D3FEND refers to a comprehensive cybersecurity framework dedicated to enhancing Detection, Denial, and Disruption for Network Defense. Its primary aim is to address the gaps in an organization’s security posture, ranging from foundational system improvements to advanced detection techniques.
In this article, we'll delve deeply into the core components of the MITRE D3FEND matrix, explore the crucial role of the Digital Artifacts Ontology as a connective bridge between ATT&CK and D3FEND, and illustrate how a possible Process Hollowing attack (ATT&CK T1055.012) corresponds to its defensive technique (D3FEND D3-PCSV).
What Is MITRE D3FEND Matrix?
The D3FEND Matrix is a cybersecurity framework developed by MITRE Corporation, designed to offer a systematic approach to understanding and implementing defensive countermeasures against cyber threats. It complements the widely recognized MITRE ATT&CK framework, which outlines adversarial Tactics, Techniques, and Procedures (TTPs).
Whereas ATT&CK maps the adversarial tactics, techniques, and procedures (TTPs) in a framework, D3FEND provides guidance on how to defend against those specific adversarial actions
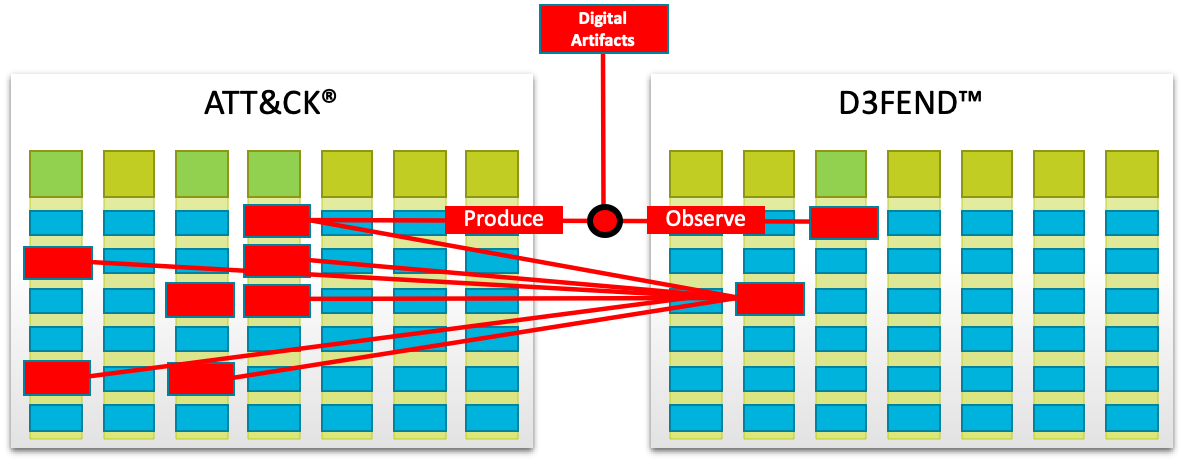
Figure 1: Bridging ATT&CK to D3FEND. Source: https://d3fend.mitre.org/about/
Why Do We Need the MITRE DEFEND Matrix?
The D3FEND matrix serves as a vital counterpart to the ATT&CK matrix, providing a structured framework for defensive measures against cyber threats. While the ATT&CK matrix meticulously outlines Tactics, Techniques, and Procedures (TTPs) employed by adversaries, the D3FEND matrix complements this by presenting a well-organized set of defensive countermeasures. This organized approach ensures that defense strategies are as robust and well-structured as the attack patterns they aim to prevent.
Although both matrices share a common goal of enhancing cybersecurity, their structures diverge to accommodate their respective focuses—attack versus defense. The D3FEND matrix aids organizations in pinpointing potential security vulnerabilities by aligning defensive measures against known attack methodologies outlined in the ATT&CK matrix. This dual-matrix approach fosters a comprehensive understanding of the cybersecurity landscape, thereby empowering organizations to bolster their security postures effectively.
