What Is Detection Rule Validation (DRV) ?
Detection Rule Validation (DRV) is a vital cybersecurity process that continuously assesses and validates detection rules used in defensive solutions, improving an organization's security posture. Automating DRV ensures accurate, efficient threat detection and response, allowing security teams to monitor real-time rule performance and address high-priority issues effectively.
What Is Detection Rule Validation?
Detection Rule Validation (DRV) is a cybersecurity process of continuously testing, evaluating and fine-tuning detection contents used in defense solutions like SIEM, EDR, and XDR. Organizations can benefit from Detection Rule Validation to improve their security posture by ensuring that their detection rules are working as accurately and effectively as intended.
Detection Rule Validation is an integral part of any organization's cybersecurity strategy as it enhances the overall security posture of an organization. By allowing security teams to assess the effectiveness of their detection rules, organizations can decrease the cost of developing and running detection contents and ensure that they can detect and respond to threats quickly and efficiently.
Automation is vital in streamlining the rule validation process and enabling real-time adjustments. Manual validation of detection rules is highly costly as they only reflect on the point-in-time health of a detection rule. Hence, manual detection rules validation requires the constant attention of an organization’s security team, which results in frustration and inefficient use of resources. By leveraging an automated Detection Rule Validation solution, organizations can ensure a better and real-time understanding of their SIEM systems and detection rules.
In conclusion, Detection Rule Validation (DRV) enables organizations to have a more robust defense against emerging cyber threats while reducing resource strain and maintaining compliance with relevant regulations and standards.
Why Is Detection Rule Validation Important?
There are six key reasons why Detection Rule Validation is important for organizations.
- Understand Real-Time Health and Performance of Detection Rules
- Focus on the High Priority Detection Rule Issues
- Enable Proactive Rule Validation
- Optimize Threat Detection and Response
- Gain Visibility of Your Rule Baseline
- Validate the Effectiveness of Detection Rules
Each key point is given with a brief explanation below.
a. Understanding Real-Time Health and Performance of Detection Rules
Detection Rule Validation is important because it helps organizations to see the real-time health of their detection rules. Due to
- misconfigurations,
- improper and unexpected changes in security solutions, and
- the complexity of the environment that defense solutions are working on,
detection rules that run in a perfect state of health and performance can stop working suddenly. Hence, it becomes almost impossible for security teams to keep up with the ever-changing health of your detection rules.
For instance, in one scenario, you might have a day where only 16 detection rules are not working; the next day, you can see that that number has skyrocketed to 250. Or, you might have a detection rule that used to run in 1.25 seconds before taking 5 minutes to run right now.
While your security team might have trouble and spend hours figuring out the reason for such dramatic change, the reason might be an unavailable log source, the use of the wrong accelerator, an index update issue, or a broken log source. Sudden changes in the health and performance of detection rules require the immediate attention of an organization’s security team. Even though you might claim that your organization has enough human resources, manual detection rule validation results in high costs and inefficient use of your human resources.
In other words, your defense team must give their undivided attention to figuring out the root cause of sudden changes in your detection rule health. Thus, the detection rule validation process has to be automated as it helps organizations understand the point-in-time health of their detection rules and highlights the possible causes behind issues encountered.
b. Focusing on the High Priority Detection Rule Issues
Focusing on what matters most is a key benefit of Detection Rule Validation, as it helps security teams to prioritize their efforts and resources more effectively.
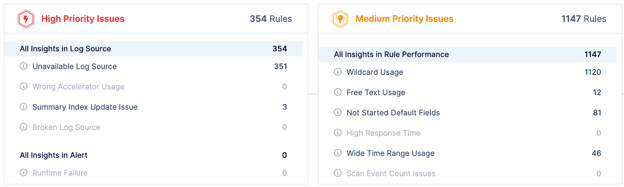
Figure 1. Picus Detection Rule Validation Rule Insights Interface.
Your Detection Rule Validation solution can provide rule insights for your detection rules. Detection rule insight can show you the high and medium priority issues that require your security team’s attention.
