Making Security Validation Easier and More Accessible: Introducing our New Next-Generation Platform
LAST UPDATED ON MARCH 03, 2025
Picus Security is delighted to announce the availability of our next-generation security validation platform.
In this blog to mark the launch, H. Alper Memiş (Picus CEO and Co-Founder) details the benefits of the release for Picus customers. He also reveals why, by making threat-centric validation easy and accessible for all, it represents another major step toward realizing our company vision.
Product launches are always a key milestone. Here at Picus, the team and I couldn’t be prouder and more excited to share with you the details of our new cloud platform, which takes automated security validation to the next level.
A key factor influencing the success of any product is market need, and when it comes to the challenge of defending against evolving threats, organizations face more difficulties and complexity than ever.
Despite businesses spending more money on security, cyber incidents continue to rise and breaches are increasingly damaging.
Driving innovation
Since Picus Security was founded in 2013, our mission has been to enable security teams to be more proactive and threat-centric. As the pioneer of Breach and Attack Simulation, we deliver the insights organizations need to better understand their threat readiness and optimize security investments to prevent serious incidents.
A desire to help our customers enhance their cyber resilience even further is what continues to drive us. It’s why, following the Series B funding we raised last year, we’ve been investing heavily in our team and technology to not only enhance our existing capabilities in the area of Security Control Validation but also expand them in other areas.
The two additional Picus products available from today, Attack Path Validation and Detection Rule Validation, will ensure that security teams can obtain even broader insights to identify and mitigate cyber risks inside and outside corporate networks.
To reflect our increased capabilities, we’ve also updated the name of our solution to The Complete Security Validation Platform.
.png?width=574&height=406&name=Obtain%20a%20holistic%20view%20of%20your%20security%20posture%20(2).png)
Why automated security validation is needed
In a rapidly evolving security landscape, it’s imperative to swiftly identify and address weaknesses before attackers can exploit them. New attack methods and constant changes within IT environments mean organizations’ security posture varies daily. It’s the reason Gartner and other thought leaders now advocate a continuous approach to threat exposure management.
Continuous threat exposure management, however, cannot be achieved by performing single point-in-time assessments. Automation is now essential to obtain the level of insight needed to keep pace with the latest threats.
The need for automation to help security teams test their defenses continuously and at scale is now widely recognized by organizations such as the US Cybersecurity and Infrastructure Security Agency (CISA) and UK National Cyber Security Centre (NCSC).
By launching our next-generation platform, Picus enables even small and mid-sized organizations to perform automated validation easily and take swift mitigating action to address gaps. Our latest approach to automated security validation means that we are committed to helping organizations not only validate, prioritize and optimize.We now also help them to discover high-risk users and assets too.
The overall result of the changes we’re making is that organizations can achieve a more holistic view of their security posture and more confidently answer questions about their preparedness to defend against the latest threats.
More about our latest products
To deliver security control validation at scale, The Picus Complete Security Validation Platform consists of three individually licensable products:
Security Control Validation - simulates ransomware and thousands of other real-world cyber threats to help measure and optimize the effectiveness of security controls to prevent and detect attacks.
Attack Path Validation - assesses an organization’s security posture from an ‘assumed breached’ perspective by performing lateral movement and other evasive actions to identify high-risk attack paths to critical systems and users.
Detection Rule Validation - analyzes the health and performance of SIEM detection rules to ensure that security operations center (SOC) teams are reliably alerted to threats and can minimize false positives.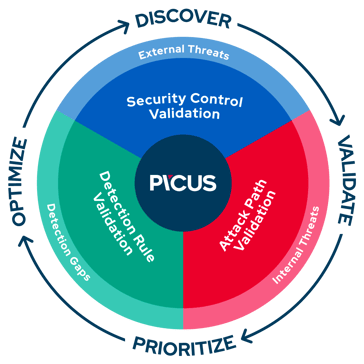
Unlike other solutions that have a steep learning curve and are time consuming to use, all our products are designed with ease of use in mind and integrate together to provide a clear workflow.
The strength of Picus’ technology partnerships means that the new platform supports the latest security controls and vendor-specific mitigation recommendations - areas that continue to make our solution stand out above the competition.
Find out more at Picus reLoaded 2022
If you’d like to learn more about the new Picus platform and our vision for automated security validation, I’d be delighted if you could join us at Picus reLoaded.
Register to attend this free virtual event, taking place on November 15th, to hear from members of the Picus team and thought leaders from Gartner, Frost & Sullivan, SANS and Mastercard.
We’d like your feedback
While we hope you like and see value in the changes we’ve made to our platform, feedback from customers and partners is always extremely welcome to help shape its ongoing development.
If you have any comments to share or would like to know more about how Picus can help you strengthen your organization’s cyber resilience, please feel free to reach out to a member of our team or submit an inquiry.
Thank you for supporting our mission as we continue to make security validation easy and accessible for all.
Stay safe
H. Alper Memiş









