What Is Security Control Validation?
In the ever-evolving threat landscape, organizations are facing more and more advanced cyberattacks each day. To keep up with these threats, organizations need to ensure that their security controls are effective and up-to-date against both known and emerging threats that target their region and/or industry. This is where Security Control Validation comes in.
In this blog, we'll dive into the details of Security Control Validation, its importance for organizations, and how it differs from traditional security testing methods.
What Is Security Control Validation?
Security Control Validation is a continuous security assessment approach that evaluates the effectiveness of an organization's prevention and detection layer solutions against external threats. Thus, it helps organizations identify and address gaps in their security posture before an adversary can exploit them.
Security Control Validation ensures that an organization’s security measures and controls are functioning as intended, provide adequate protection against cyber risks, and conform to established security requirements.
Figure 1. Picus Security Control Validation.
Why Is Security Control Validation Important for Organizations?
Security Control Validation bolsters an organization's cybersecurity posture and ensures compliance with industry regulations. This proactive approach helps identify vulnerabilities, optimize resource allocation, and fosters a culture of continuous improvement.
In this section, we will delve into three critical aspects of Security Control Validation.
-
Improved Security Posture
-
Informed Decision for Security Investments
-
Compliance and Regulations
-
Continuous Improvement
Improved Security Posture
Security Control Validation is essential for organizations because it plays a pivotal role in improving their overall security posture.
By regularly evaluating the effectiveness of their security controls, organizations can assess how well their prevention and detection layer solutions respond under simulated threats within a controlled environment, before an actual adversary performs a cyberattack. This approach allows organizations to have a data-driven perspective on their security posture against specific threats that target their regions and/or industries. Continuous validation ensures that this evaluation process is ongoing, enabling organizations to adapt to new threats in real-time and maintain a strong security posture.
Figure 2. Testing Your Detection and Prevention Layer Solutions with Picus Security Control Validation.
Thus, Security Control Validation ensures organizations that their systems and digital assets are protected against constantly evolving threats. This proactive approach helps organizations to identify vulnerabilities and weaknesses before they can be exploited by cybercriminals, reducing the risk of data breaches and other security incidents.
Informed Decisions for Security Investments
Security Control Validation enables organizations to make informed decisions about resource allocation and security investments. By identifying underperforming security controls, organizations can allocate resources more effectively and focus on implementing solutions that provide a better return on investment.
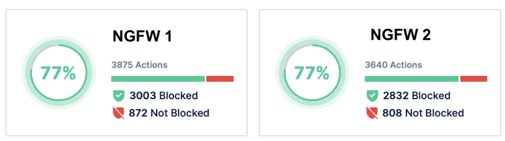
Figure 3. Better Return on Investment for Security Solutions.
Maintaining Compliance with Standards and Regulations
Security Control Validation is essential for organizations as it strengthens their cybersecurity posture and assists in maintaining compliance with industry standards and regulations, such as HIPAA, GDPR, and PCI DSS. By regularly validating security controls, organizations can demonstrate their commitment to best practices and avoid potential penalties.
For example, healthcare organizations can use Security Control Validation to ensure their security controls effectively safeguard protected health information (PHI) as required by HIPAA.
Continuous Improvement
Another critical aspect of Security Control Validation is its role in fostering a culture of continuous improvement within an organization. Regular validation of security controls encourages a proactive mindset among security teams, motivating them to stay up-to-date with the latest threats and security technologies. This ongoing process of evaluation and improvement helps to build a robust and resilient cybersecurity infrastructure that can better adapt to the dynamic threat landscape.
Security Control Validation vs. Traditional Security Assessment Approaches
Security Control Validation is a modern approach to security assessment that focuses on validating the effectiveness of an organization's security controls. It differs from traditional security testing methods in several ways, as described below.
Security Control Validation vs. Red Teaming
Red teaming is a manual process where a group of security experts, acting as adversaries, attempt to breach an organization's defenses. In contrast, Security Control Validation uses automated and continuous simulations of real-world attack scenarios to validate the performance of security controls.
While red teaming offers valuable insights into an organization's security posture, its results often remain relevant only briefly due to the dynamic nature of the security environment and the constantly evolving threat landscape. According to the Security Leader's Peer Report by Panaseer, many organizations reportedly operate an average of 57 separate security tools, with some even managing more than 76 [1]. Therefore, it becomes exceedingly difficult for a Red Team professional to thoroughly test every single security control within an organization's environment. Given that Red Teaming is typically time-consuming and resource-intensive, organizations should consider utilizing complementary solutions alongside it.
This is where Security Control Validation comes into the picture. With its always up-to-date threat library, Security Control Validation offers a scalable and efficient complementary solution that can be performed continuously without straining resources.
