Vulnerability assessment is the process of identifying, classifying, and reporting known security weaknesses across systems, applications, and infrastructure. It’s fundamental. Always has been. It's how security teams get visibility into what’s vulnerable, where risk might be, and how that risk is distributed across infrastructure. It’s the starting point for everything from compliance to patching, and no security program runs without it.
But while assessment gives you data, it doesn’t give you certainty. It flags potential risk, not actual exposure. And in modern environments, where the number of CVEs has exploded, controls are stacked in layers, and attack surfaces shift daily, that distinction matters more than ever.
Assessment is still necessary, but it’s no longer enough.
This blog breaks down the real purpose of vulnerability assessment, how it differs from full vulnerability management, and why, in today’s environments, forward-leaning teams are evolving beyond scanning alone, toward validated, risk-informed decisions.
The Role of Vulnerability Assessment
The job of vulnerability assessment is straightforward: vulnerability scanners scan systems, identify known weaknesses, assign scores, and report the findings. It’s a detection process, not a decision-making one.
Vulnerability assessment typically involves the following.
- Discovery of assets
- Scanning those assets against known vulnerability databases (like CVE/NVD)
- Applying severity scores (CVSS, EPSS)
- Exporting that data for remediation workflows
It’s a point-in-time view of where known flaws exist.
|
While vulnerability assessment is a critical first step, it’s just one part of a larger vulnerability management strategy, a distinction that’s often overlooked or conflated.
|
What Powers Vulnerability Assessment?
Vulnerability assessment is powered by scanning engines, threat intelligence, and integrations that work together to detect known weaknesses across your environment. Key components include:
-
CVE/NVD Databases: Feed scanners with known vulnerabilities.
-
Scanning Engines: Detects misconfigurations, unpatched software, and service flaws.
-
Credentialed Access & APIs: Enable deeper scans via system logins or cloud API access.
-
Asset Discovery Tools: Identify devices and services across networks and cloud.
-
Risk Scoring Models: Help prioritize findings using severity and exploitability scores.
These technologies give security teams visibility into known vulnerabilities, though not whether those issues are exploitable in your environment. For that, you need validation.
How Organizations Use Vulnerability Assessment
Vulnerability assessment plays a key role in day-to-day security operations. It’s how teams maintain visibility into known weaknesses across their environments, whether on-premises, in the cloud, or across hybrid networks.
Common use cases include:
-
Routine Risk Monitoring: Regular scans help teams keep track of outdated software, missing patches, and misconfigurations.
-
Compliance and Audit Support: Many regulations (e.g., PCI DSS, HIPAA, ISO 27001) require vulnerability assessments as part of technical controls and evidence gathering.
-
Patch Management and Remediation: Assessment findings feed directly into IT workflows, triggering patch deployment, system updates, or compensating controls.
-
Security Operations (SOC) Triage: Findings may inform escalation rules or be cross-referenced against threat intelligence or SIEM alerts.
-
Risk Reporting and Dashboards: Security leaders use assessment outputs to populate risk dashboards and demonstrate posture to stakeholders.
In short, vulnerability assessment helps teams understand where they may be exposed. But knowing where vulnerabilities exist is only the starting point, it takes validation to understand which ones actually matter.
Where It Begins, But Shouldn’t End
While vulnerability assessment supports critical functions across compliance, patching, and triage, it’s only one piece of the puzzle. To make security actions more strategic, organizations need to evolve from detection to decision-making, and that’s where vulnerability management enters the picture.
Vulnerability Assessment vs. Vulnerability Management
To make everything clearer, let’s look at the key differences between vulnerability assessments and management.
Vulnerability Assessment tells you: This system has a known vulnerability.
Vulnerability Management asks: So what should we do about it?
Vulnerability management is a broader lifecycle. It includes:
- Regular scanning (assessment)
- Prioritization (often score-based)
- Remediation or mitigation
- Validation of fixes
- Continuous reporting and improvement
|
Assessment is the input. Management is the process. And both are critical.
|
But even a full-fledged vulnerability management program is no longer enough. Most organizations get stuck at the first phase: scanners generate long lists of high and critical findings, and security teams are left overwhelmed, treating everything as equally urgent, regardless of actual risk.
This is where things start to break down.
To truly manage exposure, not just react to scanner output, organizations need validation. That’s why we emphasize Exposure Management, powered by continuous validation, as the next essential evolution. We’ll explore this further later in the blog.
But first, we need to be clear: vulnerability assessment was never designed to solve every aspect of security risk on its own. Let’s take a closer look at what it is, and what it isn’t.
Why Vulnerability Assessment Is Struggling in Modern Environments
Let’s be clear: vulnerability assessment isn’t failing because the tools are bad.
|
It's struggling because the model they were built on, scan, score, patch, was never designed for today's scale or complexity.
|
Here’s what’s changed:
-
Volume: Over 40,000 CVEs in a year. No team can investigate them all.
