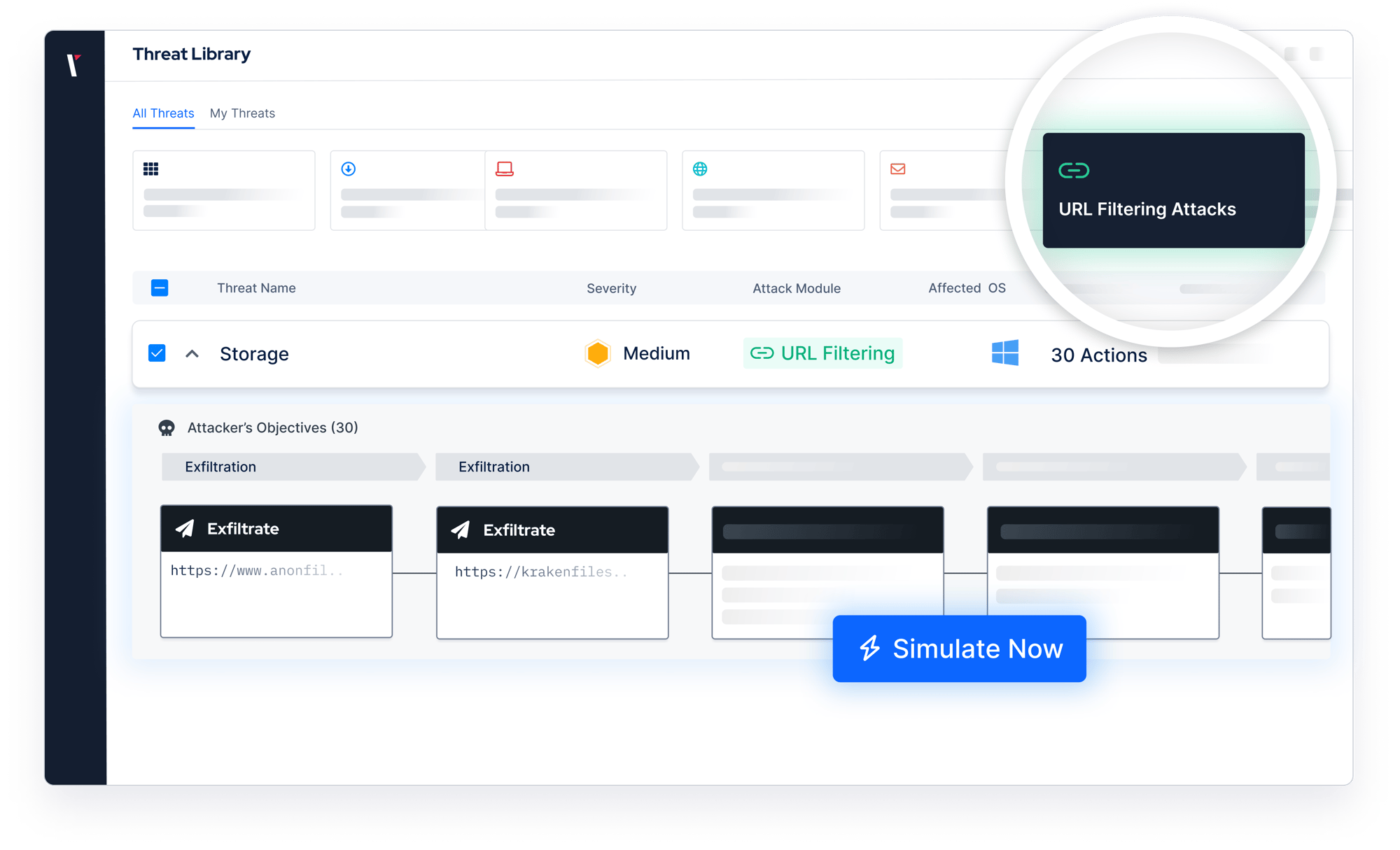
URL Filtering Testing
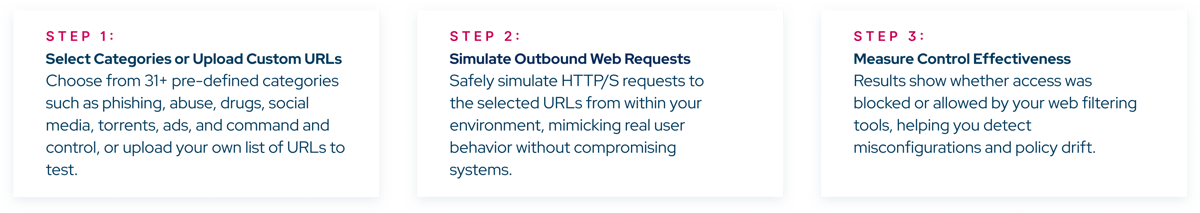
Picus URL testing module safely simulates outbound HTTP/HTTPS requests to harmful, malicious, or objectionable websites to test whether those requests are correctly blocked.
Why Validate Your URL Filtering?
Blocking access to harmful websites is a critical layer of defense. But URL filtering controls can quietly break down, exposing users to phishing, malware, and policy violations. Without ongoing validation, even the most advanced filtering technologies can fail to catch what matters.
-
Objectionable sites slip through – New or unclassified domains often bypass filters and introduce risk.
-
Policies degrade quietly – Misconfigurations, exceptions, and updates can weaken your defenses over time.
-
Manual URL testing is unrealistic – Security teams can’t keep up with thousands of risky and constantly emerging domains.
-
Automation keeps filters sharp – The Picus URL Filtering Testing Module simulates access to real malicious and inappropriate sites across 31 categories, confirming whether your controls block what they should.
Improve Web Access Control
with Automated URL Filtering Tests
Picus URL Filtering Testing Module strengthens defenses by simulating outbound access to malicious and inappropriate websites. Validate URL filtering policies across 31 categories including abuse, drugs, social media, torrents, booking sites, command and control, redirects, ads, and more. You can also test any custom URL list to ensure your controls block what they should, without manual effort.
Test against 31+ risk categories including phishing, abuse, drugs, and more.
Uncover gaps before users reach harmful or inappropriate sites.
Ensure your policies cover the URLs that matter to your organization.
Schedule recurring tests to maintain consistent control effectiveness.
Simulate access to newly discovered domains and malicious sites.
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.