Security Control Validation vs. Penetration Testing
Penetration testing involves security professionals attempting to exploit vulnerabilities in an organization's systems to gain unauthorized access. While both Security Control Validation and penetration testing aim to identify vulnerabilities, Security Control Validation focuses on validating security control effectiveness, while penetration testing primarily identifies vulnerabilities.
Moreover, Security Control Validation offers continuous and automated assessments, whereas penetration testing is often a point-in-time exercise. This allows Security Control Validation to provide a more comprehensive and up-to-date understanding of an organization's security posture.
Security Control Validation vs. Vulnerability Scanning
Vulnerability scanning is an automated process that identifies potential vulnerabilities in an organization's systems and applications. It is often used as a first step in assessing an organization's security posture. However, vulnerability scanning does not validate the effectiveness of security controls or simulate real-world attack scenarios.
Security Control Validation goes beyond vulnerability scanning by simulating a wide range of threats to test the performance of security controls across various prevention and detection layers. This allows organizations to not only identify vulnerabilities but also understand how their security controls would perform in the face of real-world attacks.
In the below, we provide a comprehensive comparison table for Security Control Validation and other traditional security assessment approaches.
Figure 4. Comparison Table for Security Control Validation and Traditional Security Assessment Solutions.
Main Objectives of Conducting Security Control Validation Exercises
There are four main objectives of Security Control Validation exercises.
-
Ensuring Effectiveness in Prevention and Detection Controls,
-
Adopting a Proactive Approach to Prevent Attacks
-
Optimize Resources,
-
Aligning With Industry Frameworks
1. Ensuring Effectiveness and Gaining Confidence in Prevention and Detection Controls
The exercises are designed to instill confidence in your organization's prevention and detection controls by evaluating their effectiveness in defending against cyber threats and safeguarding critical assets. This helps maintain a strong security posture and minimize the risk of serious breaches.
Figure 5. Testing the Effectiveness of Prevention and Detection Controls in Your Organization with Picus SCV.
2. Adopting a Proactive to Prevent Attacks
In the face of rapidly evolving cyber threats, adopting a proactive, threat-centric approach with Security Control Validation is crucial for organizations. By utilizing Breach and Attack Simulation (BAS) solutions, organizations can continuously evaluate their security measures against the latest emerging threats and their associated tactics, techniques, and procedures (TTPs).
This process allows organizations to identify and remediate gaps in their security controls, ensuring a robust defense against potential cyberattacks and minimizing the risk of breaches.
3. Optimizing Resources
Security Control Validation exercises not only help in optimizing prevention and detection capabilities through easy-to-implement signatures and rules but also improve the efficiency and effectiveness of Security Operations Centers (SOC). Automation of manual assessment and engineering processes reduces fatigue and fosters better collaboration among security teams.
4. Aligning With Industry Frameworks and Staying Prepared
By mapping assessment results to established frameworks such as MITRE ATT&CK, organizations can visualize their threat coverage and prioritize the mitigation of identified gaps. Additionally, validation exercises ensure preparedness against the latest threats by testing defenses against an up-to-date threat library containing current and emerging attack techniques.
What Tools and Technologies Are Commonly Used in Security Control Validation Exercises?
Security Control Validation exercises predominantly rely on Breach and Attack Simulation (BAS) platforms to effectively assess and validate the performance of an organization's security controls. These cutting-edge platforms provide a comprehensive, automated solution for simulating a wide range of cyber attack scenarios in real-time.
BAS tools are designed to test the effectiveness of an organization's security controls across multiple prevention and detection layers. By adopting a threat-centric approach, these platforms enable continuous and on-demand assessments, providing an up-to-date security score for the organization. Additionally, BAS platforms can integrate with other security solutions, such as SIEM and SOAR systems, to enhance overall security intelligence and response capabilities.
Utilizing advanced techniques and methodologies, BAS platforms simulate Tactics, Techniques, and Procedures (TTPs) used by real-world adversaries. These simulations help identify areas of vulnerability within an organization's security infrastructure, enabling them to prioritize remediation efforts and allocate resources effectively. With the actionable insights generated by BAS tools, organizations can continually improve their security posture and strengthen their defenses against the ever-evolving threat landscape.
As the foremost use case of Breach and Attack Simulation (BAS), the primary goal of Security Control Validation is to ensure that the implemented security controls function as intended, comply with industry standards and best practices, and effectively address potential risks and vulnerabilities.
As a Breach and Attack Simulation (BAS) use case, Security Control Validation focuses on assessing security controls, including but not limited to
-
Next-Generation Firewalls (NGFW),
-
Web Application Firewalls (WAF),
-
Intrusion Detection Systems (IDS),
-
Intrusion Prevention Systems (IPS),
-
Anti-virus and Anti-malware Software,
-
Endpoint Detection and Response (EDR),
-
Extended Endpoint Detection (XDR)
-
Security Information and Event Management (SIEM) solutions, and
-
Email Gateways.