Through the D3FEND matrix, organizations can systematically evaluate and improve the effectiveness of their defensive mechanisms, ensuring a balanced and well-rounded cybersecurity strategy. This structured approach to defense not only facilitates better threat mitigation but also promotes a culture of continuous improvement in cybersecurity practices.
MITRE D3FEND Matrix Explained
The MITRE D3FEND framework offers a structured approach to cybersecurity defense, categorized into five distinct tactics: "Harden," "Detect," "Isolate," "Deceive," and "Evict."
Each category comprises specific defensive techniques tailored to counteract threats. This framework:
-
Aids in understanding the capabilities of defensive technologies.
-
Provides insights into countermeasures and their limitations.
-
Fills the gaps in existing cybersecurity knowledge bases, such as the MITRE ATT&CK.
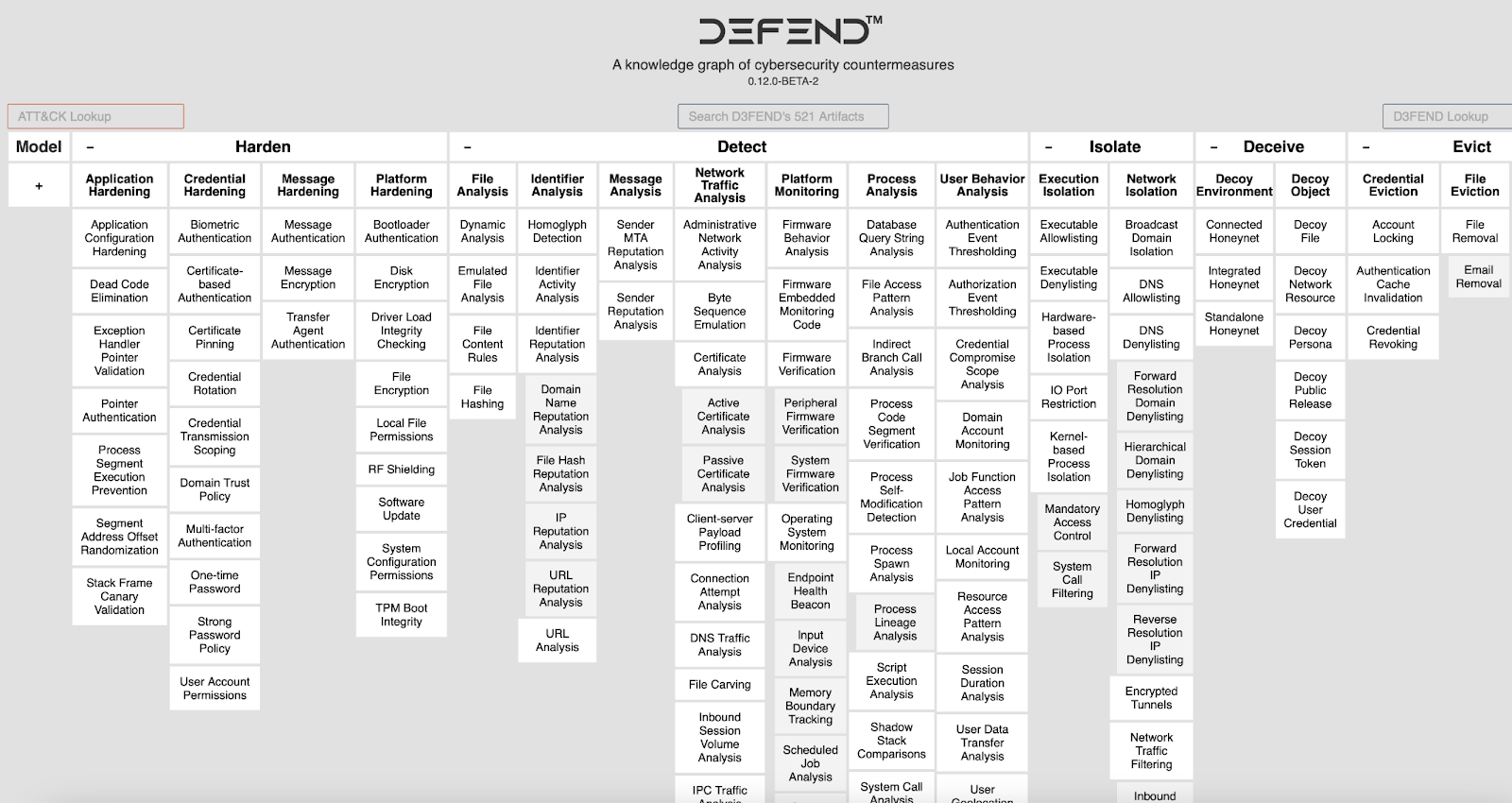
Figure 2. The MITRE D3FEND Matrix.
