SLAM Method for a Comprehensive Phishing Prevention Guide
LAST UPDATED ON FEBRUARY 03, 2026
What Does the SLAM Method Stand For?
SLAM is an acronym used to quickly evaluate whether an email may be a phishing attempt. It guides users to examine four key elements that commonly reveal suspicious activity. It stands for:
- Sender
- Links
- Attachments
- Message

Figure 1. The SLAM Method for Phishing Awareness Explained
Sender Verification: How to Do It and Why It’s Crucial
The sender check focuses on validating the authenticity of the email’s origin. Attackers often manipulate or spoof the visible display name to appear legitimate, so the technical verification happens in the underlying sender details.
Here is what to look for in the “Sender” stage.
A. Full email address, not just the display name
Threat actors often spoof the display name while hiding a malicious sender address underneath.
B. Lookalike and homoglyph domains (including Cyrillic, Greek, and extended Latin characters).
Attackers use visually indistinguishable characters to create deceptive domains. Watch for:
- Cyrillic letters replacing Latin (о, а, с, е, р)
- Greek homoglyphs (ν vs v, η vs n)
- Mixed-script domains
- Zero-width spaces or invisible Unicode characters
|
Example: "Microsoft Support" <helpdesk@microsоft.com> |
Cyrillic characters can be hard to notice, but attackers do not rely on them alone.
Sometimes they exploit how the human eye interprets shapes, using letter combinations that visually mimic real characters:
|
Example: "Microsoft Support" helpdesk@rnicrosoft.com |
The attacker replaces the letter m with the two-character sequence r + n, which visually mimics m in many fonts. This makes rnicrosoft appear almost identical to microsoft at a quick glance.
C. Domain age and reputation
New or low-reputation domains are common indicators of phishing. You can verify a domain’s age and ownership using WHOIS lookup tools.
These reveal registration dates, ownership details, and whether the domain is anonymized.
A simple free option is Whois.com, and ICANN Look Up.
What to look for?
- Domains created within the last 30–90 days
- Recently registered domains impersonating well-known brands
- Domains with no historical DNS records
- Reputation scores marked as suspicious, unknown, or low-trust
- Mismatched sender domain vs. claimed organization
D. Metadata and header inconsistencies
Check alignment across:
|
Mismatched or “weird” paths often indicate spoofing.
Links: How to Reveal the Real URL Behind a Click
When you hover over a hyperlink in an email or message, you reveal the underlying URL destination (often in the status bar or a small preview). This step is vital because the visible link text can differ from the real address where you’ll be taken.
How it works:
In HTML, a link is defined with an anchor tag, for example:
|
<a href="https://malicious.example.com/login">Click here to verify</a> |
The visible text (“Click here to verify”) can look harmless, but the href attribute controls the actual destination.
When you hover over the link (or long-press on mobile), the browser or email client displays this underlying URL before any connection is made.
Attackers exploit this design by making the anchor text look legitimate while directing the href to a deceptive domain. Common techniques include adding extra characters, creating misleading sub-domains, or using look-alike brand names to trick users into clicking.
Attachments: How to Identify Dangerous Files Before You Open Them
Attachments are one of the most common entry points for malware, including ransomware loaders, infostealers, remote access trojans, and weaponized documents that exploit vulnerabilities in Office, PDF readers, or archive utilities.
Attackers manipulate context and psychology to push the victim into opening a malicious file.
Legitimacy: “This looks like something I’d normally receive.”
Threat actors frequently disguise malware as routine business documents:
- invoices, purchase orders, delivery receipts
- resumes or HR forms
- meeting notes, shareable documents, supposed policy updates
- vendor contracts or RFP files
These mimic real workflows. Even experienced users can be tricked when attackers mirror internal templates, signatures, and file-naming styles.
Here is a convincing phishing example that abuses legitimacy to deliver malware.
|
Subject: Updated Q4 Budget Review - Please Confirm by EOD
Please review the attached Budget_Review_Q4_Final.xlsx and confirm that your department's numbers look correct. We need to close this loop today so procurement can proceed with the updated approvals. Thanks, |
Urgency: “You must open this now.”
Urgency is a classic social-engineering tactic because it disrupts critical thinking.
Examples:
- “Payment overdue – action required”
- “Your account will be closed today. Proof document attached.”
- “Immediate compliance review – open the form”
Pressure reduces scrutiny and increases the likelihood that a user will run macros or open a harmful file.
Incentive: “Here’s a reward or benefit.”
Free benefits appeal to curiosity or personal gain:
- gift cards, bonuses, free access forms
- contest results
- unexpected refunds or salary adjustments
This tactic often targets broad audiences and relies on impulse. Here is an example of incentive-based phishing mail.
