AI-Driven Security Validation
Leverage AI to transform how you detect, validate, and prioritize threats.
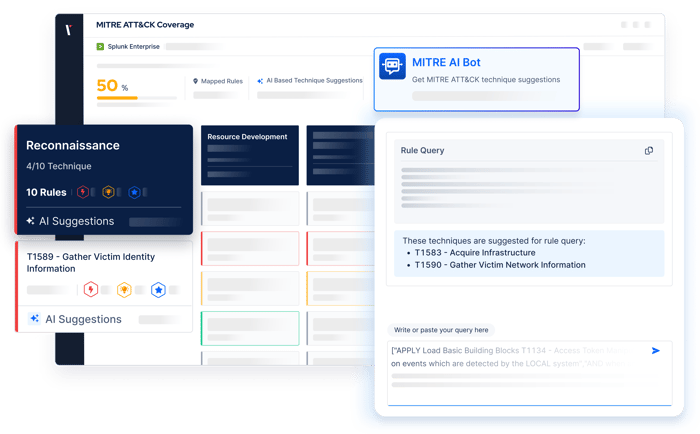
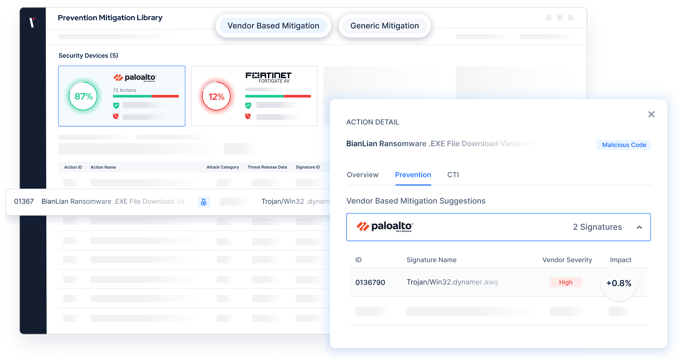
- Generate attack scenarios from any threat intelligence report using AI-driven automation.
- Continuously learn from validation data to refine detection logic and improve defense performance.
- Focus analyst effort where AI-powered analysis proves the greatest impact.




.png?width=680&height=395&name=AI%20smart%20assistant%20(5).png)

.png?width=3200&height=323&name=Pattern(1).png)