Below, we provide the overview of each D3FEND tactic given the matrix.
Harden
- Reduces attack surface.
- Focuses on application, credential, message, and platform hardening.
- Emphasizes on updating patches to reduce vulnerabilities.
Detect
- Analyzes threats in tandem with the MITRE ATT&CK framework.
- Encompasses file, identifier, message, network traffic, platform, process, and user behavior analysis.
- Utilizes SIEM solutions for defense against potential threats.
Isolate
- Focuses on segregating compromised/vulnerable hosts.
- Emphasizes execution and network isolation.
- Incorporates continuous traffic monitoring with IP and DNS filtering.
Deceive
- Employs decoying techniques for environment or specific objects.
- Diverts cyber attackers from the real environment to a decoy one.
Evict
- Concentrates on credential and process eviction.
- Aims to terminate vulnerable or compromised components for improved defense.
The D3FEND framework acts as a complementary approach to the ATT&CK framework and offers a robust model for defensive measures in cybersecurity.
How Does MITRE D3FEND Matrix Work?
The MITRE D3FEND framework operates alongside the MITRE ATT&CK, interconnected by an intermediate model termed "digital artifacts," depicted in Figure 3. This approach offers an intuitive understanding of why certain defensive techniques or countermeasures counter specific threats, offensive tactics, or system vulnerabilities.
What are Digital Artifacts?
