Picus Security Adopts Top ATT&CK Techniques
LAST UPDATED ON MARCH 24, 2023
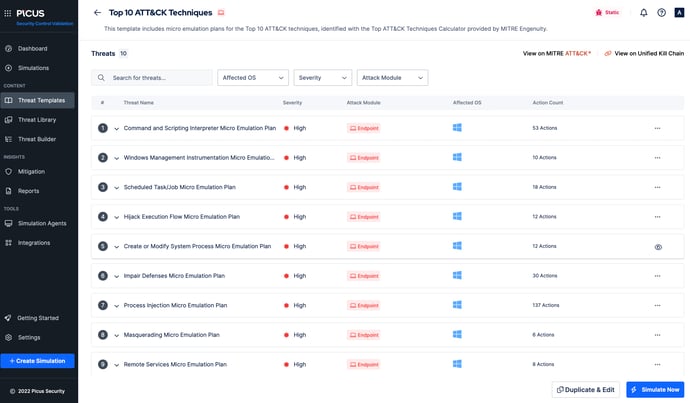
Since defending against all MITRE ATT&CK® techniques is impractical, security teams must prioritize those commonly leveraged by the threats organizations face. The Center for Threat Informed Defense's (Center) Top ATT&CK Techniques project aids defenders in systematically prioritizing techniques by identifying the ones most commonly observed by its Sightings Ecosystem.
Picus, a founding Center Gold affiliate, has adopted this R&D project to help enterprises quickly and easily validate their security controls against Top ATT&CK Techniques.
Download and Learn Adoption Best Practices
Read the Top ATT&CK Techniques Adoption Spotlight to learn about the enhancements we’ve made to our Complete Security Validation Platform to enable security teams to simulate the top ten ATT&CK techniques plus measure and optimize coverage against them.
About the Center for Threat-Informed Defense
The Center is a non-profit, privately funded research and development
the organization operated by MITRE Engenuity. The Center’s mission is to advance the state of the art and the state of the practice in threat informed defense globally. Comprised of participant organizations from around the globe with highly sophisticated security teams, the Center builds on MITRE ATT&CK®, an important foundation for threat informed defense used by security teams and vendors in their enterprise security operations. Because the Center operates for the public good, outputs of its research and development are available publicly and for the benefit of all. Visit https://ctid.mitre-engenuity.org/



.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






