BianLian Ransomware Analysis - The Rise of Exfiltration-based Extortion
On May 16th, 2023, The Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory on BianLian ransomware that has been targeting various critical infrastructure sectors in the United States and Australia [1]. Initially employing a double-extortion model, BianLian has recently shifted its focus to data exfiltration due to the availability of a free decryption tool. Although the group has seemingly abandoned data encryption techniques, it continues to be a significant threat to organizations.
Picus Threat Library has already incorporated attack simulations for BianLian ransomware. This article will outline the tactics, techniques, and procedures utilized by the BianLian group and provide guidance for assessing security postures against such ransomware and data exfiltration attacks.
Simulate Ransomware Threats with 14-Day Free Trial of Picus Platform
BianLian Ransomware and Extortion Group
BianLian ransomware first emerged in June 2022, primarily targeting financial institutions, healthcare, manufacturing, education, entertainment, and energy sectors. The financially motivated cybercrime group mainly targets organizations in the United States, the United Kingdom, and Australia. As of March 2023, BianLian has affected over 118 organizations globally, based on information from their leak site.
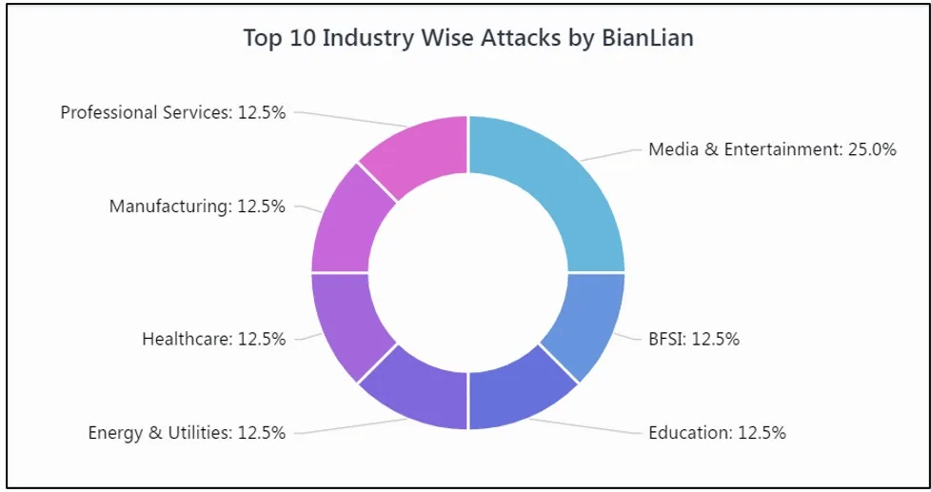
Figure 1: Distribution of BianLian Ransomware Attacks by Industries [2]
What Is BianLian Ransomware?
BianLian ransomware is written in Go. Typically, this threat actor infiltrates victim systems using legitimate Remote Desktop Protocol (RDP) credentials. Upon gaining access, the group employs open-source utilities and command-line scripts to extract victims' data through File Transfer Protocol (FTP), Rclone, or Mega. Subsequently, they demand payment, threatening to disclose the stolen data if their financial demands are unmet. At first, the group employed a single-extortion method by encrypting their victim data and demanding ransom for the decryption key. Later, they adopted data exfiltration techniques into their ransomware campaign and began threatening their victims of unauthorized disclosure of their stolen data unless the demanded ransom was paid. In January 2023, following Avast's release of a free decryptor for BianLian ransomware [3], the group shifted its focus to data exfiltration attacks while ceasing to encrypt victims' files.
How Picus Helps Simulate BianLian Ransomware Attacks?
We strongly suggest simulating BianLian attacks to test the effectiveness of your security controls against ransomware and data exfiltration attacks using the Picus The Complete Security Validation Platform. Furthermore, within minutes, the platform can test defenses against hundreds of other ransomware types, including LockBit, Maui, and ESXiArgs, via a 14-day free trial.
Picus Threat Library includes the following threats for BianLian ransomware:
|
Threat ID |
Threat Name |
Attack Module |
|
83194 |
BianLian Ransomware Campaign 2022 |
Endpoint |
|
31861 |
BianLian Ransomware Download Threat |
Network Infiltration |
|
89413 |
BianLian Ransomware Email Threat |
Email Infiltration (Phishing) |
The Picus Threat Library encompasses numerous threats specific to BianLian ransomware, alongside 700+ other ransomware threats. Additionally, 4500+ web application, vulnerability exploitation, endpoint, malware, email, and data exfiltration threats, and 20,000+ atomic actions under these threats are also covered.
Picus also provides actionable mitigation content. Picus Mitigation Library includes prevention signatures to address BianLian ransomware and other ransomware attacks in preventive security controls. Currently, Picus Labs validated the following signatures for BianLian ransomware:
|
Security Control |
Signature ID |
Signature Name |
|
Check Point NGFW |
0B559CB5E |
Ransomware.Win32.BianLian.TC.9f28TFdp |
|
Check Point NGFW |
0E8E7A377 |
Ransomware.Win32.BianLian.TC.eeb1EEZm |
|
Check Point NGFW |
0F3748C77 |
Ransomware.Win32.BianLian.TC.a |
|
Check Point NGFW |
0C1D9F8D2 |
Ransomware.Win32.BianLian.TC.829cSYVE |
|
Cisco FirePower |
W32.Auto:46d340.in03.Talos |
|
|
Cisco FirePower |
W32.Auto:1fd07b.in03.Talos |
|
|
Cisco FirePower |
W32.EAF5E26C5E.in12.Talos |
|
|
Cisco FirePower |
W32.Auto:3a2f6e.in03.Talos |
|
|
Forcepoint NGFW |
File_Malware-Blocked |
|
|
Fortigate AV |
10102076 |
W64/Filecoder.BT!tr.ransom |
|
Fortigate AV |
8162978 |
W32/Filecoder.BT!tr |
|
McAfee |
0x4840c900 |
MALWARE: Malicious File Detected by GTI |
|
Palo Alto NGFW |
531057977 |
trojan/Win32.filerepmalware.jf |
|
Palo Alto NGFW |
570478178 |
Ransom/Win64.bianlian.a |
Simulate emerging threats and gain actionable mitigation insights with a 14-day free trial of the Picus Complete Security Validation Platform.
Conclusion
In summary, the BianLian Ransomware Group presents a significant threat to organizations of all sizes, necessitating the implementation of robust security measures.
Additional recommendations for defending against ransomware attacks include:
-
Validate security controls, ensuring that your security measures are ready against ransomware attacks.
-
Regularly back up data, enabling easy restoration in the event of its encryption by ransomware.
-
Utilize strong passwords and multi-factor authentication to create obstacles for attackers attempting to infiltrate your systems.
-
Keep software up to date, ensuring that vital security patches are installed to help protect against ransomware attacks.
-
Educate employees about phishing attacks, as these are among the most prevalent methods of delivering ransomware. Equip staff with the knowledge to recognize and avoid phishing emails.
By adhering to these guidelines, organizations can bolster their defenses against ransomware attacks.
References
[2] "BianLian: New Ransomware variant on the rise," Cyble, Aug. 18, 2022. [Online]. Available: https://blog.cyble.com/2022/08/18/bianlian-new-ransomware-variant-on-the-rise/. [Accessed: May 16, 2023]
[3] "Decrypted: BianLian Ransomware," Avast Threat Labs, Jan. 16, 2023. [Online]. Available: https://decoded.avast.io/threatresearch/decrypted-bianlian-ransomware/. [Accessed: May 16, 2023]