Digital artifacts can be envisioned as evidence or traces left behind by offensive actions. By observing and analyzing these traces, defensive strategies can effectively counteract the threat.
In the following section, an example will further clarify the role of digital artifacts in bridging the ATT&CK and D3FEND frameworks.
From Attack to Defense: Mitigating ATT&CK TTPs with D3FEND
As depicted in the Figure 3,
-
The left side showcases the Offensive Model (ATT&CK).
-
The right side illustrates the Defensive Model (D3FEND).
-
The Digital Artifact Ontology acts as a bridge connecting these two matrices.
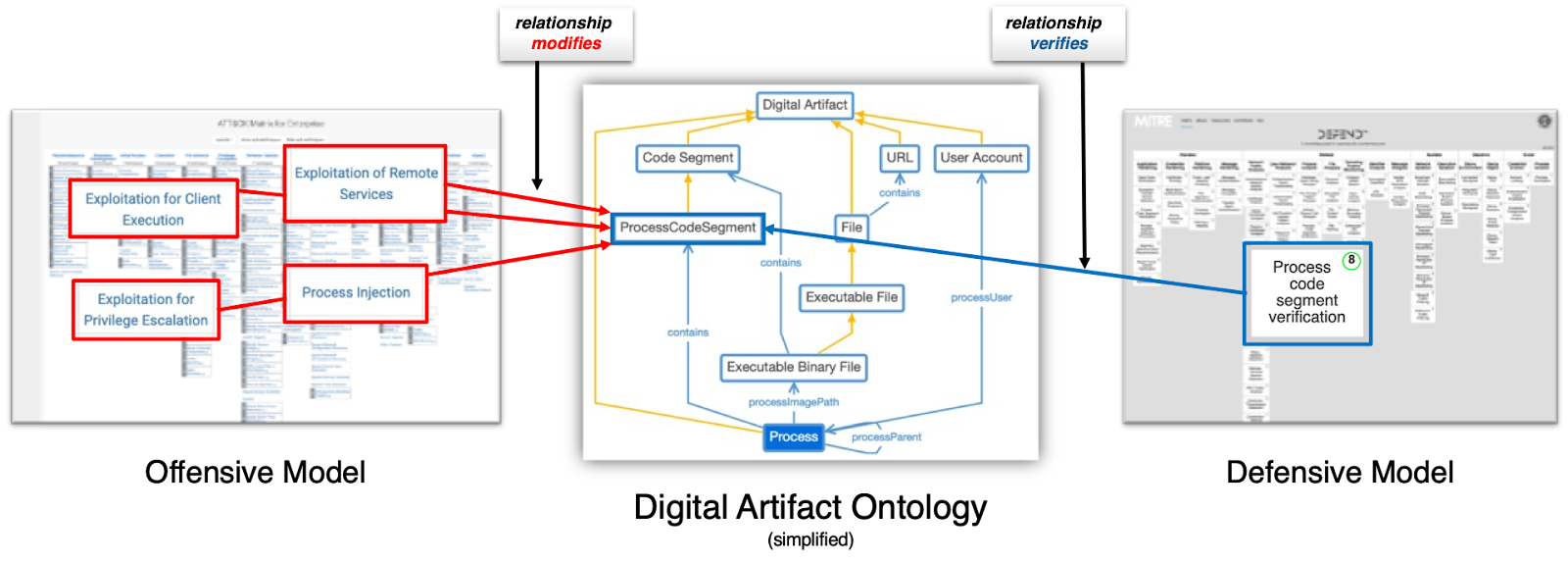
Figure 3. Digital Artifact Ontology, sourced from MITRE D3FEND.
Below, we explained each framework and the digital artifact ontology in great detail.
Offensive Model - Process Injection (ATT&CK T1055)
The Offensive Model represents the various offensive techniques adversaries might employ. Some of the techniques highlighted in the Fig. 3 include
-
Exploitation for Client Execution (ATT&CK T1203)
-
Exploitation of Remote Services (ATT&CK T1210)
-
Exploitation for Privilege Escalation (ATT&CK T1068), and
-
Process Hollowing (ATT&CK T1055.012)
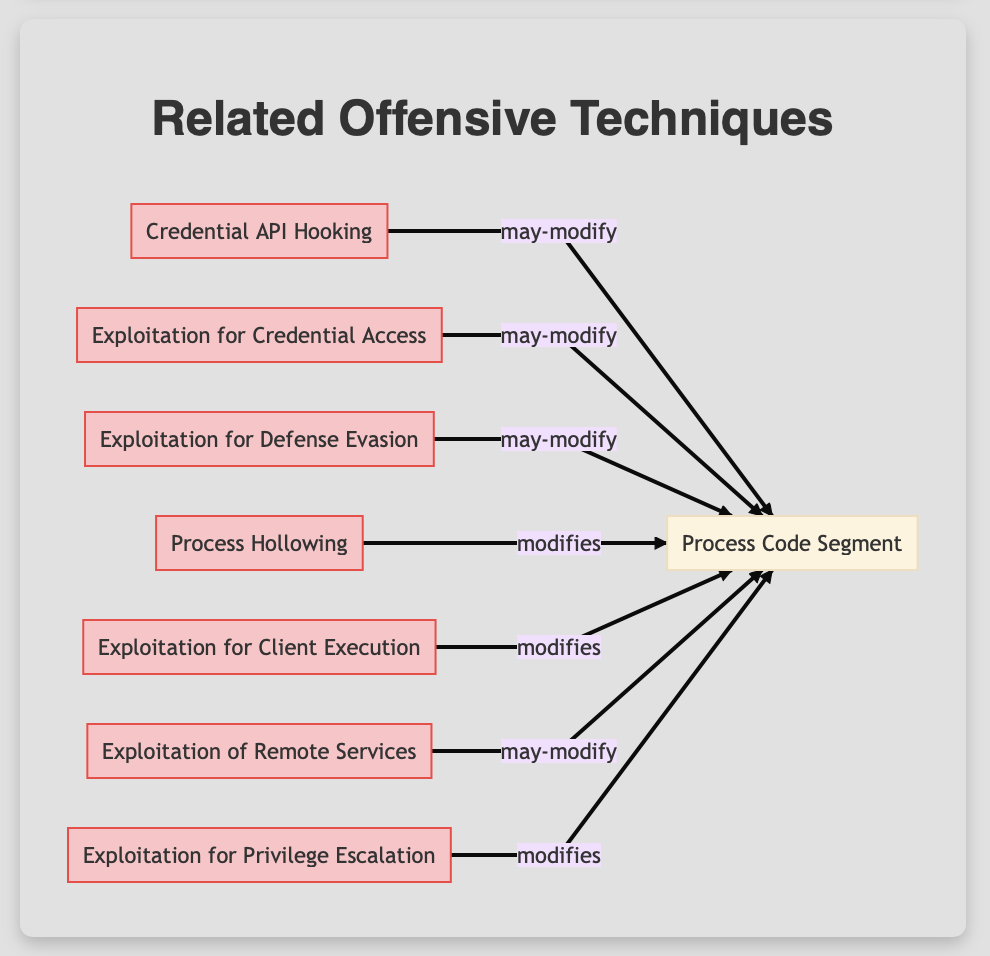
Figure 4. Related Offensive Techniques to the “Process Code Segment” Artifact.
Defensive Model - Process Code Segment Verification (D3FEND D3-PCSV)
Within the Defensive Model, the "Process Code Segment Verification" (D3-PCSV) technique is categorized under the "Detect" tactic, underlining its role in identifying potential threats. This technique emphasizes verifying a program's memory integrity, particularly its code segment.
