The Top Ten MITRE ATT&CK Techniques
Picus 10 Critical MITRE ATT&CK Techniques
Welcome to the Picus Red Report 2025, which is based on in-depth research from Picus Labs, the research arm of Picus Security. As a result of the comprehensive analysis of hundreds of thousands of real-world threat samples collected from numerous sources, Picus Labs revealed the most prevalent ATT&CK techniques and tactics to help you focus on what significantly improves your security.

|
The Red Report 2025
|
Executive Summary
Picus Labs processed more than 1 million pieces of malware collected between January and December, 2024 to reveal a comprehensive view of the latest tactics, techniques, and procedures being employed by adversaries across the planet. Each detected TTP was classified via the MITRE ATT&CK ® Framework, which resulted in the identification of over 14 million malicious actions. This provided Picus with extremely granular insight into the most commonly deployed techniques, shedding light on critical information concerning these constantly shifting attack strategies. Among these, the most striking is that this year’s Red Report reveals that malware, specifically strains targeting credential stores, increased from 8% in 2023 to 25% in 2024. This tripling in prevalence gives a glimpse into the popularity and success of this emerging threat.
The Red Report also reveals that 93% of 2024’s malicious actions were carried out using the top ten MITRE ATT&CK techniques. These findings will help security teams make better-informed decisions and concentrate on defending against the most prevalent threats in today's cyber environment.
Key Findings
The Rise of Perfect Heists:
Sophistication Meets Coordination
Today’s threats are about complex, multi-staged, structurally complex attacks, like "The Perfect Heist" perpetrated by the SneakThief malware. Featuring a combination of stealth, automation, and persistence, attackers can intrude into network systems, neutralize defenses, exfiltrate sensitive information, and remain hidden for longer periods. Attackers' ability to tailor their tactics to their surroundings speaks to a move toward precision-centric campaigns that work to create maximum destruction with minimum exposure.
Dominance of the Top 10 Techniques:
93% of Malicious Actions Linked to Top Techniques
MITRE’s top 10 techniques accounted for an astonishing 93% of the total malicious activity in 2025. T1055 Process Injection was the most prevalent, closely followed by T1059 Command and Scripting Interpreter. Other techniques, such as T1555 Credentials from Password Stores and T1071 Application Layer Protocol, now make up parts of the attack chains using stealth, persistence and automation to succeed.
Malware Complexity Reaches New Heights:
14 Malicious Actions per Malware
Malware now performs an average of 14 malicious actions and 12 ATT&CK techniques per sample, presenting an evolving level of sophistication along with a notable increase in attackers’ ability to orchestrate different techniques and methods, thus further increasing the level of complexity needed for detection and defense.
Stealth Techniques Continue to Dominate:
Evasion and Persistence at the Core of Attacks
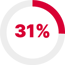
T1055 Process Injection, seen in 31% of analyzed samples,shows further movement to stealthier approaches as code injected into a legitimate process evades detection in many security solutions. In addition, T1059 Command and Scripting Interpreter stands out among the top techniques that let attackers conduct malicious operations through native tools, such as PowerShell and Bash.
Credential Theft Fuels Lateral Movement:
Handing Over the Keys to the Kingdom
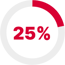
Credential theft remains one of the most dependable techniques within adversary playbooks, with T1555 Credentials from Password Stores appearing in 29% of malware samples analyzed. A growing trend in credential theft targets password managers, browser-stored credentials, and cached login data to gain lateral movement and afford attackers elevated privileges to sensitive systems. Those stolen credentials are later used for lateral movement and privilege escalation, allowing attackers to broaden their reach within the environments they’ve compromised.
Encrypted Communication Becomes Standard:
The Whispering Channels
Adversaries have generally upped their game by relying on encrypted communication methods such as HTTPS and DNS over HTTPS (DoH) while exfiltrating data or communicating with C2 servers. These "whispering channels" thus allow attackers to mask malicious traffic within legitimate network traffic patterns that bypass traditional monitoring tools. And this is where ransomware has now changed into more of a multi-stage operation involving encryption but going way beyond it.
Ransomware Evolves into a Multi-Stage Operation:
To Data Encryption, and Beyond
T1486 Data Encrypted for Impact stays near the top of this year’s list as ransomware operators keep innovating their tactics. Threat actors are increasingly coupling encryption with advanced data exfiltration by using the T1071 Application Layer Protocol to effect double extortions. Many of the most destructive high-profile ransomware attacks of 2024 and 2025 were campaigns that moved into critical infrastructure at high-value organizations with increasing regularity.
Persistence Techniques Ensure Long-Term Access:
Boot or Logon Autostart Execution on the Rise
T1547 Boot or Logon Autostart Execution is increasingly one of the leading methods by which malware outlives system reboots and removal attempts. Given the fact that SneakThief leveraged this, the trend of persistence-focused hackers gaining ground in hacked networks for longer terms isn’t likely to be going anywhere anytime soon.
Real-Time Data Theft Accelerates:
Input Capture and System Discovery
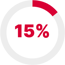
Attackers leveraged T1056 Input Capture and T1082 System Information Discovery to accelerate data theft in real-time from their targeted organizations. Along these lines,, infostealers employed keyloggers, screen capture utility, and audio interceptors for monitoring the activities at FinexaCore while keeping pace or outpacing the organization’s defensive efforts.
State-Sponsored Espionage Campaigns Intensify:
Advanced Persistent Threats on the Rise
T1082 System Information Discovery continues to be popular, and the growing trend of T1071 Application Layer Protocol outlines the continuing rise in cyber espionage campaigns. In 2024, threat actor groups such as APT29 from Russia, Volt Typhoon from China, and Lazarus Group from North Korea were targeting critical infrastructure, government agencies, and private enterprises with fresh resolve. Such campaigns emphasize long-term access, and data theft to further their geopolitical objectives.
MITRE ATT&CK Framework
MITRE ATT&CK is an open-source knowledge base of adversary tactics and techniques based on real-world observations. ATT&CK provides a common taxonomy of tactics and techniques to better classify adversary behaviors. While a tactic specifies a goal that an adversary is trying to achieve, a technique represents how an adversary accomplishes the tactic by performing an action.
The MITRE ATT&CK Matrix for Enterprise [1] consists of 14 tactics: Reconnaissance, Resource Development, Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration, and Impact. There may be many techniques to achieve a tactic, so there are multiple techniques in each tactic category. Similarly, a technique may be categorized into multiple tactics. For example, the Process Injection technique is used by attackers for Defense Evasion and also Privilege Escalation. Currently, the ATT&CK Enterprise Matrix includes 201 techniques and 424 sub-techniques.
Methodology

