Cloud Security Validation
Extend security validation to the cloud with automated cloud assessment and attack simulation.
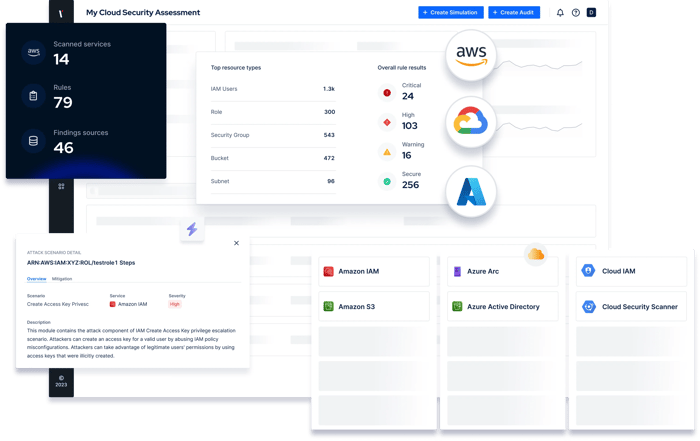
Identify Cloud Security Issues Before They Lead To Critical Incidents
Migration of workloads to the cloud continues to increase the challenge of defending against the latest threats.
Picus Cloud Security Validation (CSV) helps security teams keep pace with cloud security posture management by identifying common cloud misconfigurations and overly permissive IAM policies - the two primary causes of cloud data breaches.
How Picus Strengthens Your Cloud Security
Due to the rapid pace of digital transformation, the complexity of cloud environments, and human error, critical cloud security gaps can arise daily. Picus Cloud Security Validation helps you quickly identify and address cloud security exposures to achieve a proactive approach to cloud security posture management (CSPM) and cloud infrastructure entitlement management (CIEM.)
Secure Services Across Cloud Environments and Containers
Picus Cloud Security Validation provides the support you need to secure workloads across Amazon Web Service (AWS), Microsoft Azure (Azure) and Google Cloud Platform (GCP).

Get the Insights You Need To Address Cloud Security Risks Proactively
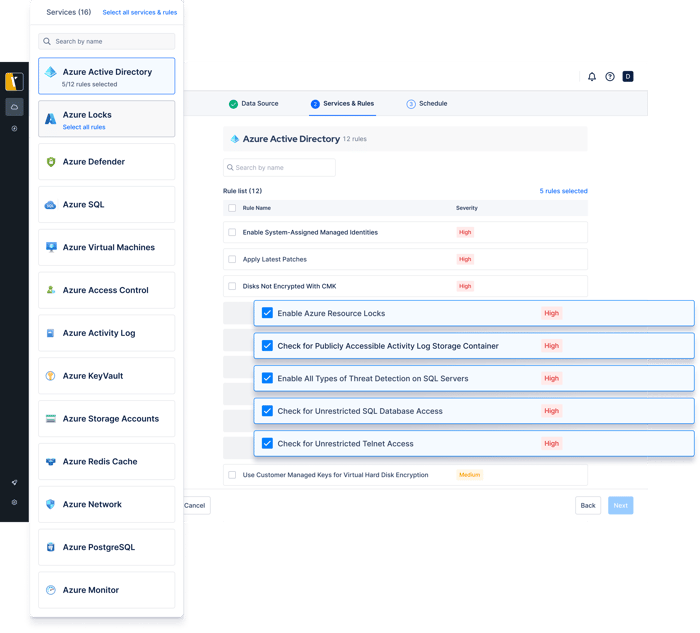
.webp?width=700&height=584&name=Cloud%20Image_4%20(1).webp)
Cloud misconfigurations can leave your services and data exposed to attackers. Picus Cloud Security Validation audits AWS, Azure and GCP services to proactively identify and prioritize risks.
Schedule regular cloud security audits to stay on top of cloud security posture management and respond to risks sooner.
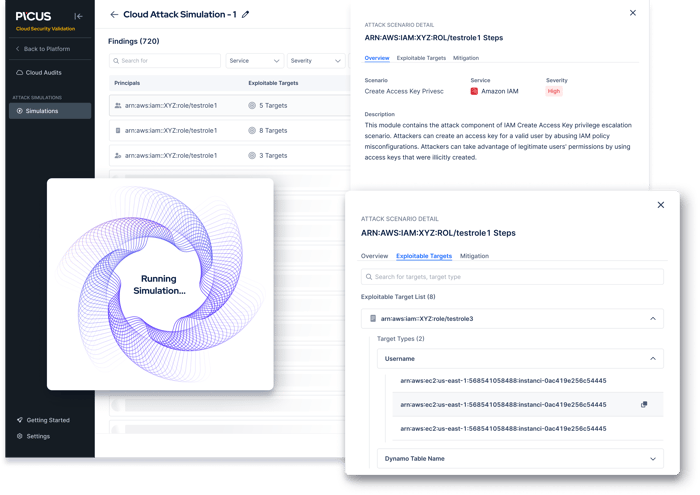
In the event attackers are able to access your cloud environment, they will likely attempt to access critical systems by escalating privileges.
To ensure that your policies follow the principle of least privileges (PoLP), Picus CSV gathers cloud resources and simulates cloud attacks in a Local Policy Simulator.