-
High Priority Issues
During Detection Rule Validation, issues that can cause a detection rule to stop functioning are flagged as High Priority Issues. While such issues commonly include unavailable or broken log sources, there can also be problems with the index update process that hampers the detection rule's ability to receive updates from the associated data model.
For instance, an unavailable log source could arise from network connectivity problems or a malfunctioning device, resulting in a lack of incoming logs for the detection rule. Simultaneously, an index update issue may occur, preventing the detection rule from receiving the latest information stored in the summary index associated with the data model.
To ensure effective detection, these high priority issues require prompt resolution. It involves addressing any log source issues, such as fixing network connectivity or resolving device malfunctions, and resolving any problems with the index update process to synchronize the data model with the summary index, enabling accurate detection and alert generation for potential security threats.
-
Medium Priority Issues
A medium priority issue refers to a problem or concern that is significant but not as urgent or critical as a high priority issue. It signifies an area of attention that requires action or resolution, albeit with a lower level of immediate impact or severity.
In the context of detection rules or security monitoring systems, a medium priority issue could indicate a situation that needs to be addressed to ensure optimal performance, efficiency, or accuracy of the rules. It may involve issues such as moderate resource consumption, suboptimal configuration settings, or certain limitations in rule logic or coverage.
While medium priority issues may not have an immediate detrimental effect on the system or security posture, they should still be acknowledged and resolved to maintain the effectiveness and reliability of the overall monitoring infrastructure. Addressing medium priority issues helps improve the system's performance, enhance detection capabilities, and optimize resource utilization for better operational efficiency.
Example: What Happens When You Do Not Utilize Log Source Parameters?
For instance, your Detection Rule Validation solution may identify a detection rule that isn't utilizing any log source parameters. In other words, without specified parameters, the rule may not have the necessary focus to sift through the vast amount of log data and pinpoint the relevant security events or anomalies. It's like trying to find a needle in a haystack without knowing what the needle looks like. Thus, improper practice of not using log source parameters often results in negative situations in terms of resource consumption. Therefore, such oversights, although not immediately disabling, contributes to a decline in the performance and health of your detection rules.
This instance illustrates that even issues of medium priority can have significant impacts on the effectiveness of your security measures. Hence, it's crucial to address these issues promptly to ensure optimal performance and efficiency of your detection rules.
c. Enabling Proactive Rule Validation
Enabling proactive rule validation is essential for maintaining a strong cybersecurity posture. By regularly validating SIEM detection rules, SOC teams can gain valuable insights into their threat coverage, accuracy, and performance. This allows them to quickly identify and address any gaps in their defenses, ensuring comprehensive protection against known and emerging threats. As a result, SOC teams can focus on real threats rather than being overwhelmed by irrelevant alerts.
Example: How Can You Leverage DRV for Proactive Rule Validation?
For instance, you might want to improve the overall health of a particular detection rule. To do this, you have changed a few things in your software environment (Splunk, for instance). Now, you want to be sure about the accuracy of these changes so that the updated rule does not cause any negative impact or it does not populate true-positive alarms. To test the accuracy and performance of a change in the detection rule, you can look at your detection rule validation, as it will show real-time changes in the performance of the detection rule.
d. Optimizing Threat Detection and Response
Optimizing threat detection and response through detection rule validation can be examined under five main categories.
-
Holistic Visibility
-
Operationalizating MITRE ATT&CK Framework
-
Enhanced Threat Detection
-
Improved Response Capabilities
-
Continuous Testing of the Detection Rule Health
You can find a brief explanation for each category given above.
1. Holistic Visibility
To optimize threat detection and response, it is crucial to have a comprehensive view of an organization's security landscape. This involves collecting and analyzing data from various log sources such as network logs, endpoint logs, security devices, and cloud infrastructure. By aggregating and correlating this data, organizations can gain visibility into potential threats and identify patterns of malicious activity.
