BLUE REPORT 2025
The Blue Report 2025 uncovers how security controls perform in practice, based on over 160 million attack simulations across real enterprise environments.
-2.png?width=300&height=373&name=image%20(1)-2.png)
Real-World Effectiveness Is Declining
The 2025 Blue Report reveals a drop in prevention effectiveness to 62%, no improvement in log visibility,
and only a slight uptick in alert generation.
Despite continued investment, many defenses fail to detect or stop today’s most common attacks.

Password Cracking Threat Intensifies
46% of environments had at least one password hash cracked and converted to cleartext. Weak hashing, poor password hygiene, and stored credentials continue to enable lateral movement and privilege escalation across internal domains.


Data Exfiltration Defense Is Getting Worse Despite Rising Risk
Data exfiltration prevention dropped from 9% to just 3%, marking it the weakest vector for the third year in a row. This sharp decline comes as infostealers triple and ransomware groups lean heavily on double extortion, exposing a major gap in defensive readiness.
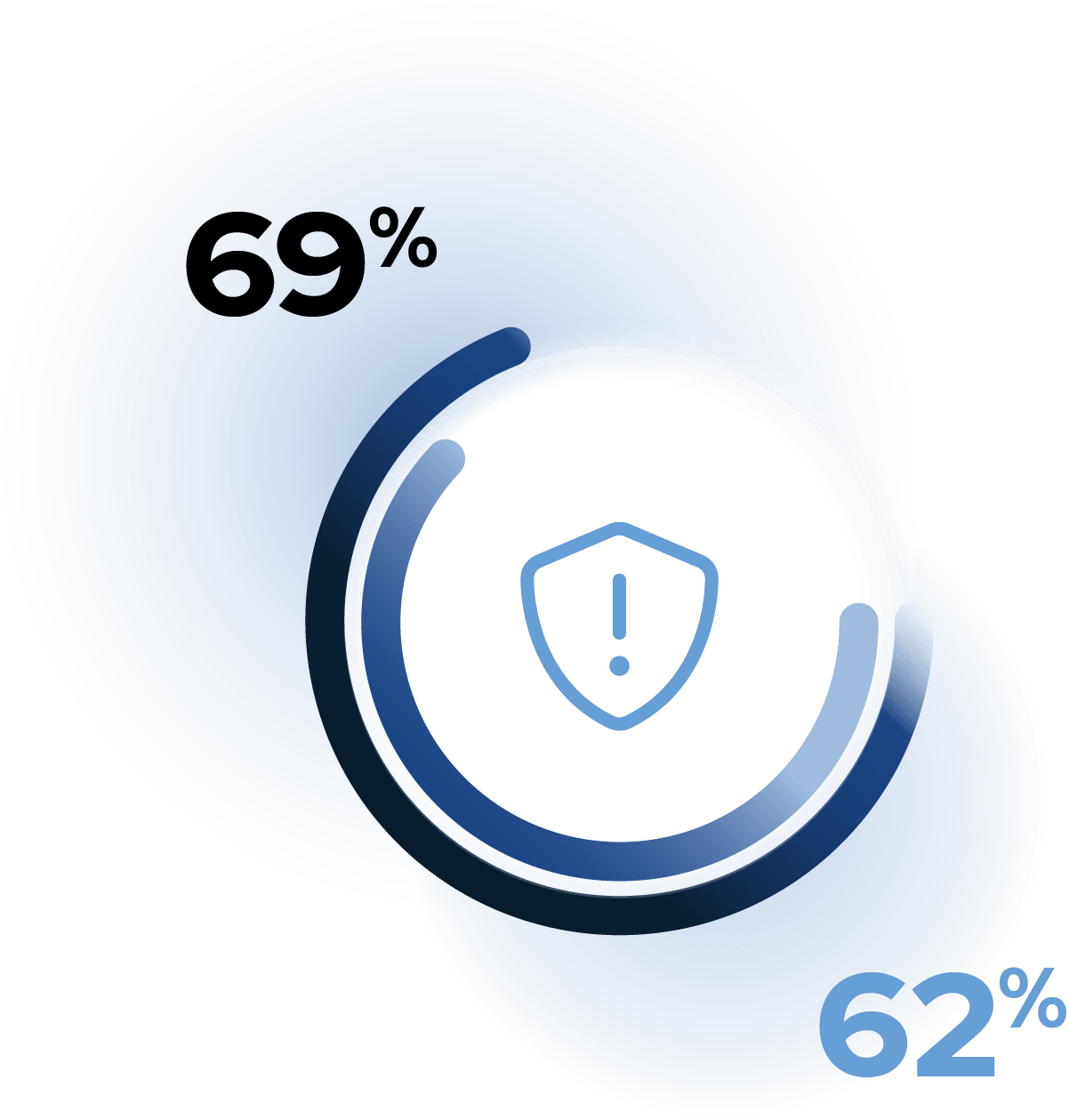
Prevention Effectiveness Declines
After a strong improvement in 2024, the average prevention score fell from 69% to 62% in 2025. This drop suggests that many organizations are struggling to keep up with increasingly sophisticated attack techniques and that previously effective controls may be losing their edge without continuous validation and tuning.
