What’s New in MITRE ATT&CK v18: Detection Strategies and Analytics Unveiled
LAST UPDATED ON NOVEMBER 13, 2025
The cybersecurity community is buzzing about the MITRE ATT&CK Framework v18.0, released on October 28, 2025.
This version introduces one of the most transformative updates in the framework's history: the retirement of traditional Detections and Data Sources, which are now replaced by Detection Strategies and Analytics for every technique and sub-technique.
Figure 1. MITRE ATT&CK v18.0 Changes
The Shift to Behavior-Driven Cyber Threat Intelligence
This evolution elevates the MITRE ATT&CK Framework from a static catalog of simple detection rules to a dynamic, behavior-driven model. This structure more precisely reflects how real-world adversaries operate, significantly enhancing your cyber defense strategies.
The result is improved visibility across all tactics and stronger cross-tactic correlations, critical for Security Operations Centers (SOCs) dealing with overlapping telemetry, especially between Execution and Persistence tactics.
Key Takeaways
The new structure provides immediate, measurable benefits for detection engineering and threat hunting:
-
Detection Strategy: This new concept replaces old detections, offering a structured, behavior-focused methodology for understanding specific adversary activity.
-
Actionable Analytics: The introduction of Analytics is key for security teams. It directly links high-level detection strategies to real-world telemetry, helping defenders precisely pinpoint the where and how of adversarial behaviors. This effectively bridges the gap between threat intelligence and operational defense.
-
Refined Data Model: The updated data components enhance the mapping of telemetry to adversary techniques, ensuring more precise and scalable detection development.
-
New Adversary Coverage: Version 18 expands the framework's breadth by introducing 12 new techniques, ensuring the model stays current with modern attack vectors.
What’s New in the MITRE ATT&CK v18 Framework?
Introduction of Detection Strategies and Analytics
MITRE has replaced traditional “Detections” and “Data Sources” with a new two-tier detection model:
-
Detection Strategies (DETxxxx): High-level defensive approaches that describe how to identify adversary behaviors.
Example additions include strategies such as “Detection of Wireless Sniffing” (DET0743) and “Detection of Trust Relationship Modifications in Domain or Tenant Policies” (DET0458)
-
Analytics (ANxxxx): Specific behavioral or telemetry-based analytic implementations that make detections actionable.
Figure 2. MITRE ATT&CK Defenses > Detections > Detection Strategies
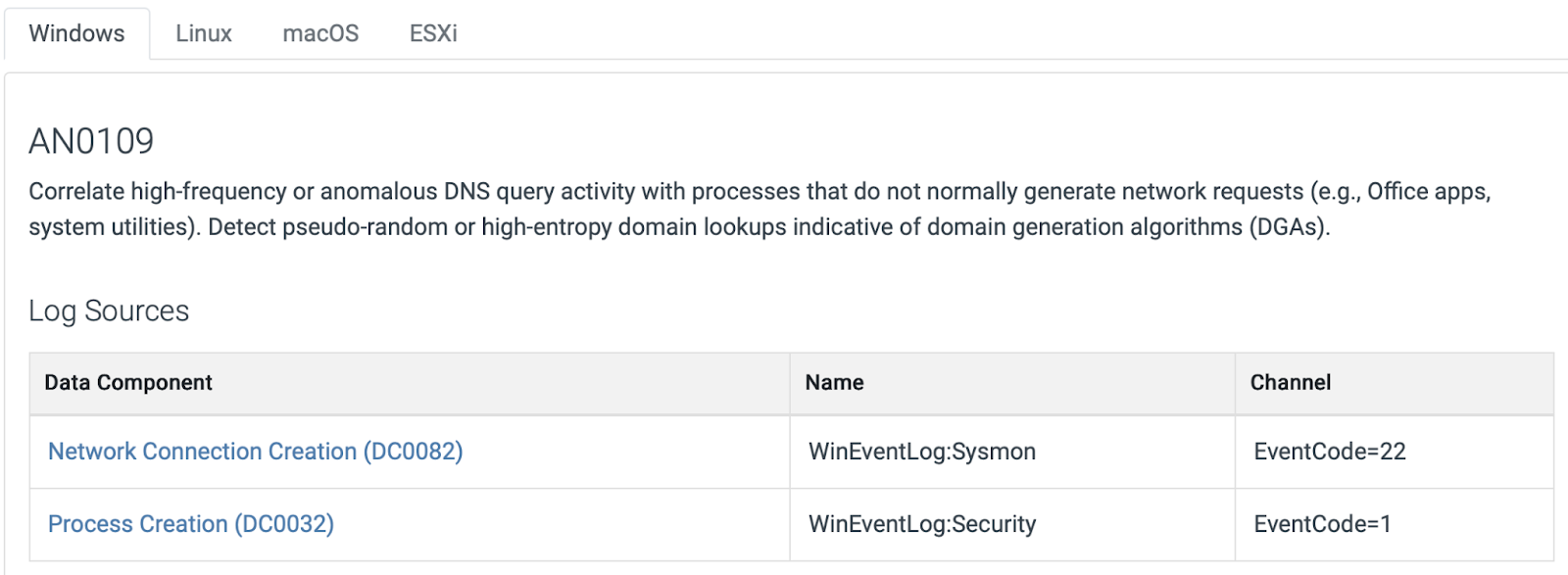
Figure 3. MITRE ATT&CK v18.0 Analytics Example
Retirement of Data Sources and Static Detections
All legacy data sources (e.g., Command Execution, Application Log, Active Directory Object Modification) were fully deprecated.