For instance, using a SIEM (Security Information and Event Management) system, organizations can collect and analyze logs from different sources, correlate events, and gain a holistic view of potential threats across their infrastructure. By continuously validating the detection rules implemented within the SIEM, security teams can ensure that the detection rules are working accurately and performing efficiently. This validation process helps maintain the integrity and effectiveness of the detection rules, contributing to a more robust security posture.
2. Operationalizating MITRE ATT&CK Framework
Operationalizing the MITRE ATT&CK Framework involves aligning detection rules and response procedures with the ATT&CK framework's adversary tactics, techniques, and procedures (TTPs). This alignment enhances an organization's threat detection and response capabilities by highlighting the gap in their detection coverage against a wide range of adversary behaviors and giving detection rule suggestions.
Adding a Detection Rule for Credential Dumping with Detection Rule Validation
For example, adversaries frequently employ the OS Credential Dumping (T1003) ATT&CK technique. Attackers typically attempt to dump credentials to gain access to valid accounts and credential material, usually in the form of a hash or clear text password, from the operating system and software. Once attackers have valid account credentials, they can leverage them to move laterally across the network and access restricted/sensitive information.
Thus, it's essential for organizations to establish detection rules that trigger an event when a potential credential dumping attack occurs. This could be something like dumping the memory of the lsass.exe process or the %systemroot%\system32\config\SAM file.
Consider a scenario where a security team utilizes a Detection Rule Validation solution and discovers they lack detection rules for a potential OS Credential Dumping attack technique. Given the severe implications of a potential OS Credential Dumping (T1003) attack, Detection Rule Validation platforms can recommend detection rule content that can be readily incorporated into your security solution.
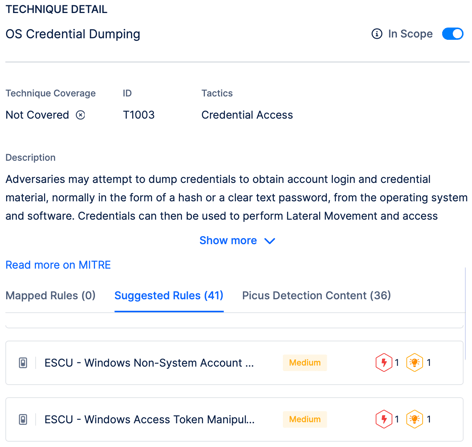
Figure 2. Identifying Gaps in your Detection Rules through MITRE ATT&CK Framework.
Furthermore, after integrating a new detection rule into your security solution, you can continuously track and analyze the rule's real-time effect, health, and performance.
In conclusion, Detection Rule Validation (DRV) solutions assist organizations in aligning their existing detection rules with MITRE ATT&CK techniques and uncovering any deficiencies within the framework. After an organization identifies gaps in its detection coverage, a Detection Rule Validation platform can suggest appropriate rules to fill these gaps. Implementing these rules can enhance an organization's capacity to safeguard itself from cyberattacks.
Knowing the devastating effects of a possible OS Credential Dumping (T1003) attack, Detection Rule Validation platforms can suggest detection rule contents that you can easily apply to your security solution. In addition, after adding a new detection rule to your security solution, you can continuously analyze this new rule's point-of-time effect, health, and performance.
In conclusion, Detection Rule Validation (DRV) solutions help organizations to map their newly added or existing detection rules to MITRE ATT&CK techniques and identify their gaps in the framework. Once an organization has identified its detection gaps, it can use a Detection Rule Validation platform to suggest corresponding rules. These rules can then be implemented to fill the gaps in the organization's detection coverage. This can help the organization to better protect itself from cyberattacks.
3. Enhanced Threat Detection
As mentioned in the previous section, Detection Rule Validation (DRV) can help organizations to map both existing and newly added detection rules to the MITRE ATT&CK Framework. Detection Rule Validation leverages AI technology to make trained suggestions for mapping each detection rule to the ATT&CK framework. This can help organizations to improve their threat detection capabilities by identifying gaps in their detection coverage and ensuring that their rules are working as intended.
