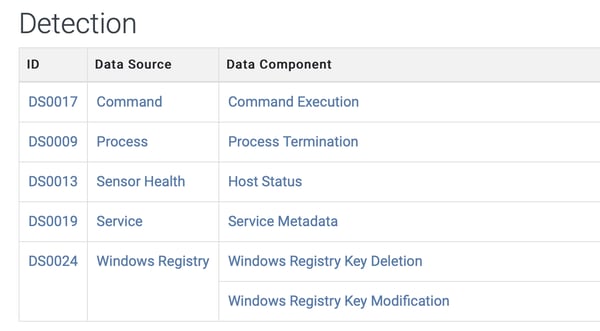
The MITRE ATT&CK framework also provides “data components”. They bring an additional sub-layer of context to data sources and narrow the identification of security events. For example, “Active Directory: Active Directory Object Access” means that the data source is “Active Directory” and the data component is “Directory Object Access”.
Detection Gaps
On the detection gaps, detection rules need to be developed and revised against false positives, and you must ensure that they detect malicious behavior as they are supposed to.
ATT&CK provides information on the details of the technique, but you need to research further to identify the specific procedures used. For example, API call names used in a process injection attack are given the MITRE ATT&CK Process Injection page, in the example below, for the DLL Injection technique [4].
.png?width=600&height=230&name=unnamed%20(8).png)
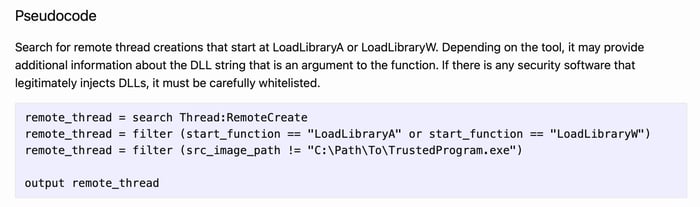
The MITRE Cyber Analytics Repository (CAR) [5] is a great place to start developing detection rules. CAR defines a data model used to generate pseudocode detection rule representations and offers implementations for specific tools such as Splunk and EQL. CAR is intended to provide a set of validated and well-explained analytics for covered techniques. For example, pseudocode to detect DLL Injection via Load Library technique provided by MITRE CAR is shown below.
References
[1] B. Strom, “Getting Started with ATT&CK: Adversary Emulation and Red Teaming,” MITRE ATT&CK®, Jul. 17, 2019. https://medium.com/mitre-attack/getting-started-with-attack-red-29f074ccf7e3.
[2] “Data Sources.” [Online]. Available: https://attack.mitre.org/datasources/.
[3] “Impair Defenses: Disable or Modify Tools.” Available: https://attack.mitre.org/techniques/T1562/001/.
[4] “Process Injection.” https://attack.mitre.org/techniques/T1055/
[5] The MITRE Corporation, “Welcome to the Cyber Analytics Repository,” MITRE Cyber Analytics Repository. https://car.mitre.org/.