These static entries are now replaced or linked to new detection strategies and analytics to improve telemetry precision and contextual visibility.
Behavior-Driven Detection Model
Each analytic now includes detailed references to log sources, data components, and telemetry channels, for example:
- vpxd.log from vCenter Management
- esxi:shell under Shell Execution
This structure supports more granular, behavior-based detection engineering rather than generic event matching.
Enhanced Cross-Tactic Correlation
Detection Strategies now connect behaviors across tactics, notably between Execution and Persistence, enabling defenders to trace attack chains and validate detection coverage at a behavioral level.
New Techniques Added in MITRE ATT&CK v18
MITRE ATT&CK v18 introduces 12 new techniques across Enterprise, Mobile, and ICS domains, reflecting the latest adversary tradecraft and detection research.
Key additions include:
-
Enterprise: New techniques for cloud exploitation, virtualization abuse (ESXi/Shell execution), and trust relationship manipulation enhance coverage of hybrid and identity-based attacks.
-
Mobile: Added behaviors around Wi-Fi discovery and wireless sniffing expand detection visibility in mobile and IoT environments.
-
ICS: New wireless sniffing and remote exploitation analytics improve defensive mapping for industrial systems.
These updates ensure ATT&CK aligns with modern attack surfaces, linking behaviors, telemetry, and analytics to help defenders detect and validate attacks more effectively.
Why MITRE ATT&CK v18 Changes Matter
MITRE ATT&CK v18 transforms the framework into a behaviorally grounded defense model.
By shifting to Detection Strategies and Analytics, defenders gain clarity on:
- How adversaries move laterally through systems and networks
- What telemetry sources reveal those movements
- How SOC detection engineering aligns with adversary tradecraft
These changes redefine detection from static documentation to operational defense, helping teams understand not just what to detect, but how detection can be achieved.
In essence, MITRE is bridging the gap between intelligence and action, turning knowledge of adversary behavior into measurable defensive capability.
Example: New MITRE ATT&CK v18 Detection Model
The table below describes the new detection model for each technique and sub-technique across all ATT&CK tactics.
|
MITRE Detection Layer |
ATT&CK Framework v18 Example |
|
Technique/Sub-technique |
T1082 – System Information Discovery (Tactic: Discovery) |
|
Detection Strategy |
DET0525 – System Discovery via Native and Remote Utilities |
|
Analytic |
AN0850 – Behavioral detection of system and network discovery commands (e.g., correlating systeminfo, esxcli system version get, Get-ComputerInfo, or remote API calls) |
|
Data Components |
DC0009 – Process Creation (Event Log) |
This example shows how MITRE ATT&CK v18 redefines detection for T1082 – System Information Discovery.