For example, a security team can develop a detection rule for detecting a suspicious MS scripting process such as wscript.exe or cscript.exe that is loading a WMI module to process a WMI query. Without Detection Rule Validation, it would be difficult for this organization to map this detection rule to the corresponding technique in the MITRE ATT&CK Framework. However, with Detection Rule Validation, organizations can simply integrate their data analysis software solution into their DRV, and the platform will give trained suggestions to map the rule to the appropriate technique. Thus, Detection Rule Validation (DRV) helps organizations continuously track and analyze newly added rules, as well as all other existing rules within the focused ATT&CK tactics and techniques.
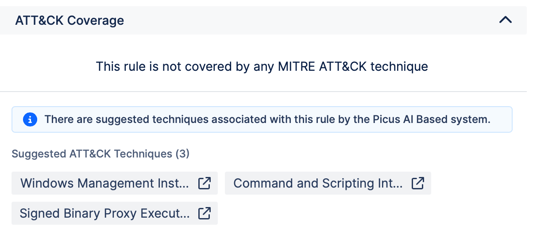
Figure 3. Mapping Detection Rules to a MITRE ATT&CK Framework.
Detection Rule Validation can help organizations to improve their threat detection capabilities in a number of ways. First, it can help organizations to identify gaps in their detection coverage. By mapping detection rules to the MITRE ATT&CK Framework, organizations can gain a better understanding of which attack techniques their detection rules are protecting against. This can help organizations to identify areas where they may need to add additional detection rules.
Second, DRV can help organizations to ensure that their rules are working as intended. By mapping detection rules to the MITRE ATT&CK Framework, organizations can verify that their rules are actually detecting the intended attack techniques. This can help organizations to avoid false positives and false negatives.
Finally, DRV can help organizations to improve their overall security posture. By improving their threat detection capabilities, organizations can make it more difficult for attackers to successfully infiltrate their systems. This can help organizations to protect their data and assets from attack.
4. Improved Response Capabilities
Through Detection Rule Validation, organizations have the capability to verify the performance and accuracy of their crucial detection rules. These are the rules designed to respond appropriately to potential security threats. By ensuring these rules are functioning accurately and maintaining a healthy state, organizations can bolster their security infrastructure, providing more robust protection for their data and systems.
In conclusion, Detection Rule Validation (DRV) helps organizations check whether critical detection rules are working accurately and in a healthy way.
5. Continuous Testing of the Detection Rule Health
Detection Rule Validation is a critical step in maintaining the integrity of any system, as it ensures that the rules are functioning correctly and involves a continual monitoring process. Continuous monitoring and analysis of detection rules is essential for identifying potential situations or anomalies that could arise due to the operation of these rules. When such situations occur, they could indicate potential issues concerning the health or effectiveness of the rules, which could compromise the overall functionality of the system
Therefore, it's vital to detect these issues promptly and suggest appropriate solutions to mitigate them. In this way, detection rule validation helps ensure a rule's accuracy, increases its overall performance, and contributes to its resilience and adaptability in changing conditions.
e. Gaining Visibility of Your Rule Baseline
As a security professional, even though you added a new detection rule without encountering any problems, the rule can stop working suddenly due to the slightest change in your detection environment. Organizations can gain continuous and point-in-time visibility into their rule baseline by leveraging a detection rule validation platform.
Detection Rule Validation allows organizations to track and monitor the health and performance of their rules in real-time. As a result, when facing newly emerging threats, the process of adapting detection rules can be significantly streamlined. Instead of spending hours manually assessing and modifying rules, organizations can quickly identify gaps or areas requiring improvement, reducing the detection engineering efforts from hours to just a few minutes. This enhanced visibility empowers organizations to stay agile and effectively respond to emerging threats in a timely manner.
f. Validating the Effectiveness of Detection Rules
Through Detection Rule Validation platforms allow organizations to validate the effectiveness of their new and existing rules based on log coverage, alert frequency and performance metrics.
