Cyber Crime Turns Cyber Racket - Tackling Ransomware Before It Hits
LAST UPDATED ON DECEMBER 12, 2024
EXECUTIVE SUMMARY
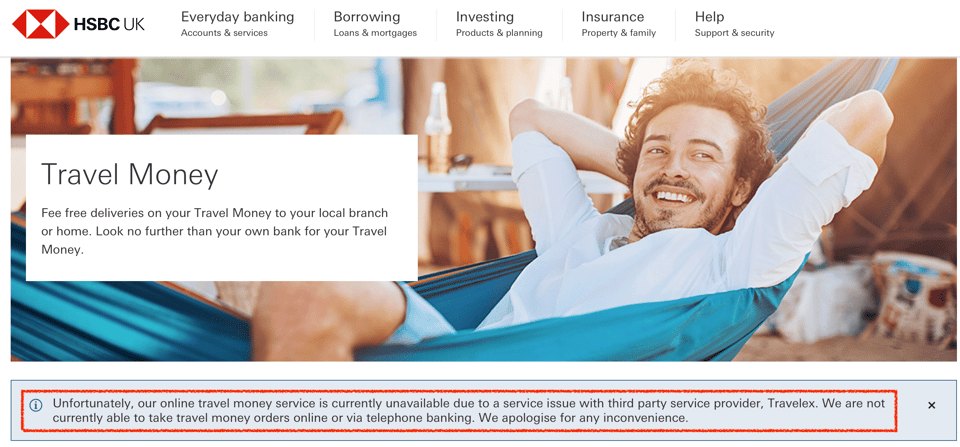
On New Year's Eve, foreign currency exchange provider Travelex took all its systems offline following a ransomware attack. Although more than a week has passed since the incident, their websites, including travelex.com and travelex.co.uk, are still out of service. So, the ransomware attack has had a very high impact on Travelex. According to BBC , the threat actor demands a $6m ransom.
After the ransomware attack, Travelex took down its websites across 30 countries and resorted to using pen and paper in its retail locations. As of today, there is a “press release” and a “Purchase Funnel down” message on their websites.
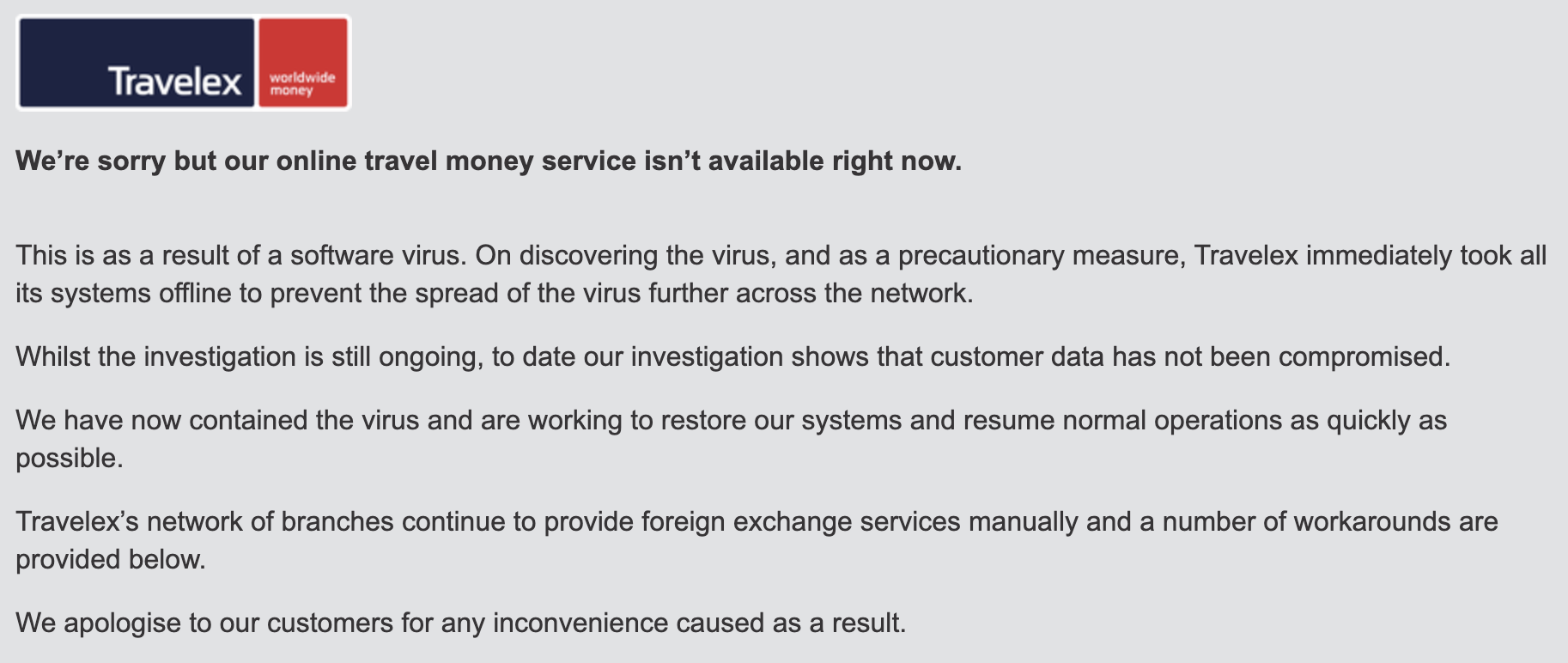
Not only Travelex, more than a dozen of the major banking players, including Lloyds Banking Group, Royal Bank of Scotland, HSBC, Barclay and Virgin Money, are reporting that their online foreign currency systems are down following Travelex. For example, HSBC UK stated that “our online travel money service is currently unavailable due to a service issue with third party service provider, Travelex”.
Travelex has confirmed that the ransomware is Sodinokibi which spreads using different methods, such as spearphishing emails, exploits and compromised websites. It encrypts files in the infected system and leaves a note demanding a ransom.
Lessons Learned
Up until a threat turns into a breach, it is just another threat among many others. This time the Travelex security team were the ones that were caught out, even though they have prevented thousands of threats so far. No security team should be judged by the one that got away.
The key capability for teams is to be able analyze a huge influx of l information, most of which will not be directly relevant. Any cybersecurity ecosystem must be empowered with the right tools to assess their breach preparedness and identify the relevant risks.