-
Context: CVSS doesn’t know your network, your segmentation, or your compensating controls.
-
Visibility gaps: Assessment doesn’t tell you what’s reachable, what’s already blocked, or what’s actually exploitable.
-
Tool overload: Most teams already have firewalls, WAFs, EDRs, XDR, SIEMs, but assessments don’t tell you if those tools are working against specific vulnerabilities.
So while vulnerability assessments generate useful data, they don’t generate answers. They’re snapshots, not simulations. You end up reacting to scores instead of understanding risk.
That’s not a vulnerability problem. That’s a prioritization problem. And that’s exactly where exposure validation comes in.
Don’t Throw Away Vulnerability Assessment, Make It Actionable Through Validation
You don’t need to replace your scanners. You need to make their findings matter.
Exposure Validation doesn’t compete with vulnerability assessment, it completes it. Your scanners tell you where vulnerabilities exist: CVEs, severity scores, affected assets. But they leave critical questions unanswered:
- Is this asset actually reachable by an attacker?
- Is there a viable attack path that leads to it?
- Do our controls stop the exploit at the source, such as firewalls, WAFs, or IPS? If not, do they at least detect, log, or alert on it through systems like IDS or EDR?
- Is this truly urgent, or a theoretical risk we can deprioritize?
Exposure Validation adds the missing layer: real-world evidence.
It tests whether those vulnerabilities can be exploited in your environment, safely and continuously. Not in theory, not on paper, but based on how your actual defenses perform against real attack behavior.
Validation doesn't just reduce noise. It empowers you to focus your limited time and resources where they’re most needed, by identifying which exposures are truly exploitable and which are not.
|
Assessment tells you where the fires might be. Validation tells you where the smoke is real, and where the alarms are just crying wolf.
|
Exposure Validation vs. Vulnerability Assessment
To better understand the improvements that exposure validation brings in, let’s look at a comparison table: assessment vs. validation.
|
Vulnerability Assessment
|
Exposure Validation
|
|
Identifies known weaknesses based on public CVEs and signature matching
|
Simulates real-world attack behavior mapped to CVEs and adversary TTPs
|
|
Uses static scoring (e.g. CVSS) to estimate risk
|
Measures validated exploitability in your specific environment
|
|
No visibility into network exposure, segmentation, or reachability
|
Actively checks if the vulnerable asset is reachable and exploitable
|
|
Ignores the presence and effectiveness of compensating controls
|
Validates whether your controls (EDR, WAF, NGFW, SIEM) detect or stop the threat
|
|
Generates long, undifferentiated vulnerability lists
|
Produces a filtered, evidence-backed set of exploitable exposures
|
|
Treats patching as the only form of mitigation
|
Enables mitigation through control tuning, network isolation, and alternative defenses
|
|
Static, point-in-time snapshots (weekly or monthly)
|
Continuous validation that adapts to control changes and infrastructure shifts
|
Why Assessment Alone Isn’t Enough: A Real-World Example Using Log4Shell
Let’s say your vulnerability scanner flags Log4Shell (CVE-2021-44228) across three different assets in your environment:
-
Asset A: A public-facing web application
-
Asset B: A service behind a WAF and proxy
-
Asset C: An internal HR system with no external access
From a vulnerability assessment perspective, all three assets receive a CVSS score of 10.0, and the EPSS score suggests a high likelihood of exploitation. On paper, they appear equally urgent. As a result, teams may enter remediation mode, triggering SLAs, patching processes, and alerts across the board.
But assessment tells you what’s there, not whether it can be exploited in your environment.