A process code segment refers to a specific portion of a computer program's memory that houses the actual executable instructions. It’s like the list of orders that a computer must follow to run a program. If anyone tampers with this segment, it can change the way the program runs, potentially leading to malicious actions.
In the context of our example, it's highlighted that this segment can be altered through techniques like "Process Hollowing," which is a method used by attackers to insert or "inject" malicious code into running processes. By juxtaposing the current state of the process's memory with a known state, anomalies—potential indicators of malicious activities like process hollowing—are identified.
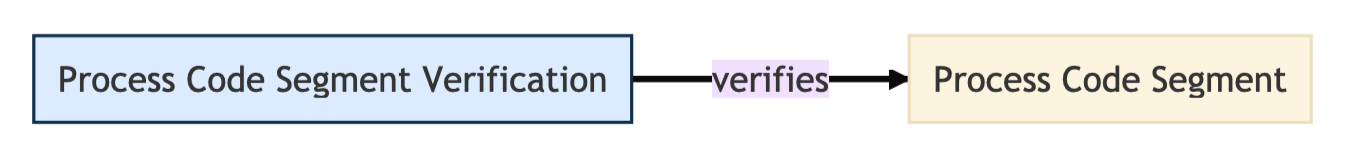
Figure 4. Process Code Segment Verification Defend Technique Sourced from D3FEND Matrix
For clarity, look at the following example.
-
Process Code Segment: This refers to the memory segment containing the machine code instructions of a running program. Various countermeasure techniques interact with this segment to detect and verify its integrity.
-
Memory Integrity Verification: By comparing the current code segment's hash with a known 'clean' hash, any alterations or tampering can be identified. Techniques such as "Asset Vulnerability Enumeration" and "Memory Boundary Tracking" play a crucial role in this verification.