Confucius said “study the past if you would define the future”. Sodinokibi, for example, is not a new malware. We have seen it before. It has been attributed to a series of high-profile attacks since April 2019. If breached companies had previously tested themselves against a possible Sodinokibi attack and remediated the gaps in their defensive controls, they would have been better prepared for the attack.
Since the first time Sodinokibi appeared in April 2019, Picus users have been able to test their network and client security systems' effectiveness against it, inoculating them against infection. Picus simulates delivery of dozens different Sodinokibi samples over different channels to test your network security devices.
Do you want to know if your current enterprise security devices are blocking these types of attacks? Contact us at demo@picussecurity.com. Don’t hesitate. Let us show you within just a few hours, we can quickly report to you if your network security systems are protecting you against Sodinokibi and other prominent cyber attacks!
HOW TO PREVENT RANSOMWARE ATTACKS
The quickest way to prevent ransomware attacks is blocking their initial access to your system. If you can avoid it, you should not download suspicious attachments in emails, and files from suspicious links. However,it is likely that someone will download that file, especially in large companies. That’s why companies use security solutions focused on detecting previously known attacks - but this leaves a knowledge and preparedness gap for new and emerging threats. Very few enterprises, our customers among them, know the effectiveness of their security controls against prominent threats.
Picus validates your endpoint security controls against a wide range of threats, from basic attacks to Advanced Persistent Threats (APTs), with up-to-date attack techniques mapped to MITRE’s ATT&CK framework. As with Sodinokibi, Picus can simulate the lifecycle of all malware, from Initial Access through Impact, covering 834 different implementations of 179 ATT&CK techniques.