What Are the Key Steps in Detection Rule Validation?
There are eight key steps in Detection Rule Validation.
-
Rule Preparation
-
Rule Analysis
-
Issue Identification
-
Issue Categorization
-
Solution Development
-
Documenting and Reporting
-
Testing and Verification
-
Iterative Improvement
Below, we’ve provided an overview of each key step presented here.
a. Rule Preparation
Rule preparation is a multi-faceted process and entails more than just relying on a security product. It begins with comprehensive research to understand the threat landscape and the specific scenario that the rule is intended to address.
It's essential to scrutinize the existing environment and conduct thorough log reviews to understand the current state and look for any anomalies or patterns. An internet scan for the written scenario can provide valuable insights into the latest threats and strategies employed by cyber adversaries.
All these steps aim to collect all the necessary data required to write an effective rule. This extensive preparation helps in crafting precise rules that are adept at identifying potential threats, thereby enhancing the overall security posture.
b. Rule Analysis
A Detection Rule Validation platform checks the syntax and structure of the detection rules to ensure they are correctly written and free of any syntax errors. DRV verifies that the rules are properly structured and follow the query language or the requirements of the security product.
For instance, in the context of detection rules, wildcards can cause false positives (F/P) and be resource-intensive. A wildcard in a detection rule typically stands for any character or set of characters, allowing the rule to match a wide range of data. While this can be beneficial for ensuring broad coverage, it can also lead to the detection of data that shouldn't be flagged (false positive). Additionally, because the detection rule has to check against a much larger set of possibilities, it can consume significant computational resources.
c. Issue Identification
DRV (Detection Rule Validation) works to identify issues that may hinder or negatively affect the functioning of a rule.
For instance, one critical area that DRV assesses is the logic of the detection rules. It examines the structure of the queries, conditionals, and logical operators, and looks for any potential gaps or inaccuracies that may exist in the rule logic. These could involve faulty assumptions, overlooked scenarios, or errors in the logical flow that may compromise the rule's effectiveness.
DRV also identifies any configuration-related issues in the rules. These could be related to parameters, thresholds, time windows, or other settings that influence the rule's behavior and performance. By assessing these factors, DRV ensures that the rule is correctly configured for optimal functionality.
Finally, Detection Rule Validation (DRV) evaluates the performance of the detection rules. It pinpoints any inefficiencies, bottlenecks, or scalability concerns that could impact the rule's execution time, resource usage, or overall performance. By addressing these concerns, DRV can help improve the rule's efficiency and scalability, thereby enhancing its effectiveness in detecting threats.
d. Issue Categorization
In Detection Rule Validation (DRV), issues are identified and categorized based on their severity and impact on the operation and performance of the rules. Typically, issues are classified into categories such as high priority and medium priority.
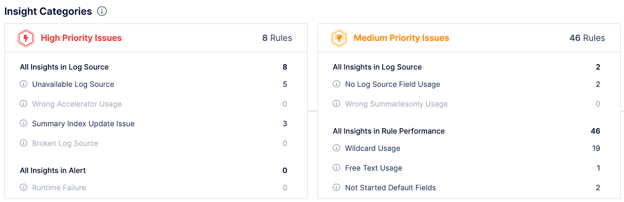
Figure 4. Detection Rule Issue Categorization with Detection Rule Validation (DRV).
Furthermore, DRV provides insightful categorizations along with the identification of scenarios where a single problem might affect multiple rules. This means if one issue arises, it may have a cascading effect and impact several rules. In such cases, Detection Rule Validation helps in detecting negative instances and provides a comprehensive list of all the rules affected by the particular problem. This detailed categorization and extensive detection process help in better management of the rules and more effective resolution of issues.
e. Solution Development
Upon identifying the issues with Detection Rule Validation (DRV), appropriate solutions or recommendations are developed to address these issues.
For some matters, Detection Rule Validation can provide direct solutions, which might include modifying the rule queries, adjusting configurations, or refining the logic to improve detection accuracy.