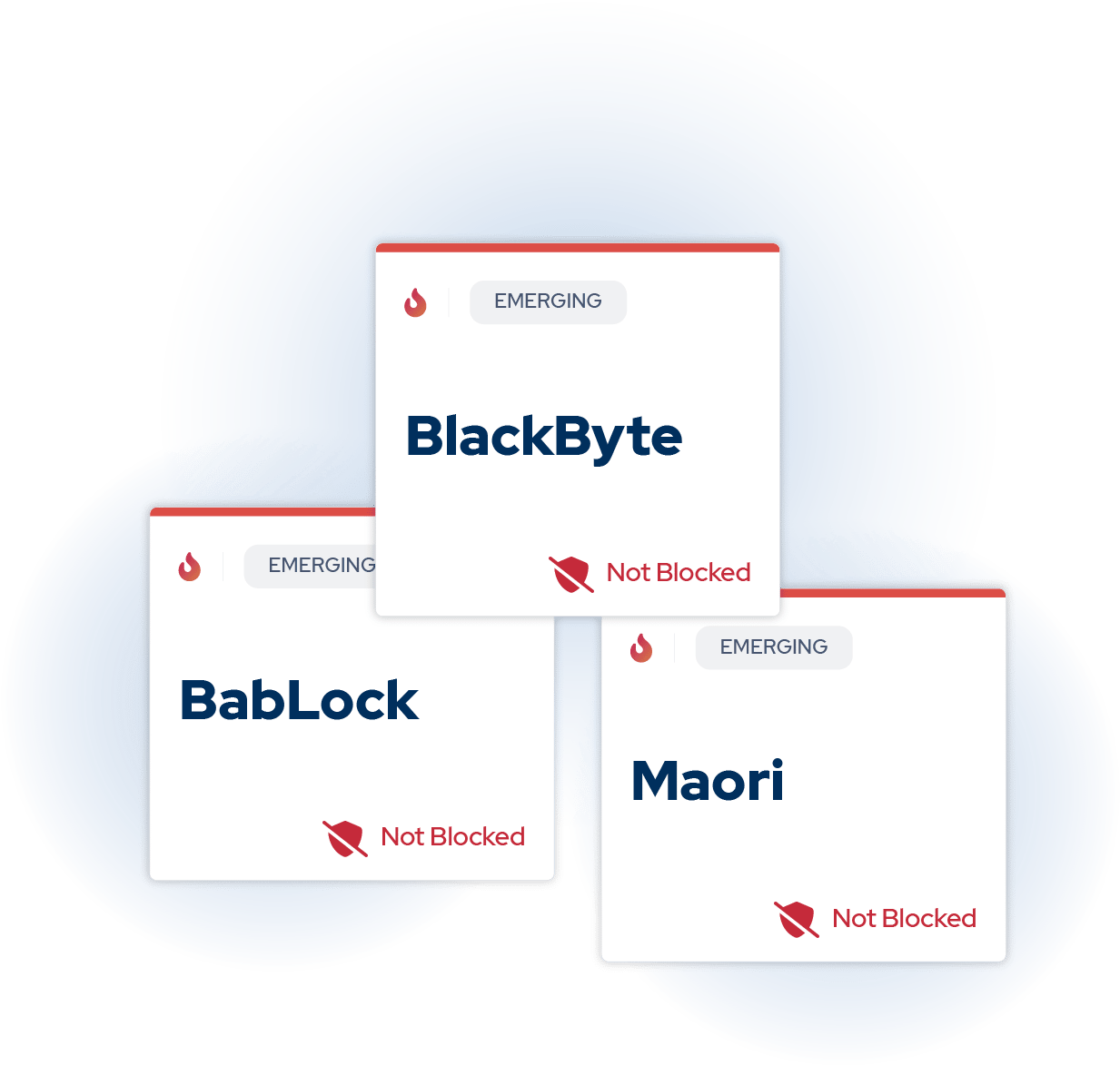
Ransomware Remains a Top Concern
BlackByte continues to be the hardest strain to prevent, with a prevention effectiveness of just 26%, even after its prominence in last year’s findings. BabLock and Maori followed at 34% and 41%, respectively.
Previous Blue Reports


Uncover the Trade-offs Organizations Make When Managing Their Threat Exposure
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
The Picus Blue Report 2025 is an annual research study that analyzes the real-world effectiveness of cybersecurity controls across organizations. Based on over 160 million attack simulations conducted via the Picus Security Validation Platform, the report offers data-driven insights into how well enterprises are able to prevent and detect adversary behaviors across vectors, industries, and regions.
Averaging 14 per sample, with 11,984,156 mapped to the MITRE ATT&CK framework. Out of those techniques, we observed the following top 10 techniques being used in the corresponding order: Process Injection, Command and Scripting Interpreter, Credentials from Password Stores, Application Layer Protocol, Impair Defenses, Data Encrypted for Impact, System Information Discovery, Input Capture, Boot or Logon Autostart Execution, and Data from Local System.