Not only endpoint security controls, Picus can also test your network and email security controls, continuously.
SODINOKIBI TIMELINE
Sodinokibi ransomware, also known as REvil or Sodin, has been responsible for a series of high-profile attacks since April 2019:
- Attackers used a zero-day exploiting CVE-2019-2725 vulnerability in the Oracle WebLogic Server to distribute it in April 2019 .
- Attackers breached the infrastructure of at least three managed service providers (MSPs) to deploy ransomware on the MSPs' customers systems.
- Sodinokibi spam campaign targeted Germany in June 2019.
- Attackers compromised the WinRAR Italian website and replaced the WinRAR installation file with an instance of the ransomware in June 2019 .
- 22 Texas local and state entities were hit by Sodinokibi in August 2019.
- Attackers compromised WordPress sites to distribute Sodinokibi in September 2019.
- The financially motivated GOLD SOUTHFIELD threat group used Sodinokibi in September 2019.
TECHNICAL ANALYSIS
Initial Access
Spearphishing Attachment (ATT&CK T1193) is one of the most used Initial Access techniques used by ransomware families as in Sodinokibi. Attackers use spam emails with an attached MS Office Word document including a malicious macro to download the ransomware to the target system. In order to show the lifecycle of Sodinokibi ransomware, we analyzed a Microsoft Word document.
The specific sample analyzed below is Bewerbungsunterlagen_6704760.doc ( SHA-256: fb8b03748b617acf0ee3b138c5b37e74ec396bc73da3362d633862d7283742fd , detection rate is only 33/60 as of today). Even though Sodinokibi uses simple obfuscation techniques mentioned below, 30 of 60 antiviruses cannot detect it. “Bewerbungsunterlagen” means “application document” in German, and the attackers used a CV theme to lure victims into downloading the document.
Sodinokibi is a “Ransomware-as-a-Service (RAAS) malware, so its distribution methods vary depending on the attacker distributing it. Attackers have used the following Initial Access techniques in their other campaigns to deliver Sodinokibi:
- Exploit Public-Facing Application (ATT&CK T1190 ) : Attackers exploit vulnerabilities in enterprise applications to distribute it, such as the deserialization vulnerability CVE-2019-2725 in Oracle WebLogic Server having a CVSS score of 9.8/10.
- Remote Desktop Protocol ( ATT&CK T1076 ) : Attackers use RDP to deliver Sodinokibi.This delivery technique can also be classified in External Remote Services ( ATT&CK T1133 ).
- Supply Chain Compromise ( ATT&CK T1195 ) : Sodinokibi ransomware was distributed through a compromised version of WinRAR downloaded from the WinRAR Italia website.
- Drive-by-Compromise ( ATT&CK T1189 ): Attackers compromised WordPress sites and injected JavaScript over the content of the original site to spread Sodinokibi.
When a victim opens the document, Microsoft Word asks to enable/disable macros. It reveals that a macro is embedded in the document (Scripting, ATT&CK T1054 ). It claims that it was created in an earlier version of Microsoft Office and asks the victim to enable the content, which launches the code hidden in the macros.
Defense Evasion
When we examined macros in the document, we saw that VBA (Visual Basic for Applications) codes were split into modules and functions for the purpose of obfuscation (Obfuscated Files or Information, ATT&CK T1027 ). The VBA codes download de1.trp from 54.39.233.132 and saves it to the C:\Windows\Temp\ directory as MicrosoftOfficeWord_upd.v.88735.34.5.exe.
The downloaded file is the Sodinokibi ransomware (SHA-256: 720fbe60f049848f02ba9b2b91926f80ba65b84f0d831a55f4e634c820bd0848, detection rate is 51/69 as of today). Its artifacts usually mimic the names of known executables for Defense Evasion, such as a Microsoft Word update file name (MicrosoftOfficeWord_upd.v.88735.34.5.exe) as in this sample (Masquerading, ATT&CK T1036 ).