In other instances, where a direct solution might not be feasible or the issue is more complex, Detection Rule Validation offers some suggestions that can be performed to further investigate and resolve the issue. These recommendations can also include the addition of new rules to strengthen your security posture.
f. Documentation and Reporting
In the Detection Rule Validation (DRV) process, all identified issues, their categorization, and the corresponding solutions or recommendations are thoroughly documented. This includes not only specific issues related to individual rules but also an overarching view of the general health status of all rules in the environment. DRV provides insights and reports on the overall performance, improvement rates, and trend analysis of the rule health, offering a holistic view of the detection rules' effectiveness. A comprehensive report is prepared summarizing the findings and actions taken during the validation process, which acts as a valuable resource for understanding the current state of the rules and guiding future enhancements.
g. Testing and Verification
Test the modified or updated detection rules to ensure that the issues have been resolved and that the rules are functioning as intended. Verify the effectiveness and accuracy of the rules in detecting the desired patterns or threats.
h. Iterative Improvement
Detection Rule Validation (DRV) continuously refine and improve the detection rules based on the insights gained through the validation process. DRV regularly assesses the rules, addresses new issues, helping organizations stay updated with emerging threats and best practices.
In addition, during the evaluation process of a detection rule, if a critical finding related to the rule's health is detected, corrective measures can be immediately taken to address it. Alternatively, the rule can be tracked post-implementation, and any issues that may arise even 15 days or more after the rule's creation can be identified via Detection Rule Validation. This process not only helps in maintaining the robustness of the rules but also ensures that any potential issues are promptly identified and addressed, thereby enhancing the overall effectiveness and reliability of the system.
What Are the Common Challenges in Detection Rule Validation?
The most common challenge in detection rule validation is ensuring the rule is functioning correctly. This involves determining whether the rule is operational, whether it has been disabled to environmental factors, or whether it is not functioning at all. Detection rule validation demands a continuous monitoring process, which can be a difficult and labor-intensive task. Given the dynamic nature of cybersecurity threats, rules can abruptly stop working or not work as expected, making it a constant challenge to keep up with the validation. Therefore, persistence, attention to detail, and an automated proactive approach for detection rule validation are required to manage and overcome these challenges effectively.
What Are the Best Practices for Detecting Rule Validation?
The best practices for detection rule validation start with defining an assessment scope and scheduling continuous assessments via an API connection. Once the first assessment is initiated, it's important to review the results, prioritize insights based on their categories, and then refine the rules accordingly. This cycle of assessing, improving, and reassessing should be repeated regularly.
When developing a new rule, it's crucial to include it in the next automatic assessment conducted by Detection Rule Validation (DRV). DRV enables you to gain valuable insights about a detection rule's operation and make necessary improvements right from the start. However, there could be circumstances that might hinder the optimal performance of the new rule. Detection Rule Validation is instrumental in identifying such issues that may affect the rule's effectiveness. These issues can be tracked and managed through DRV, and the provided recommendations can be implemented to update and fine-tune the rule.
As a result, you can ensure not only the optimal performance of the new rule from day one but also its continuous improvement through ongoing assessments. This iterative process, supported by Detection Rule Validation, helps to ensure the effectiveness and accuracy of your detection rules, leading to a more robust security posture.
What Is the Difference Between Testing and Validation of Detection Rules?
Testing and validation of detection rules are two distinct but equally important processes in maintaining a robust security posture. Testing is the process of verifying that detection rules are functioning as intended. This stage ensures that the rules are implemented correctly and are operational within the designated environment.
