Healthcare organizations use Picus to validate their defenses against ransomware, data breaches, and misconfigurations, helping protect patient data, ensure HIPAA compliance, and strengthen operational resilience without disruption.
Validate Cyber Readiness Across Healthcare Systems
.webp?width=520&height=435&name=healthcare-banner-image-final@72x%20(1).webp)
How Cybercriminals Exploit Healthcare Systems: Gaining Domain Admin in 9 Steps
Northbridge Health Network (NHN) is a large regional healthcare provider, operating multiple hospitals, outpatient clinics, and specialized care centers. With an extensive IT infrastructure, NHN supports critical healthcare applications such as Electronic Health Records (EHR), medical imaging systems, and administrative operations, managing sensitive patient data and medical records.
Key workers involved in this scenario include:

Full Attack Path on a Northbridge Health Network (NHN)
EMMA.SHAW, an administrative assistant at NHN, receives a phishing email from what appears to be her superior. Thinking nothing of it, she opens the attachment, which installs a backdoor on WKSTN16.NHN.LOCAL.
SARAH.KAPLAN, a billing systems specialist, is identified as a Kerberoastable target. A TGS ticket is requested and cracked offline, exposing her password.
On WKSTN16, UAC bypass techniques are employed to escalate privileges, granting high-level access to the system.
With the cracked TGS ticket, SARAH.KAPLAN’s identity is impersonated, enabling access to sensitive systems like the billing platform.
Using SARAH.KAPLAN’s credentials, lateral movement occurs from WKSTN16 to WKSTN26 via SMBExec, maintaining administrative privileges on the new system.
On WKSTN26, cached credentials for DR.MICHAEL.REID are dumped, allowing further impersonation and credential theft.
To maintain stealth, SARAH.KAPLAN’s identity is reverted to while continuing the lateral movement through the network.
A session is created on SRV02 (Clinical Imaging Server) using DR.MICHAEL.REID’s credentials.
On SRV02, LSASS memory is dumped, obtaining THOMAS.NGUYEN’s domain admin credentials, leading to full control over NHN’s domain and critical healthcare systems.
USE CASES
Protect Critical Systems with
Evidence-Driven Validation
Validate how your healthcare defenses hold up against real-world attacks—like ransomware moving through your EHR network or privilege escalation via outdated medical devices. Picus helps test what matters, where it matters most.
Healthcare networks are flat, legacy-heavy, and always expanding. CTEM helps identify and validate exposures across EHRs, IoT devices, and third-party access—continuously, not just during audits.
Attack Simulation (BAS)
Simulate ransomware, phishing, and insider threats without risk. Validate whether your EDR, SIEM, and email security tools can stop real attacks targeting healthcare.
Uncover chained risks like legacy systems + weak identities. Automated pentesting finds attack paths to patient data—no manual red teaming required.
Reveal attack paths that bridge IT and OT. Automated pentesting uncovers chained risks—like weak identities and flat network zones—without manual red teaming or interrupting operations.
Built for The Real World Challenges of Healthcare Institutions
From ransomware simulations to validating control effectiveness and generating compliance reports, Picus helps healthcare security teams stay ahead of threats, meet regulatory demands like HIPAA and HITRUST, and focus on fixing what truly puts patient care at risk.
Simulate ransomware, phishing, and lateral movement tailored to healthcare environments. Validate readiness across EHRs, IoT devices, and third-party portals—before attackers do.
Get audit-ready reports aligned with HIPAA, HITRUST, and ISO 27799 and prove compliance with clear, evidence-based assurance of control effectiveness.
Healthcare teams are stretched thin. Automate offensive testing, prioritize the most critical exposures, and reduce wasted time chasing false positives.
Simulate end-to-end ransomware attacks to uncover gaps in prevention, detection, and response across critical clinical systems.
Whether you operate across on-prem systems, cloud services, or hybrid networks, Picus helps you identify exposures and test defenses consistently without requiring red team expertise.
Reduce alert fatigue and false positives by focusing on what your controls actually detect. Picus enables SOC teams to test detection logic, improve SIEM rules, and prioritize gaps based on real risk.
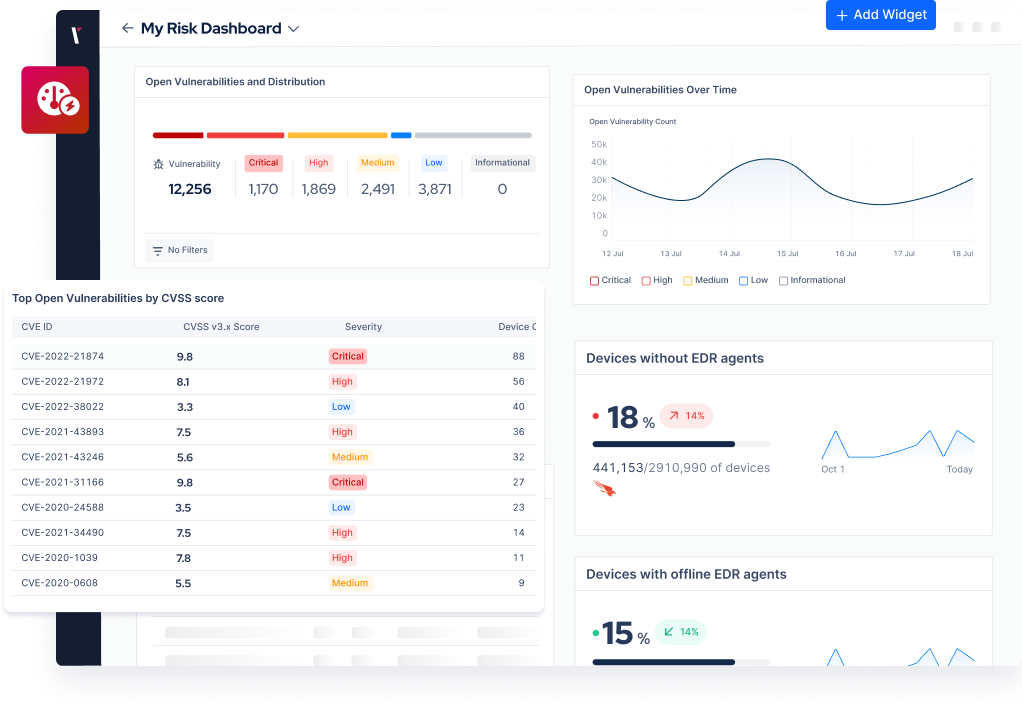
HIPAA Compliance with Continuous Security Validation
Reduce compliance risk by validating your security controls against real-world threats. Learn how Picus helps healthcare organizations stay audit-ready and meet HIPAA requirements with confidence.
Real-World Healthcare Security: A Pragmatic Approach to Protection and Compliance
Watch this webinar to discover a pragmatic strategy that ensures your healthcare system stays protected against modern threats while maintaining compliance and seamless clinical operations.
Simulate Cyber Threats Targeting Healthcare
With Picus Threat Templates for Healthcare, you can validate your defenses against the latest campaigns targeting hospitals and medical systems, including TA505 ransomware, MuddyWater, and Lazarus.
Simulate real-world attacks on endpoints and networks, reveal hidden gaps, and strengthen defenses against sector-specific risks.
Why Healthcare Organizations Choose Picus
Security leaders across the healthcare sector trust Picus to validate their security posture safely, continuously, and at scale.
Here's how Picus supports key roles across the organization:
-
CISOs gain clear visibility into security posture and control effectiveness,enabling them to report measurable risk reduction to executives and boards.
-
SOC Managers streamline operations, reduce alert fatigue, and ensure security controls perform reliably against real-world threats.
-
Compliance Officers simplify audit preparation with evidence-based reporting aligned with HIPAA, HITRUST, ISO 27799, and other regulatory frameworks.
-
Security Analysts get hands-on visibility into what their controls are blocking or missing and can quickly apply vendor-specific mitigations.
CUSTOMERS
Sutter Health’s Continuous Security Validation With Picus
Sutter Health replaced manual security testing with continuous, automated validation using Picus. Real-world attack simulations reduced validation cycles from weeks to under an hour, improved visibility into control effectiveness, and supported faster remediation and HIPAA compliance.