Subject: Your Exclusive Amazon Reward Is Ready to Claim
|
Hello, Mr. (accurate naming for spear-phishing)
This offer expires in 24 hours.
|
File-Type Abuse: Using trusted formats to deliver exploits
Attackers commonly weaponize:
- Office documents with malicious macros
- PDFs containing embedded scripts or links
- ZIP/RAR archives hiding executable files
- ISO, IMG, and LNK files used to bypass traditional detections
- HTML attachments redirecting users to credential-harvesting sites
Modern ransomware groups, like LockBit, BlackCat, and TA577, use exactly these file types to infect systems at scale.
Messages: How to Spot Suspicious or Inconsistent Content?
The Messages step focuses on the content of the email. Even when the sender or attachment looks legitimate, the wording often reveals the attack. Look for:
- Unusual tone or phrasing that doesn’t match how the sender normally writes.
- Spelling or grammar errors, odd formatting, or inconsistent branding.
- Generic greetings (“Dear Customer”), incorrect names, or mismatched personalization.
- Requests that feel out of context, such as actions the sender wouldn’t normally ask you to do.
- Inconsistencies between message and role, like HR sending financial documents or IT sending payment reminders.
- Manipulative tone, pressure, fear, urgency, or unexpected benefits.
If anything in the message feels “off,” stop, verify through another channel, and do not interact with links or attachments.
Using the SLAM Method to Help Prevent Phishing Attacks
The SLAM method is a simple, practical framework that helps users assess email safety with confidence. By applying SLAM whenever something feels off, individuals can quickly spot the warning signs of phishing and avoid risky actions. It’s easy to remember, easy to teach, and focuses on the four elements attackers rely on most, sender, links, attachments, and message.
Because it’s so straightforward, SLAM works well in any security awareness program. It encourages users to pause, think, and examine emails with intention, empowering them to make safer choices when confronted with suspicious messages.
Recognizing a Phishing Email
While the SLAM method offers a focused approach, phishing emails often carry additional warning signals beyond that checklist. These include:
- Poor grammar and spelling: Many phishing emails contain awkward wording or typos. Professional organisations typically proofread their messages.
Here is an example.
|
Dear Customer, Your account have been suspended due to unusual activites. Please verify your informations urgently by open the attached form and update your details. Failure to do so will result in permanent closed of your account. |
This kind of awkward phrasing, inconsistent verb use, and misspelled words is a strong indicator of a phishing attempt.
- Urgent or threatening tone: Scammers often try to pressure you into acting fast, claiming your account will be locked or that a payment is overdue.
- Strange-looking URLs: Even if the link text appears legitimate, hovering over it may reveal a misspelt or unrelated domain. Attackers exploit this to mislead you.
By combining the SLAM framework with awareness of these red flags, individuals and teams increase their chances of spotting phishing attempts before damage occurs.
What to Do When You Detect a Phishing Attack
Here are five clear steps to follow when you detect a phishing attack.
- Stop all interaction: Don’t click links, open attachments, or reply to the suspicious email.
- Verify the sender: Contact the person or organisation through a separate, trusted channel (phone call, official website) to confirm if the email is legitimate.
- Report the incident: Use your organisation’s process (or email provider’s reporting tool) to flag the phishing attempt so filters and defenders can respond.
- Change affected credentials: If you clicked a link, opened an attachment, or entered information, update your passwords and enable multi-factor authentication on relevant accounts.
- Scan and monitor: Run a full antivirus/malware scan on your device, check for abnormal activity (logins, transactions), and continue monitoring for signs of compromise.
Employee Awareness Training: Integrating SLAM into Organizational Cybersecurity
To strengthen an organization’s defense against phishing, SLAM should be embedded directly into employee awareness training. The method is simple, memorable, and easy to apply, making it ideal for everyday use.
Training sessions should introduce SLAM as a practical checklist, encouraging employees to
- pause,
- assess the sender,
- links,
- attachments, and
- message, and
make informed decisions before interacting with an email.
By pairing SLAM with real examples and periodic phishing simulations, employees learn to recognize threats in realistic scenarios.
Consistent reinforcement, clear reporting procedures, and regular refreshers ensure the habit sticks, transforming SLAM into a natural part of daily workflow and a reliable layer of human-centric security.
How Picus Can Help Prevent Breaches from Phishing Attacks?
Picus Email Infiltration Module enables organizations to safely simulate URL- and attachment-based phishing attacks to evaluate the performance of their email security gateways and firewall controls. By replicating real-world phishing techniques, it helps teams identify gaps, validate policy effectiveness, and strengthen one of the most frequently targeted layers of the security stack.