- Instead of listing static data sources, v18 maps the technique through a Detection Strategy (DET0525) and Analytic (AN0850) linked to specific Data Components (DC0009, DC0017, DC0025).
- Each layer builds on the other, from adversary behavior to detection logic to telemetry, creating a clear, testable path from technique → strategy → analytic → data.
What’s Next for the MITRE ATT&CK® Framework
MITRE is preparing several forward-looking changes to the ATT&CK framework.
Among the most notable: the current “Defense Evasion” tactic is proposed to be split into two new tactics: Stealth and Impair Defenses. This re-organisation is still under development, but it highlights MITRE’s intent to map adversary goals and behaviours more precisely.
In addition, MITRE plans to re-classify several techniques to better align with their intent and context, including:
- T1548 – Abuse Control Mechanism: moving from Defense Evasion to Privilege Escalation
- T1578.005 – Modify Cloud Compute Configurations: moving from Defense Evasion to Persistence
Looking Ahead into 2026 and Beyond: The Roadmap Includes
- Aligning every detection with the new Detection Strategies and Analytics model.
- Expanding CTI content (new software, groups, campaigns).
- Extending coverage to additional asset types, sectors and system architectures.
- Refining and re-categorising techniques and adding new sub-techniques.
- Establishing an ATT&CK Advisory Council to provide structured community feedback on the framework’s evolution.
Operationalizing MITRE ATT&CK® v18 with Picus Security