Picus Cloud Security Validation doesn’t just identify cloud risks. It also provides the insights you need to understand their severity and respond to risks sooner.
Built-in dashboards enable you to track improvements to your cloud security posture and prove your maturity.
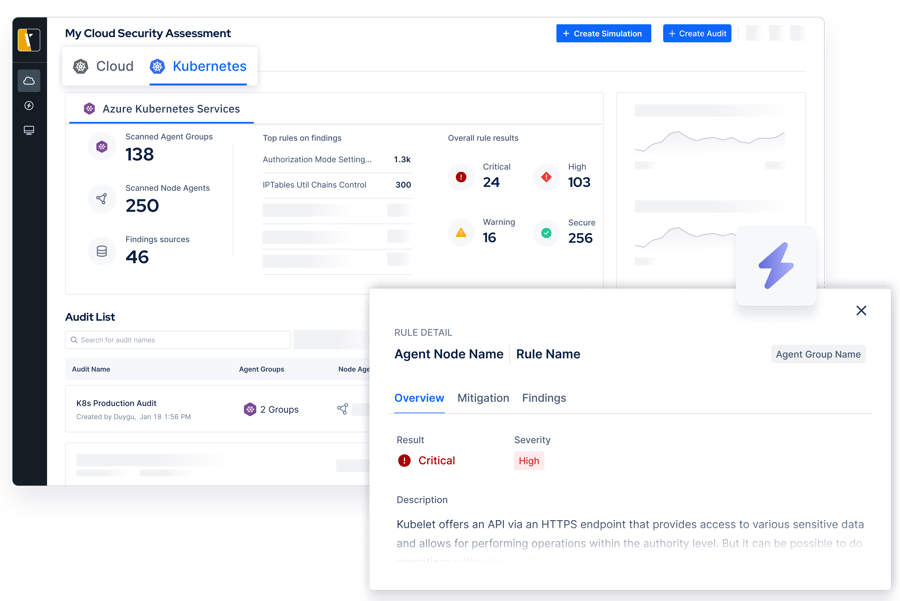
Harden Kubernetes to Secure Your Containerized Applications
If your organization is using Kubernetes to deploy and manage applications in containers, then it’s crucial to assess its security regularly. The dynamic and complex nature of containerized architectures means that weaknesses in the way clusters are configured can easily arise.
With Picus Cloud Security Validation, you can stay on top of container security risks by proactively identifying misconfigurations and by alleviating the time it takes to harden nodes, pods, and policies.
USE CASES
Address Challenges with Security Validation
See and prioritize exposures across your security operations.
Attack
Simulation
Simulate attacks to measure and optimize security controls.
Testing
Stay on top of exposures while alleviating manual testing requirements.
Validation
Improve decision making with a holistic view of your security posture.
Awarded By The Industry
Customer's Choice
2025 Gartner Peer Insights Voice of the Customer for Adversarial Exposure Validation
What Our Customers Say
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer
The implementation was very fast, the platform is easy to integrate and results quite intuitive to be analyzed.
CIO
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated..
ICT Security Engineer
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist
With the help of this product we can perform continuosly endpoint attack via latest tactics and techniques which are used by threat actors..
Manager, IT Security and Risk Management
.. It is possible to customise the campaign or schedule the assessment periodically, to test protection measure implemented on network, endpoint and email.
ICT Security Engineer
Picus is such a great product for organizations that are looking to have constant checks and validation on their security posture in the organization.
Cybersecuirty Pre-sales Engineer
Picus is a real safety measurement tool. Ever since we took Picus into our inventory, Security has helped significantly to increase our maturity level.
Cyber Defense Senior Specialist
It strengthened our security perspective and allowed us to follow trend attacks. We can test zeroday malicious threats very early because Picus could add them their attack database quickly.
Security Specialist
Validate Effectiveness Across Your Security Program
Validation
Enhance visibility of internal and external cyber assets and the security risks they pose.
Validation
Identify cloud misconfigurations and overly permissive identity and access management policies.
Validation
Measure and optimize the effectiveness of security controls with consistent and accurate attack simulations.
Validation
Eliminate high-risk attack paths that attackers could exploit to compromise users and assets.
Validation
RESOURCES
Latest Cloud Security Validation Resources




.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
In today's digital world, organizations are rapidly adopting cloud technology to operate more efficiently and effectively. However, with this trend comes a new set of security challenges. Simple misconfigurations or excessive privileges can easily go unseen, opening doors for attackers to exploit. In contrast to on-premises environments, there are often no security controls in place in cloud environments to protect wrongly configured resources from being exploited. This is why it’s running regular cloud security assessments to identify and mitigate gaps is important.
Constant changes within cloud environments and the frequent discovery of new attack techniques mean that organizations’ cloud security postures can change regularly. Scheduling cloud security audits and cloud attack simulations on at least a weekly basis will help you to identify and address issues before they lead to serious security incidents.
Yes. Picus CSV supports Amazon Web Services, Microsoft Azure and Google Cloud Platform.
Container security is focused on the protection of containerized workloads.
Today, more and more organizations, are choosing to run applications in containers because of the flexibility and scalability it offers. However, if not configured properly, containers can be used by attackers to s to compromise apps, users and data.
.png?width=161&height=136&name=gartner-logo-2025%201%20(1).png)