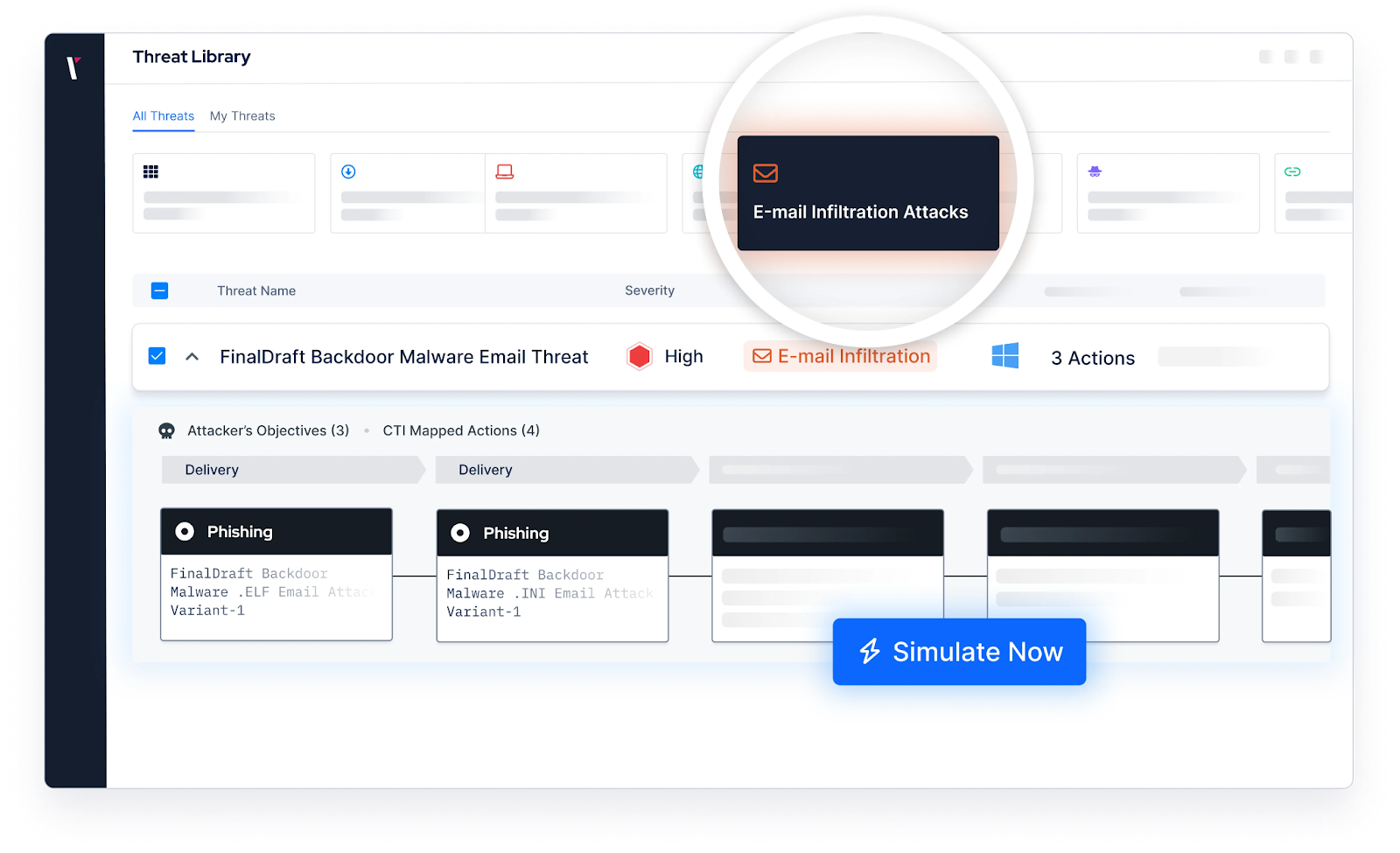
With 2,546+ real-world email threats and 10,167+ unique attacker actions from the Picus Threat Library, the module delivers extensive threat coverage. Simulations include realistic sender profiles, verified email addresses, malicious URLs, and weaponized attachments, providing a true-to-life assessment of how well email defenses detect, block, and respond to threats.
Automated, continuous testing ensures issues such as policy drift, outdated signatures, spam filter misconfigurations, and delivery delays are discovered early, before they can be exploited by attackers.
See how your email defenses perform against real-world phishing techniques, book a demo today!


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