Execution
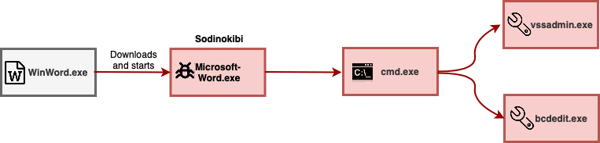
As seen in the above process graph, the macro in the Word document downloads and runs Sodinokibi executable. After execution, it runs vssadmin.exe to delete all volume shadow copies on the system to prevent recovery (Inhibit System Recovery, ATT&CK T1490 ), and uses bcdedit.exe twice to disable automatic Windows recovery features by modifying boot configuration data (Inhibit System Recovery, ATT&CK T1490 )
Impact
Like most ransomware, Sodinokibi encrypts files and adds a random extension such as “test.jpg.1cd8t9ahd5” (Data Encrypted for Impact, ATT&CK T1486 ). It also drops a ransom note in folders that contain encrypted files. The ransom note recommends accessing the attacker’s website over the TOR browser. When we accessed the website, we saw the following page that wants 0,6346 Bitcoin worth $5,000. If you pay the ransom in two days, the cost is halving.
.png?width=600&name=img2%20(1).png)
Sodinokibi ransomware uses multiple encryption by encrypting files and also private keys. To put it another way, it requires two keys for decryption. Sodinokibi utilizes AES encryption to encrypt the private keys, and Salsa20 for encrypting files. As far as I know, unfortunately there are no decryption tools to restore data encrypted by Sodinokibi ransomware.
CONCLUSION
In this wave of attacks, Sodinokibi ransomware spreads by spearphishing emails that lure victims into downloading a CV themed Word document, which contains a macro that downloads and executes the ransomware. Commands in the macro are split into different modules and functions for defense evasion. After infection, Sodinokibi encrypts files and puts a ransom note in folders that contain encrypted files. It also deletes all volume shadow copies and disables automatic Windows recovery features to inhibit system recovery. Sodinokibi uses very similar infection and execution techniques with the notorious GandCrab ransomware, raising suspicion that it was developed by GandCrab authors.
Our “continuous security validation and remediation” approach is currently used by hundreds of satisfied customers in countries all over the world. Our users can assess their cyber resilience with 8,500 real attack techniques enriched with context information such as affected products, countries, sectors and threat actors. They can also identify the weaknesses and strengths of their defensive controls by simulating these techniques which expose the threats that cannot be blocked by current security controls.
Picus also provides actionable prevention and detection signatures to remedy security controls against unblocked and undetected attacks. In this way, organizations can gain maximum benefit from their security investments, quantify their risks, and increase their resilience as a result. Because of our unique approach, Picus was recognized as a Cool Vendor in the Security and Risk Management, 2H19 report by Gartner.
Do you want to know if your current enterprise security controls are blocking these types of attacks? You can contact us at demo@picussecurity.com. Don’t hesitate. Let us show you how within just a few hours, we can quickly report to you how your network security systems are protecting you against Sodinokibi and other prominent cyber attacks!
 APPENDIX
APPENDIX
MITRE’s ATT&CK Techniques Observed
| Initial Access | Execution | Persistence | Defense Evasion | Lateral Movement | Impact |
|---|---|---|---|---|---|
| T1189 Drive-by-Compromise | T1059 Command-Line Interface | T1133 External Remote Services | T1036 Masquerading | T1076 Remote Desktop Protocol | T1486 Data Encrypted for Impact |
| T1190 Exploit Public-Facing Application | T1054 Scripting | T1054 Scripting | T1490 Inhibit System Recovery | ||
| T1133 External Remote Services | |||||
| T1193 Spearphishing Attachment | |||||
| T1195 Supply Chain Compromise |


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