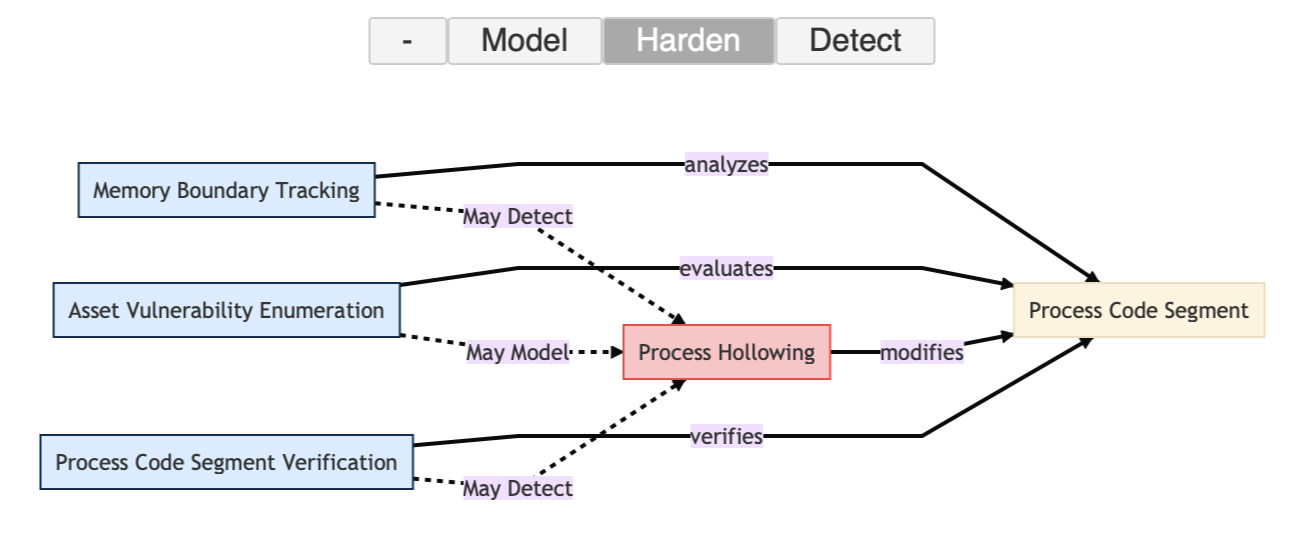
Figure 5. Hardening Against Process Hollowing Attack by D3FEND.
-
Protection Mechanisms: Enhancing memory defense mechanisms include Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR). However, certain adversarial techniques, notably process hollowing, have been designed to bypass these protective measures.
-
Process Hollowing: This is a covert attack technique where a legitimate process's memory is hollowed out and subsequently replaced with malicious code. It often remains undetected as it leverages genuine processes, modifying the process code segment directly.
-
Anomaly Indicators: Potential deviations or inconsistencies in memory patterns might emerge, indicating tampering or malicious activities.
-
Utility of Technique: The essence of these techniques lies in their capability for real-time detection of tampering. They are instrumental in identifying sophisticated attacks, thereby enabling swift and effective defensive responses.
Digital Artifact Ontology
Ontology refers to a structured framework that organizes and defines relationships between various concepts. When referring to the "Digital Artifact Ontology," we mean a system that organizes and maps different digital artifacts and their relationships to each other.
The term "ontology" can sometimes be confusing, but the D3FEND Lead Peter Kaloroumakis provides a simpler explanation.
Think of ontology as a sophisticated method of organizing information. A basic example is a simple list of definitions. A more complex example is a taxonomy, like the way we classify animals (e.g., a dog is a type of mammal, which is a type of animal). An ontology takes this further by allowing for multiple taxonomies and the relationships between them, forming a knowledge graph.
-
In this context, the "ProcessCodeSegment" is an example of a digital artifact.
-
It's a part of a larger structure where a "ProcessCodeSegment" is a type of "Code Segment," and that, in turn, is a type of "Digital Artifact."
-
These relationships form the ontology – a network of interconnected concepts.