Between January 2024 and December 2024, Picus Labs conducted an extensive analysis of 1,094,744 unique files, of which 1,027,511 (93.86%) were classified as malicious. These files were collected from a diverse range of reliable sources, including commercial and open-source threat intelligence services, security vendors, independent researchers, malware sandboxes, malware databases, and online forums. This comprehensive approach ensured a robust and representative dataset of real-world threats.
From the identified malicious files, 14,010,853 malicious actions were detected, averaging approximately 14 actions per malware sample. These malicious actions were systematically mapped to the MITRE ATT&CK framework, resulting in a total of 11,984,156 ATT&CK techniques being identified. On average, each malware sample exhibited 12 distinct techniques, with many malicious actions corresponding to a single technique. This mapping process provided a granular view of how adversaries leverage specific techniques to achieve their objectives.
To compile the Red Report 2025 Top Ten, Picus Labs researchers focused on identifying the most prevalent techniques used by adversaries. For each technique, the number of malicious files employing it was calculated and expressed as a percentage of the total malicious files analyzed. For instance, the T1055: Process Injection technique was observed in 314,088 malware samples, representing 31% of the 1,027,511 malicious files in the dataset. This method allowed researchers to rank techniques based on their prevalence, ensuring the report highlights the techniques most widely used by attackers in real-world scenarios.
By leveraging this data-driven approach, the Red Report provides actionable insights into the most frequently observed adversary behaviors, enabling organizations to better prioritize their defenses against the techniques most likely to target them.
Picus 10 Critical MITRE ATT&CK Techniques
The most prevalent ATT&CK techniques identified in 2024 are ranked by the percentage of malware samples exhibiting each behavior. Click on a technique to explore its details: how to simulate it (red team exercise), how to detect and mitigate it (blue team exercise), and which threat actors and malware leverage it against specific targets.
|
|
#1
|
|
T1055 Process Injection
|
|
|
#2
|

|
T1059 Command and Scripting Interpreter
|
|
|
#3
|
|
T1555 Credentials from Password Stores
|
|
|
#4
|

|
T1071 Application Layer Protocol
|
|
|
#5
|
|
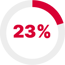
T1562 Impair Defenses
|
|
|
#6
|