Enter Exposure Validation
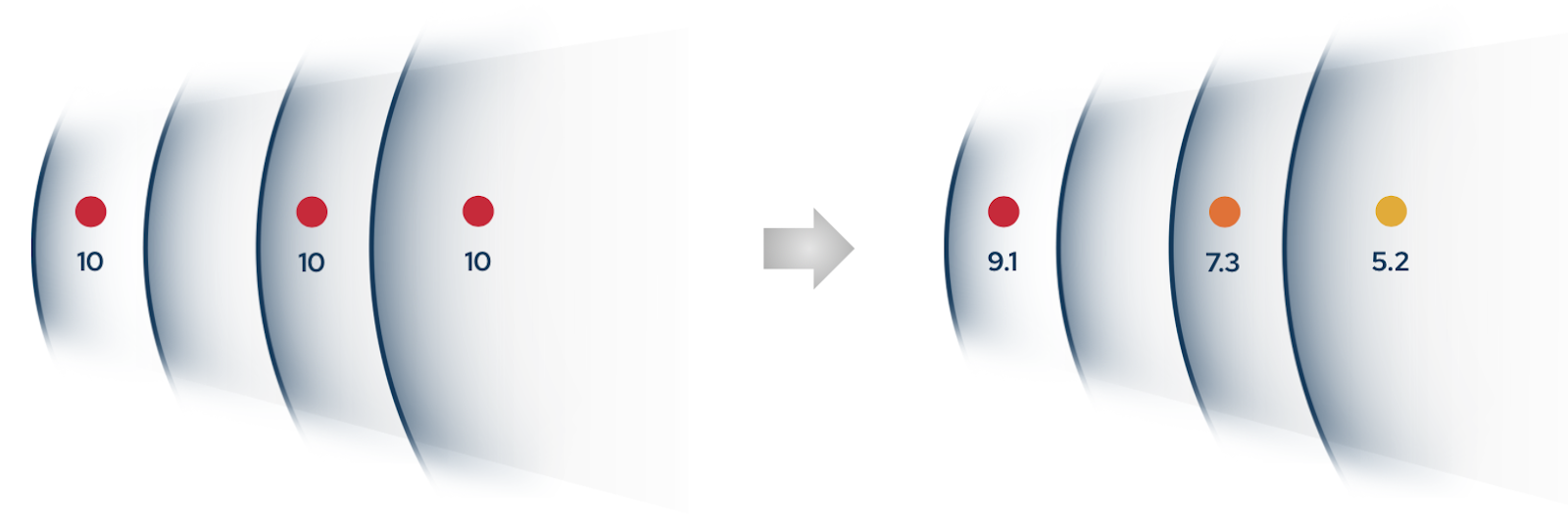
Figure. Picus Exposure Validation in Action
But this is where Exposure Validation changes the outcome.
By simulating real attack behavior and factoring in reachability, segmentation, and security control effectiveness, the findings become more precise:
-
Asset A is reachable, exposed, and unprotected. The exploit succeeds. → Exposure Score: 9.1
-
Asset B is protected by a WAF. Simulated threats are blocked. → Exposure Score: 7.3
-
Asset C is isolated and cannot be reached by an attacker. → Exposure Score: 5.2
From Detection to Decision
This is the critical distinction between assessment and validation:
With Exposure Validation, you gain the confidence to deprioritize two-thirds of your findings, not based on assumptions, but on evidence. Resources stay focused, patching efforts become targeted, and your risk posture reflects actual exploitability, not just severity scores.
This is how organizations evolve from reactive assessment to proactive exposure management.
Exposure Validation Doesn’t Replace Assessment, It Makes It Operational
Vulnerability assessment is essential. It tells you what vulnerabilities exist. But on its own, it stops short of answering the real question: Do these vulnerabilities matter in our environment?
Exposure Validation adds that missing layer of evidence:
- It shows which findings are exploitable, and which are just noise
- It confirms where controls are working, and where they’re silently failing
- It helps teams prioritize with confidence, not assumptions
With Exposure Validation in place, security teams see:
-
Up to 80% reduction in high-priority findings
-
5x faster remediation of validated exposures
-
Tangible evidence of control effectiveness for auditors, boards, and compliance
This isn’t about replacing what you have. It’s about upgrading how you use it.
You already assess vulnerabilities. Now validate them.
The Future Is Validation-First
Security teams rely on vulnerability assessments to identify what’s potentially at risk. But increasingly, leaders are asking deeper, more contextual questions:
- Is this vulnerability actually exploitable in our environment?
- Are our controls detecting or stopping it?
- How exposed are we, truly?
These aren’t questions traditional assessment alone can answer.
That’s why many are beginning to look beyond raw scan data toward validation-based decision making. It’s not about replacing assessment, but about enhancing its value with real-world evidence.
Upgrade Your Vulnerability Program with Picus Exposure Validation
Traditional vulnerability tools flood you with findings. Picus helps you focus on what’s real.
The Picus Exposure Validation Platform transforms raw scan results into evidence-based decisions. Building on proven techniques like Breach and Attack Simulation (BAS) and Automated Penetration Testing, Picus integrates with your existing stack, firewalls, WAFs, EDRs, and more, to simulate real adversary behaviors, validate the effectiveness of your prevention and detection controls, and assign exposure scores grounded in your environment, not just theoretical models.
No more reacting to scores alone. No more wasting cycles on unexploitable risks.
With Picus, you can:
- Simulate real-world attacks to test actual exploitability in your environment
- Validate the performance of your prevention and detection tools, firewalls, EDRs, WAFs, SIEMs
- Assign exposure scores that reflect true risk, not just CVSS or EPSS assumptions
- Automatically deprioritize vulnerabilities already blocked by your controls
- Gain precise, actionable mitigation guidance to improve control effectiveness
It’s the evolution from vulnerability scanning to exposure-led risk reduction, a smarter, evidence-driven approach that reduces noise, accelerates remediation, and builds trust across teams, boards, and regulators.
Validate what matters. Ignore what doesn’t.
Book a demo and see how Picus helps you move beyond assessments, to true validation.


-3.png?width=353&height=200&name=image%20(79)-3.png)





.png?width=353&height=200&name=what-is-exposure-assessment-blog-preview%20(1).png)