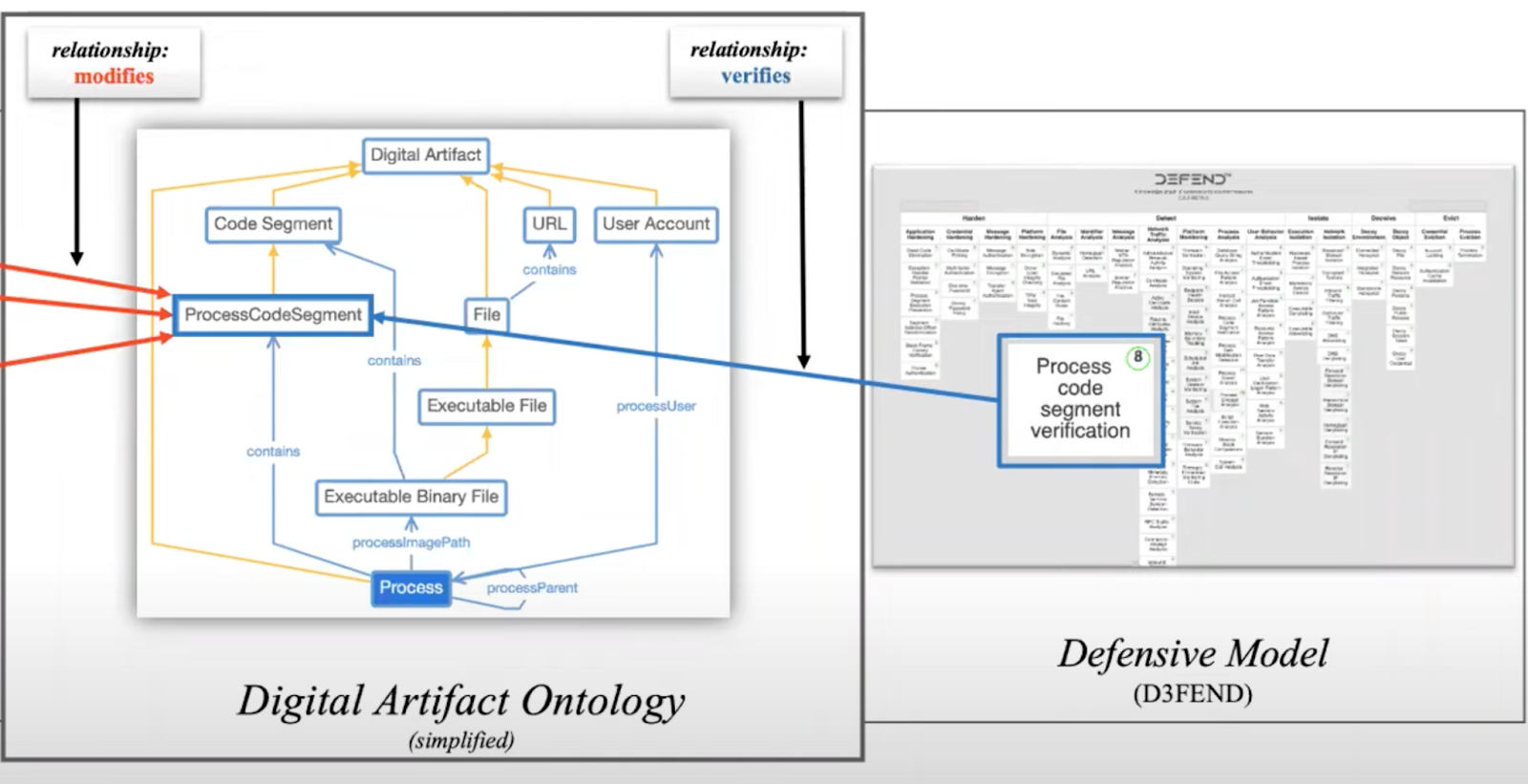
Figure 5. Digital Artifact Ontology, sourced from SANS Cyber Defense.
To simplify, the Digital Artifact Ontology serves as a bridge between offensive techniques, like process hollowing, and defensive techniques, such as process code segment verification.
By understanding this ontology, cybersecurity professionals can better grasp the complex interrelationships between different tactics, techniques, and processes in the cybersecurity realm. This knowledge aids in developing strategies for both attack and defense.