As MITRE advances the ATT&CK framework, Picus Security ensures continuous alignment with every new release. The Picus Platform features over 6,500 threats and 27,000 attack action tests to validate your security controls.
Each test is precisely mapped to corresponding MITRE ATT&CK techniques, sub-techniques, mitigations, and detections, delivering comprehensive, framework-based validation.
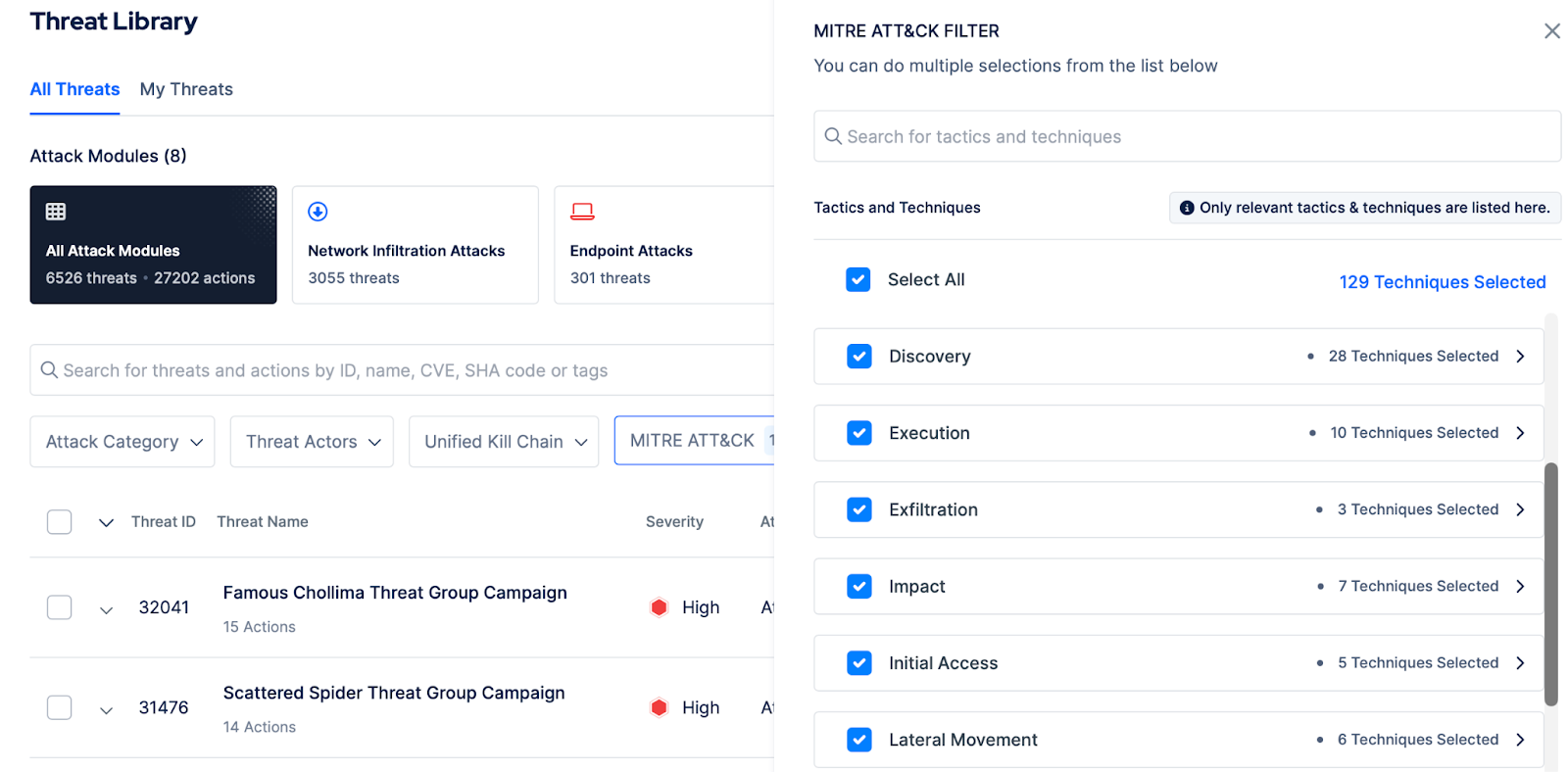
Figure 4. Picus Security Control Validation Threat Library
We support both vendor-neutral and vendor-specific detection and mitigation content, ensuring that teams with heterogeneous tool-sets get value no matter their stack.
- On the vendor-neutral side: Our Mitigation Library offers generic SIGMA rules and best-practice detection logic for major SIEM/EDR systems.
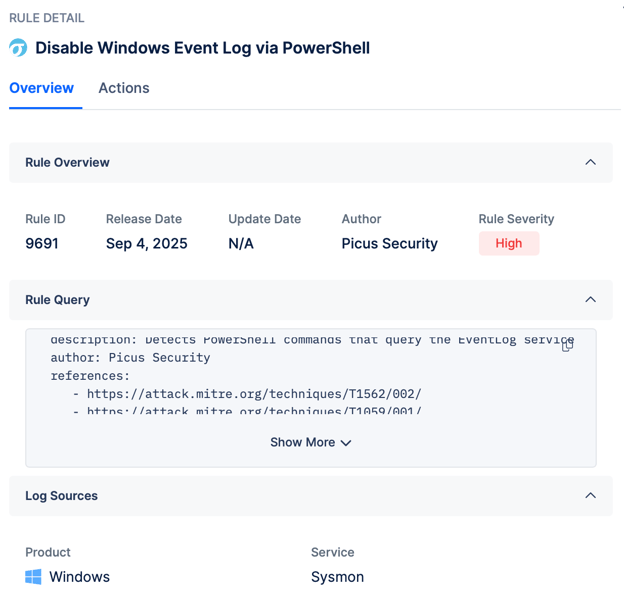
Figure 5. Sigma rule example showing how Picus Security Control Validation (SCV) detects the disabling of Windows Event Logs through PowerShell
- On the vendor-based side: We also deliver custom detection rules and prevention signatures tailored to specific security products and technologies.
For Picus customers, this means:
- A unified view of ATT&CK technique coverage tied to both generic and product-specific detection engineering.
- Automated mapping of detection content to MITRE models, enabled via AI-driven rule mapping and threat simulation.
- Platform-driven simulation of adversary behavior, generation of tailored rule sets, and ready-to-apply mitigation insights across varied enterprise tech stacks.
If you’d like to see how this works in practice, sign up for a demo to explore how Picus turns MITRE ATT&CK v18 from framework into operational defence validation.

.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)