Detection Rule Validation (DRV) goes a step further by not just confirming that the rules are working, but also about ensuring that they are accurate, effective, and efficient. Detection rule validation includes identifying any circumstances in the environment that could adversely affect the operation of the rules. By pinpointing these potential disruptions, validation helps in ensuring the rules' continued effectiveness despite any environmental challenges.
a. Detection Rule Testing vs. Detection Rule Validation
In this section, we provide a comprehensive table that compares detection rule testing and detection rule validation.
|
Aspect |
Detection Rule Testing |
Detection Rule Validation |
|
Purpose |
Ensure detection rules function correctly |
Evaluate and optimize the quality and performance of detection rules |
|
Process |
Examine functionality, configuration, and inputs |
Assess accuracy, effectiveness, efficiency, and coverage of rules using tools like BAS |
|
Examples |
Confirm rule-triggered alerts for specific malware |
Measure rule performance against realistic cyberattack scenarios, validate rule coverage against threat frameworks like MITRE ATT&CK |
|
Outcome |
Confirm rules are operating as designed |
Validate rules' ability to detect actual threats, optimize detection capabilities, proactive rule validation |
|
Tools |
Test environments, simulated inputs |
Breach and Attack Simulation (BAS) solutions, up-to-date threat libraries, Detection Rule Validation (DRV) solutions |
Integrating Detection Rule Validation (DRV) and Security Control Validation (SCV) for Enhanced Security
Integrating Detection Rule Validation (DRV) and Security Control Validation (SCV) can significantly enhance an organization's security posture.
SCV allows for the simulation of appropriate attack scenarios based on the rules set within the security framework. Security Control Validation (SCV) provides a practical, hands-on way to track and evaluate the effectiveness of the security controls in real-world conditions.
On the other hand, Detection Rule Validation (DRV) focuses on identifying any potential issues concerning the health of the detection rules. It scrutinizes the rule's logic, configuration, and performance to ensure it operates as intended and is capable of accurately identifying threats. Furthermore, actions related to Detection Analytics can be automatically monitored, providing real-time insights into the functioning of the rules.
In essence, the integration of DRV and SCV offers a holistic approach to security, where rules are not only validated but also tested against simulated attacks, ensuring a robust, resilient, and effective security framework.

Figure. Picus Detection Rule Validation.
In this section, we will talk about the main benefits of integrating DRV and SCV for enhanced security.
-
Comprehensive Assessment of Security Infrastructure
-
Quick and Continuous Optimization of Detection Rules
-
Resource Prioritization
-
Enhanced Visibility on Detection and Response Capabilities
Below, we provide a brief overview of each key benefit listed in this section.
a. Comprehensive Assessment of Security Infrastructure
Integrating DRV and SCV provides a more comprehensive analysis of the organization's security infrastructure. DRV evaluates the accuracy, effectiveness, and efficiency of detection rules, while SCV tests the organization's defenses against realistic threats by simulating real-world cyberattack scenarios, leveraging an up-to-date threat library.
b. Quick and Continuous Optimization of Detection Rules
The continuous feedback loop provided by the combination of DRV and SCV enables security teams to promptly identify and address issues with their detection rules, ensuring more accurate and effective responses to emerging threats.
c. Resource Prioritization
The integration of Detection Rule Validation (DRV) and Security Control Validation (SCV) serves as a strategic approach in managing cybersecurity resources. Security Control Validation plays a crucial role in identifying the most critical threats and vulnerabilities that the security rules need to address. This involves simulating various attack scenarios and observing the effectiveness of the existing rules in mitigating these threats.
On the other hand, Detection Rule Validation (DRV) focuses on the continuous monitoring and evaluation of the health status of these rules. It identifies any logical, configuration, or performance issues that could hinder the rules' effectiveness. By ensuring these rules are operating optimally, DRV contributes to accurate and reliable threat detection.
The combined use of DRV and SCV allows security teams to not only pinpoint and prioritize the most relevant risks but also ensure that the rules designed to address these risks are functioning correctly. This dynamic and comprehensive approach helps optimize the rule base, leading to a robust and responsive security framework.
d. Enhanced Visibility on Detection and Response Capabilities
The combination of DRV and SCV offers a holistic view of an organization's threat detection and response capabilities, providing insights into areas that need improvement and identifying potential blind spots in the security infrastructure.








