Identifying External Shortcomings that may be Affecting SOC Operations
Effectiveness of a SOC platform depends on many external factors, such as the log collection scope and consistency in a network. Based on the available internal and adversarial context, SOC teams work hard to swiftly detect all indicators of compromise, assign the right priorities, and take actions. This process requires aligning vast numbers of people, processes, and technologies. Regardless of how next-gen or automated a platform is, if a reliable detection validation process is not established, identifying shortcomings is impossible.
Blue Teaming in Dark is Ineffective
SOCs sit at the heart of Blue Team operations. Validating SOC or Blue Team efficacy is primarily driven by deploying offensive security practices such as Red Team or penetration test. These solutions come with their limitations concerning adversarial scope, repeatability, budget consumption, and use of time, while SOC teams need to have sustained visibility on logging and alerting capabilities about the adversarial context.
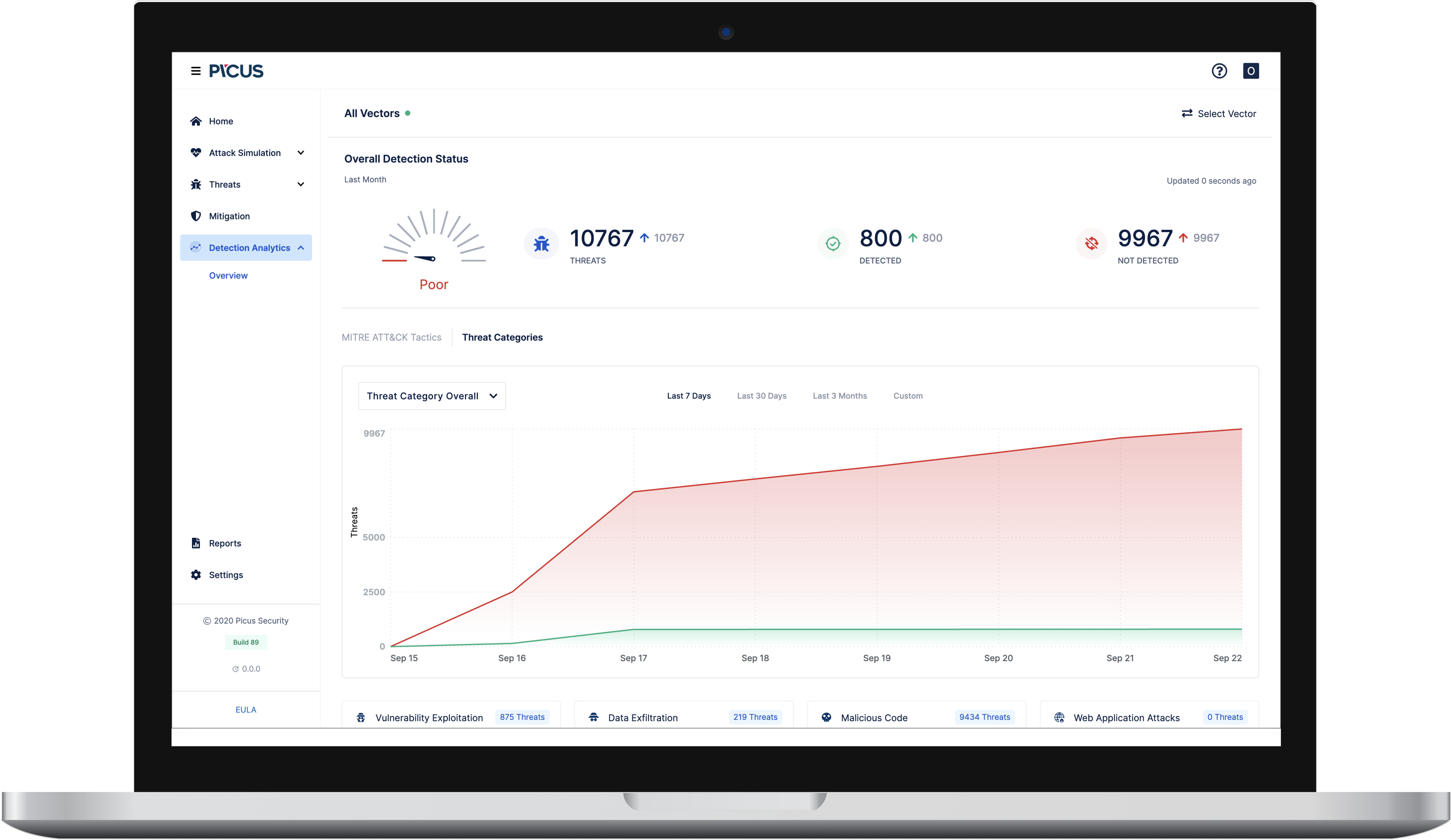


Picus Detection Analytics Module Brings Context as no Other
Picus Detection Analytics is an automated module that queries SIEM and EDR security logs to find the difference between the available events and expected events. Every emulated threat and adversary technique create a log in the relevant security controls should these emulations be detected or prevented. Querying SIEM and EDR platforms in customer environments, the Detection Analytics module matches query findings using advanced algorithms, with the real threat samples and techniques emulated by Picus Threat Emulation Module. As a result, undetected, unlogged, and non-alerted attacks are identified on the spot.
Detection Analytics has an intelligent 24x7 modus operandi. It utilizes the most extensive adversarial context, covering more than 90% of the MITRE ATT&CK techniques and the largest number of malware, vulnerability exploits, and web application attacks samples, thanks to Picus Threat Library.
Aligning Defensive Efforts Across the Board
Picus Detection Analytics provides the peace of mind SOC teams need by:
- Validating if the log mechanisms work across the whole network consistently
- Revealing the detection capabilities and configuration problems of the security stack
- Assessing and enhancing the alerting capabilities of SIEM platforms
- Decreasing the dwell time
- Making residual risk visible to all stakeholders
- Making evidence-based decision making possible
- Increasing the detection capabilities of security controls by instrumenting Picus Mitigation Library
- Being in operation around the clock


Seamlessly Integrates with your Infrastructure
Picus Detection Analytics is no ordinary detection validation technology. It is designed to provide minimal to zero false positives thanks to its comprehensive analytics capabilities brought by the proprietary Picus Dictionary. Its unique integration with content-rich Picus Mitigation Library makes vendor-specific EDR and SIEM detection policy improvements easy and possible. Current detection and response related technology alliance partners are IBM, Splunk, and VMware Carbon Black.

