Simulating and Preventing Atlassian Confluence CVE-2021-26084 Exploit
On August 25, 2021, Atlassian published information about a critical remote code execution vulnerability (CVE-2021-26084) affecting Atlassian Confluence Server and Confluence Data Center. A public exploit code was released on August 31, 2021.
Within a day after the release of the exploit, Picus Labs has updated the Picus Threat Library with attacks that exploit the Atlassian Confluence CVE-2021-26084 vulnerability. We also updated the Picus Mitigation Library with prevention signatures of network security controls. So, organizations using Picus Continuous Security Validation Platform have already tested the effectiveness of their security controls against CVE-2021-26084 vulnerability and mitigated the vulnerability with vendor-specific prevention signatures provided by Picus Platform.
What is the CVE-2021-26084 Vulnerability?
An OGNL injection flaw causes the vulnerability on Atlassian Confluence Server and Confluence Data Center software that’s usually installed on Confluence self-hosted project management, wiki, and team collaboration platforms. OGNL (Object-Graph Navigation Language) is a simple scripting language for interacting with Java code, which is the underlying technology for most Confluence software.
What is the Impact of CVE-2021-26084 Vulnerability?
CVE-2021-26084 allows unauthenticated attackers to execute arbitrary code on Confluence Server or Data Center installations. Accordingly, the CVSSv3 base score for CVE-2021-26084 is 9.8 Critical.
A non-administrator or unauthenticated user can remotely access the vulnerable endpoints on these applications if ‘Allow people to sign up to create their account’ is enabled. Go to ‘COG > User Management > User Signup Options’ on the affected software to see if this is enabled.
What is the Current Situation?
After the release of the public exploit, researchers reported that attackers are trying to exploit the vulnerability. Considering Confluence is a widely used team collaboration software, and the CVE-2021-26084 vulnerability is immensely potent, threat actors are expected to increase their attacks in the following weeks.
Update: US-Cert and CISA released an urgent notification stating mass exploitation of the vulnerability on September 3, 2021.
What Should You Do?
CVE-2021-26084 was patched on August 25. To protect against these attacks, we highly advise organizations to identify vulnerable Confluence installations and upgrade them to the latest Long Term Support release. Moreover, we suggest that enabling prevention signatures for CVE-2021-26084 in their security controls. You can find relevant prevention signatures below.
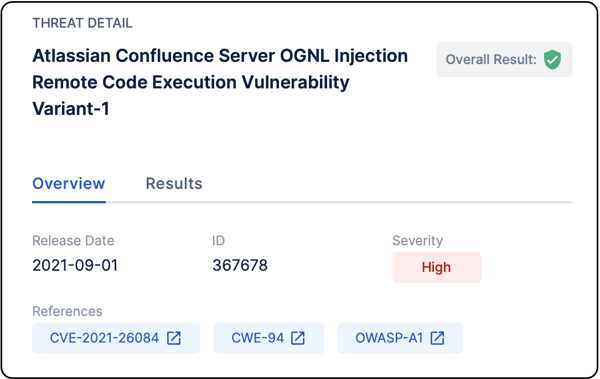
How Picus Helps Simulate Atlassian Confluence Server CVE-2021-26084 RCE Attacks?
We also strongly suggest simulating CVE-2021-26084 vulnerability to test the effectiveness of your security controls against Confluence Server RCE attacks using the Picus Continuous Security Control Validation Platform. Picus Threat Library includes the following threats for CVE-2021-26084 vulnerability:
|
Picus ID |
Threat Name |
|
367678 |
Atlassian Confluence Server OGNL Injection Remote Code Execution Vulnerability Variant-1 |
|
530383 |
Atlassian Confluence Server OGNL Injection Remote Code Execution Vulnerability Variant-2 |
Picus Threat Library also includes the following threats for previous Atlassian Confluence vulnerabilities:
|
Picus ID |
Threat Name |
CVE |
|
553673 |
Atlassian Confluence Remote Code Execution via Macro Preview Feature Variant-1 |
CVE-2019-3396 |
|
726719 |
Atlassian Confluence Remote Code Execution via Macro Preview Feature Variant-2 |
CVE-2019-3396 |
|
541281 |
Atlassian Confluence Remote Code Execution via LFI Vulnerability |
CVE-2019-3398 |
|
421887 |
Atlassian Confluence Cross-Site Scripting Vulnerability |
CVE-2018-5230 |
Moreover, Picus Threat Library contains 1500+ vulnerability exploitation and endpoint attacks in addition to 10.500+ other threats as of today.
How Picus Helps Prevent Atlassian Confluence CVE-2021-26084 RCE Attacks?
Picus also provides actionable mitigation content. Picus Mitigation Library includes prevention signatures to address CVE-2021-26084 and other vulnerability exploitation attacks in preventive security controls.
|
Security Control |
Signature ID |
Signature Name |
| F5 BIG-IP | 200003437 | Java code injection - java/lang/Runtime (Parameter) |
| ForcepointNGFW | - | HTTP_CRL-Confluence-OGNL-Injection-CVE-2021-26084 |
| SourceFire IPS | 1.58094.1 | SERVER-WEBAPP Atlassian Confluence OGNL injection remote code execution attempt |
| FortiWeb | 90500037 | Known Exploits |
| ModSecurity | 944100 | Remote Command Execution: Suspicious Java class detected |
| ModSecurity | 944130 | Suspicious Java class detected |
| ModSecurity | 944250 | Remote Command Execution: Suspicious Java method detected |
| Snort | 1.58094.1 | SERVER-WEBAPP Atlassian Confluence OGNL injection remote code execution attempt |
We will update the above list when Picus Labs validate the signatures of other vendors/products.
Conclusion
Simulating emerging threats, identifying gaps in your preventive and detective security controls, fixing these gaps, and validating applied mitigations are crucial for improving your cyber resilience and security effectiveness. Picus is the first Breach and Attack Simulation (BAS) and Continuous Security Validation (CSV) that adds Confluence CVE-2021-2608 attacks and actionable mitigation insights.