RESOURCES
Stay Informed with Picus Healthcare Blogs



.png?width=353&height=200&name=picus-Why-Healthcare-Needs-exposure-validation-blog%20(1).png)

.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
Healthcare organizations face significant cybersecurity threats, including ransomware attacks, advanced persistent threats (APTs), phishing, insider threats, unpatched vulnerabilities in legacy systems, cloud misconfigurations, and supply chain exploits. Due to the high value of patient data and life-critical systems involved, these risks must be continuously validated through proactive testing such as Breach and Attack Simulation (BAS) and Automated Penetration Testing. This validation ensures security controls effectively protect against real-world threats.
Ransomware incidents can have devastating effects on healthcare organizations, disrupting patient care, compromising life-saving operations, and causing severe financial losses. Beyond operational disruption, attackers often demand substantial ransoms and threaten to leak sensitive patient data, risking patient safety and trust. On average, healthcare breaches cost around $10.93 million, reflecting the industry's vulnerability. Continuous validation helps mitigate these impacts by identifying weaknesses before attackers do, ensuring faster response and recovery.
Continuous validation of security controls is critical for healthcare organizations to maintain compliance with regulations such as HIPAA, HITECH, GDPR, ISO 27799, and HITRUST CSF. Traditional periodic assessments often miss evolving threats. Leveraging automated and continuous validation platforms like Picus, healthcare organizations can demonstrate consistent adherence to regulatory requirements. By continuously testing defenses and promptly addressing identified gaps, compliance becomes proactive rather than reactive, helping healthcare providers meet stringent standards while safeguarding patient data.
Many healthcare SOCs struggle with overwhelming alert volumes and false positive alerts. This often leads to alert fatigue, missed threats, and reduced response speed. By continuously validating detection rules and simulating real-world attacks, teams can identify what their tools are catching and what they're missing. Platforms like Picus help optimize SIEM and EDR configurations, reduce false positives, and ensure that analysts are focused on real threats, not noise.
BAS allows healthcare organizations to safely simulate attacker techniques used in real-world campaigns, such as ransomware, credential theft, and lateral movement. Unlike one-off assessments, BAS is continuous, automated, and tailored to your environment. It helps validate that security controls are working as expected, identifies prevention and detection gaps, and enables teams to apply mitigation measures with confidence without disrupting critical workflows.
Yes. Picus simulates ransomware behaviors from initial infection to encryption and data exfiltration, allowing healthcare organizations to assess their defenses across the kill chain. This includes validating endpoint protection, email gateways, segmentation, and detection workflows. With visibility into what techniques are detected or blocked, teams can proactively close gaps, reduce dwell time, and strengthen preparedness against high-impact ransomware threats.