Micro Emulation Plan Testing
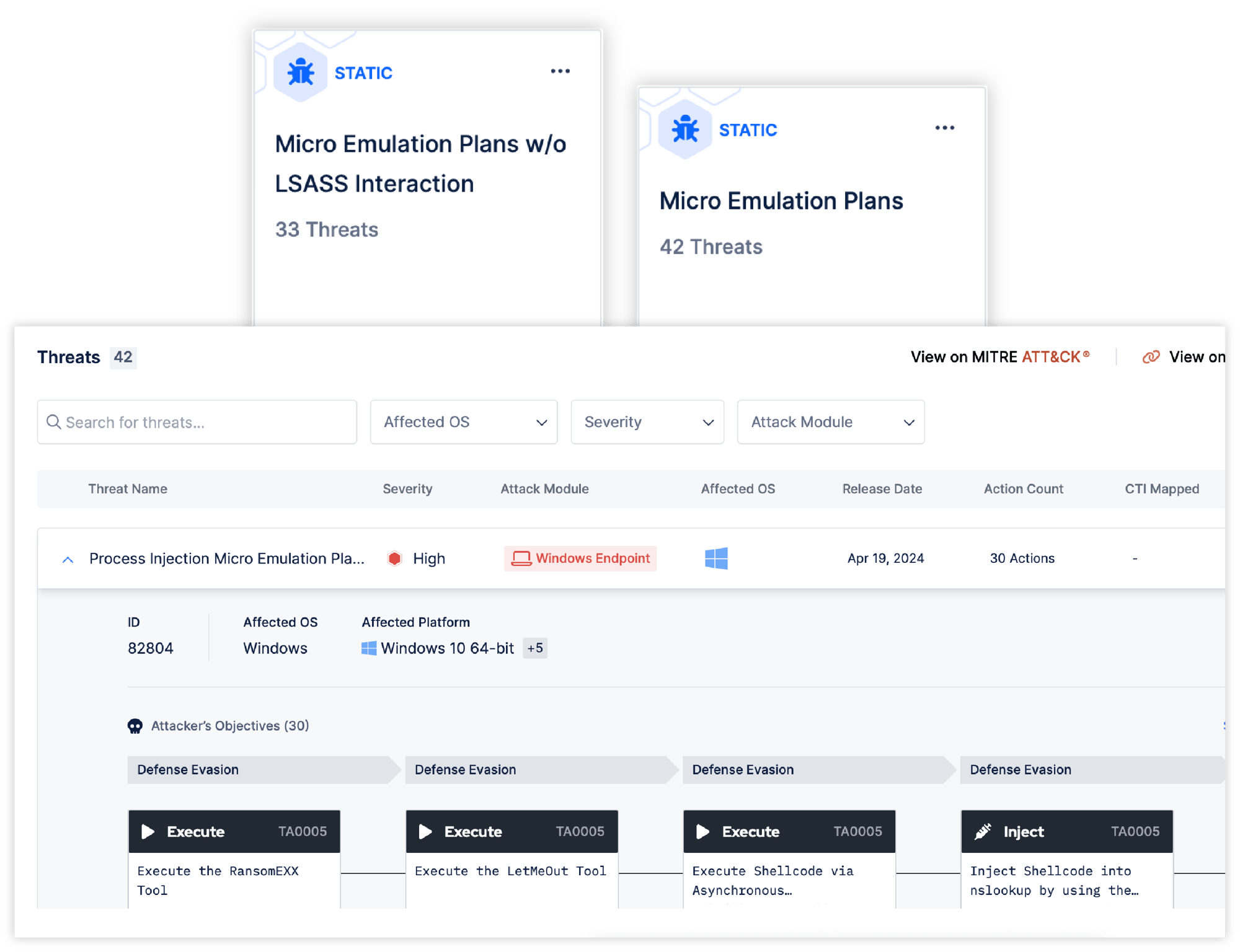
Picus Micro Emulation Plans validate endpoint defenses by simulating specific MITRE ATT&CK techniques through real-world atomic behaviors. Assess how effectively your XDR, EDR, and SIEM detect and respond to targeted attacker activity.
Why Validate Endpoint Defenses with Micro Emulation?
Advanced threats often slip through overlooked gaps in endpoint defenses. That’s why validating your XDR, EDR, and SIEM is essential. Even well-configured tools can miss critical behaviors. Micro Emulation Plans let you easily simulate advanced techniques seen in the wild to test prevention and detection coverage.
- Atomic techniques go undetected – Point-in-time testing can overlook specific attack steps that bypass detection.
- Detection rules drift over time – Updates, policy changes, or misconfigurations can reduce visibility without alerting teams.
- Manual testing isn’t scalable – Simulating every technique across users and systems is too resource-intensive to manage manually.
- Micro Emulation keeps defenses tuned – Picus Micro Emulation Plans simulate isolated, real-world adversary techniques mapped to MITRE ATT&CK, helping you pinpoint and fix detection gaps in your endpoint security stack.
Test Endpoint Defenses Against Techniques from Real-World Intrusions
Picus Micro Emulation Plans strengthen detection by simulating real-world atomic behaviors mapped to specific MITRE ATT&CK techniques—like LSASS dumping under Credential Dumping. These focused actions help validate how well your endpoint tools detect adversary tactics, with minimal setup and no manual scripting.
Test against advanced behaviors such as DLL Side-loading, Process Injection, and Active Directory enumeration.
Continuously monitor how detection capabilities evolve across updates and policy changes.
Simulate techniques seen in real-world endpoint intrusions by advanced threat actors, APT groups, and malware campaigns.
Identify blind spots in your XDR, EDR, and SIEM coverage before attackers exploit them.
Execute safe, non-disruptive tests in live environments to validate defenses confidently.

.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.