|
T1486 Data Encrypted for Impact
|
|
|
#7
|

|
T1082 System Information Discovery
|
|
|
#8
|
|
T1056 Input Capture
|
|
|
#9
|

|
T1547 Boot or Logon Autostart Execution
|
|
#10
|
|
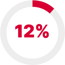
T1005 Data from Local System
|
Comparison With Other Top ATT&CK Techniques Lists
Apart from our report, there are valuable studies on top ATT&CK techniques. The following table presents the top 10 lists prepared by Red Canary [2], MITRE CTID [3], and Mandiant [4] and the common techniques between these lists. In these lists, various techniques will be listed differently, but diversity does not necessarily signify inaccuracy or incompleteness. Since different methodologies and threat samples were used when creating the lists, it is natural to see different results.
 |
|
|
|
|
|
1 |
T1055 - Process Injection |
T1059.001: Command and Scripting Interpreter: PowerShell
|
T1059 - Command and Scripting Interpreter
|
T1059 - Command and Scripting Interpreter
|
|
2 |
T1059 - Command and Scripting Interpreter
|
T1059:003 - Command and Scripting Interpreter: Windows Command Shell
|
T1078 - Valid Accounts
|
T1027 - Obfuscated Files or Information
|
|
3 |
T1555 - Credentials from Password Stores
|
T1047 - Windows Management Instrumentation
|
T1021 - Remote Desktop Protokol
|
T1083 - File and Directory Discovery
|
|
4 |
T1071 - Application Layer Protocol
|
T1078.004 - Valid Accounts: Cloud Accounts |
T1047 - Windows Management Instrumentation
|
T1021 - Remote Services
|
|
5 |
T1562 - Impair Defenses
|
T1027 Obfuscated Files or Information
|
T1490 - Inhibit System Recovery
|
T1082 - System Information Discovery
|
|
6 |
T1486 - Data Encrypted for Impact
|
T1114.003 - Email Collection: Email Forwarding Rule
|
T1105 - Ingress Tool Transfer
|
T1070 - Indicator Removal
|
|
7 |
T1082 - System Information Discovery
|
T1003 - OS Credential Dumping
|
T1083 - File and Directory Discovery
|
T1071 - Application Layer Protocol
|
|
8 |
T1056 - Input Capture
|
T1218.011 - System Binary Proxy Execution: Rundll32
|
T1486 - Data Encrypted for Impact
|
T1033 - System Owner/User Discovery
|
|
9 |
T1547 - Boot or Logon Autostart Execution |
T1105 - Ingress Tool Transfer
|
T1190 - Exploit Public-Facing Application
|
T1140 - Deobfuscate/Decode Files or Information |
|
10 |
T1005 - Data from Local Systems
|
T1036.003 - Masquerading: Rename System Utilities
|
T1489 - Service Stop
|
T1190 - Exploit Public-Facing Application
|
Limitations
The limitations outlined below are imperative to consider when interpreting the Red Report 2025:
-
Sample Size Representation: Despite analyzing an extensive dataset of over 1,000,000 malware samples, it encompasses a subset of the vast malware landscape. This limitation may introduce a bias in the visibility of malware types and behaviors.
-
Focus on Post-Compromise Tactics: Our research focused primarily on post-compromise activities, thus excluding TA0043 Reconnaissance, TA0042 Resource Development, and TA0001 Initial Access techniques. Understanding that these initial access techniques such as T1566 Phishing and T1190 Exploit Public-Facing Applications were not covered is critical, as they are crucial steps in the attack chain.
Reflecting on these points provides a balanced view of the findings, acknowledging the scope of analysis while recognizing aspects not addressed within the study.
Conclusion
This research has shown that the Top 10 ATT&CK techniques account for 93% of observed malicious actions, with a significant rise in credential-focused malware. Sophisticated adversaries are increasingly deploying info stealers, a type of malware referred to as "SneakThief," which employs multi-stage infiltration, process injection, encrypted communications, and persistence techniques to infiltrate systems and exfiltrate sensitive data without detection. The surge in credential-targeting malware from 8% in 2023 to 25% in 2024 highlights the growing effectiveness and prevalence of this threat.
Cyber threat actors continue to develop advanced tools and refine existing techniques, with credential access becoming a primary focus. Effective mitigation of these threats requires proactively challenging security controls by employing the very same techniques adversaries use, but in a safe and non-destructive manner. This approach allows security teams to uncover security vulnerabilities, evaluate their defenses, and strengthen their security posture by addressing identified gaps.
The Picus Security Validation Platform empowers organizations to safely test their security controls in production against thousands of real attack techniques, including those leveraged by info stealers like the SneakThief type of malware. By identifying and addressing gaps with actionable prevention signatures and detection rules, organizations can protect against adversarial TTPs, maximize the effectiveness of their security investments, quantify risks, and enhance their overall resilience.
References
[1] "Matrix - Enterprise." [Online]. Available: https://attack.mitre.org/versions/v16/matrices/enterprise/
[2] "Top ATT&CK® Techniques - Red Canary Threat Detection Report," Red Canary, Mar. 11, 2024. Available: https://redcanary.com/threat-detection-report/techniques/.
[3] "Top 15 Techniques — Sightings Ecosystem v2.0.0 documentation." Available: https://center-for-threat-informed-defense.github.io/sightings_ecosystem/top-15-techniques/.
[4] "M-Trends 2024 Special Report,” Mandiant. Available: https://www.mandiant.com/m-trends.





.png?width=353&height=200&name=rr25-Blog-7-data-from-local-system%20(1).png)

.png?width=353&height=200&name=rr25-Blog-5-Impair-Defenses-11%20(1).png)




