Do you utilize your security controls
at their maximum?
How well an enterprise utilizes its security control stack depends on factors such as the level of skill set, cybersecurity maturity, infrastructural complexity, awareness, executive-level engagement and others.

Cyber Attack Readiness is a never-ending race, not a state
There are no hard and fast rules against cyber threats. Once investments are deployed, and solutions are implemented, new and evolving threats will undermine your security posture. Misconfigurations and control gaps can appear any minute.
Our solution
Build Organizational Capabilities for Optimizing Security Investments and Achieving Cyber Attack Readiness
250+
Customers trust Picus Solutions globally
80+
Channel Partners
15+
Mitigation focused technology alliances
Achieve Proactive Security through Automation & Rich Adversarial Context
Completely hassle free automation capabilities of Threat Emulation Module allow Picus users to test thousands of adversarial scenarios in the matter of hours across their entire network, web, email and endpoint security estate. Picus Mitigation Library points to the quickest fixes for the identified gaps specific to customer environments.
Picus Threat
Library
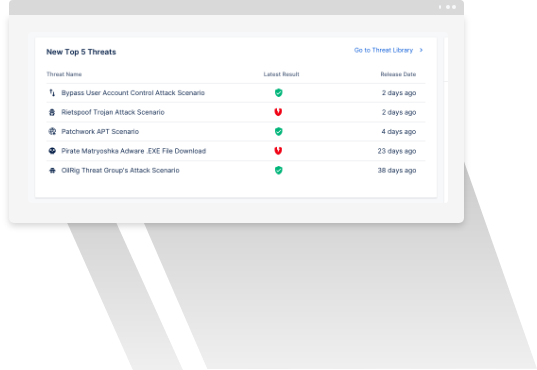
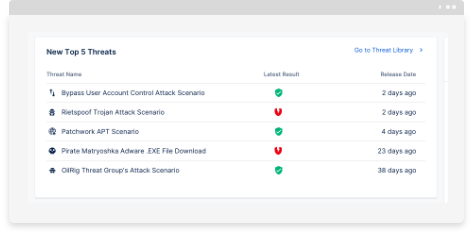
The proprietary threat library maintained by Picus Labs is the essence of the Picus Validation Platform. Undertaking Global Threat Watch, Imminent Threat Analysis and Commonality Evaluation processes, Picus Security Validation tools provide thousands of real-world threat samples and scenarios that best represent the threat landscapes around the clock. Picus Labs ties all threat library content to MITRE ATT&CK with over 90% coverage, cyber kill-chain and OWASP frameworks.
Picus Threat
Emulation Module
The Picus Threat Emulation Module assesses the “readiness level” of network, web application, endpoint and email security controls in production networks, either being in operation 24x7 or on-demand when required. Picus Threat Emulation Module is categorically safe, technology agnostic, requires limited deployment effort and fully automated.
Picus Mitigation
Library
Picus Mitigation Library contains industry wide security policy insights for different security technologies based on the technology alliances Picus Security formed. It provides specific next-generation firewall, network intrusion prevention systems, and web application firewalls mitigations for the technologies of its alliance partners. For EDR and SIEM related mitigations provided by the library, please refer to Detection Analytics & Mitigation.
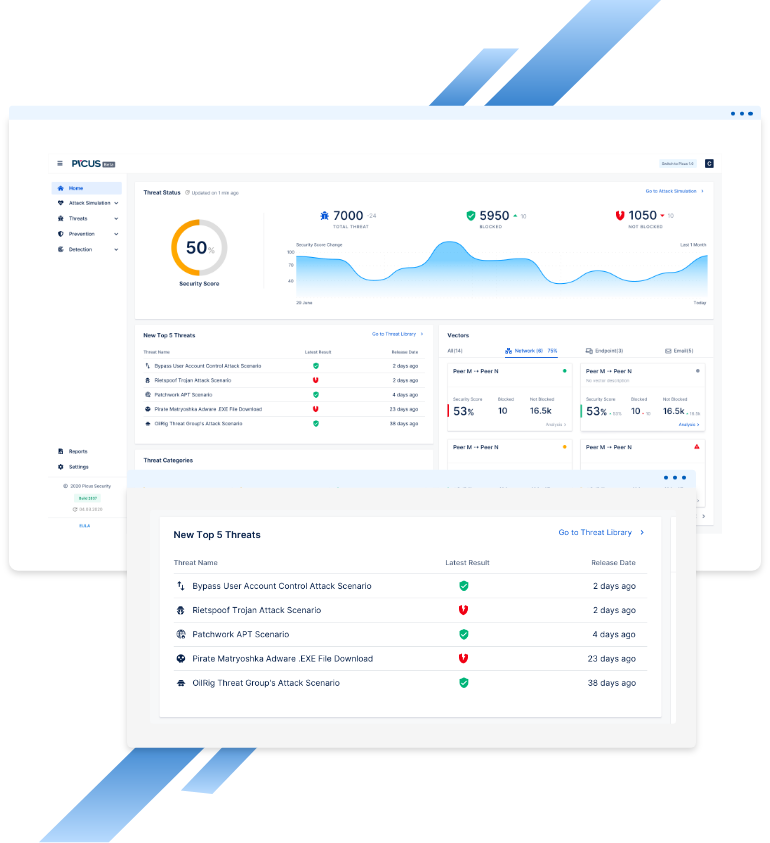
Continuous Security Validation
Continuous security validation allows teams to harden and maintain a strong security baseline. Any security posture can be weakened by evolutions in the outer threat landscape. But insider events such as change or transformation are just as relevant.
Change is necessary for business agility and performance, and it needs to be managed. By constantly and automatically measuring level of exposure to cyber risk and the associated degree of readiness, continuous validation allows to eliminate potential gaps resulting from change management or misconfiguration.


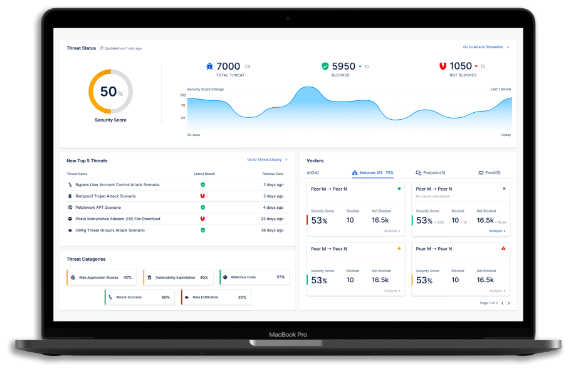

Augment Red & Blue Team Practices
Whether you are an organization attempting to measure cyber risk or a partner providing red team or blue team services, snapshot validation exercises can help protect yourself or your customers. On-demand use of Picus Threat Library, Picus Threat Emulation Module and Picus Mitigation Library triad, delivering a complete cyber kill chain service that ranges from threat development to validation and mitigation.
Measure the impact of attacks on core business functions and critical infrastructure. Identify gaps in your security estate and collect instant results.
Save costs through a time limited exercise.