Below, you will find some example use cases that include, but are not limited to, the following security control solutions.
Example Use Case 1: Validating IPSs and NGFWs
In the case of Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), Security Control Validation evaluates their capability to detect, analyze, and prevent malicious network traffic and potential intrusion attempts. This assessment process involves multiple technical aspects, such as
-
signature-based detection,
-
anomaly-based detection, and
-
inline vs. passive mode,
to ensure the organization's IDS/IPS solutions are effectively safeguarding the network infrastructure.
Signature-based Detection
Security Control Validation tests the IDS/IPS solutions' ability to identify attack patterns by simulating various types of attacks based on established signatures.
This includes well-known exploits, as well as sophisticated malware designed for specific purposes such as ransomware for encryption and extortion, rootkits for defense evasion and persistence, wipers for data destruction, and trojans for information stealing. Additionally, the test covers command and control (C2) communication and common attack methods.
The objective is to ensure that the system can accurately detect and respond to threats that are constantly updated and added to an up-to-date library through extensive Cyber Threat Intelligence (CTI) research by red team professionals.
Anomaly-based Detection
Security Control Validation assesses the IDS/IPS capability to detect unknown or zero-day threats by identifying deviations from normal network behavior. This may involve creating custom traffic patterns or simulating abnormal network activities to test the system's ability to recognize and alert on potentially malicious activities that do not match any predefined signature.
Inline vs. Passive Mode
Security Control Validation assesses the effectiveness of the IPS solution in inline mode, where it actively blocks malicious traffic, and in passive mode, where it only detects and generates alerts for potential threats. This assessment helps determine the optimal mode for the organization's risk tolerance and operational requirements.
Example Use Case 2: Validating SIEM Solutions with Security Control Validation
In the case of SIEM solutions, Security Control Validation verifies their capabilities to collect, correlate, and analyze security events from multiple sources to identify potential threats and trigger alerts in real-time. This process involves several technical aspects to ensure that the organization's SIEM solution is effectively detecting and managing security events.
-
Log Collection and Normalization
-
Correlation Rules and Use Cases
-
Threat Intelligence Integration
-
Incident Prioritization and Response
Below, you will find brief descriptions for each aspect.
Log Collection and Normalization
Security Control Validation tests the SIEM's ability to collect logs from various devices and systems, such as firewalls, IDS/IPS, network devices, endpoints, and applications. The test involves ensuring that the SIEM can parse and normalize logs from different formats and sources, enabling efficient data correlation and analysis.
Correlation Rules and Use Cases
Security Control Validation evaluates the SIEM's pre-defined and custom correlation rules, which detect patterns indicative of security incidents. Security Control Validation assesses the accuracy and relevance of these rules by simulating real-world scenarios and examining the SIEM's ability to detect and alert on such events.
Threat Intelligence Integration:
Security Control Validation verifies the SIEM's integration with threat intelligence feeds, which provide up-to-date information on known threats, vulnerabilities, and malicious indicators of compromise (IOCs). By simulating attacks using IOCs from recent campaigns or emerging threats, Security Control Validation can determine if the SIEM effectively utilizes threat intelligence data to enhance its detection capabilities.
Incident Prioritization and Response
Security Control Validation tests the SIEM's ability to prioritize security incidents based on factors such as severity, impact, and likelihood. This involves simulating multiple concurrent events and analyzing the SIEM's incident response capabilities, including automated remediation actions and alert notifications to appropriate personnel.
Example Use Case 3: Validating Email Gateway Solutions with Security Control Validation
For email gateways, Security Control Validation assesses their ability to filter spam, detect phishing attempts, and block malicious attachments effectively. This evaluation involves several critical aspects of email gateway performance:
-
Spam Filtering
-
Phishing Detection
-
Malicious Attachment Blocking
-
URL Filtering
-
Data Loss Prevention (DLP) Integration
A brief overview of each aspect is provided below.
Spam Filtering
Security Control Validation tests the email gateway's spam filtering algorithms to ensure that unsolicited and unwanted messages are accurately identified and filtered out. This may involve sending a variety of test emails with spam-like characteristics and monitoring the gateway's ability to prevent them from reaching the user's inbox.
Phishing Detection
Security Control Validation evaluates the email gateway's ability to identify and quarantine phishing emails, which are designed to deceive recipients into revealing sensitive information or performing actions that may compromise their security. This assessment may involve simulating phishing campaigns with varying levels of sophistication and verifying the gateway's effectiveness in detecting and blocking such attempts.
Malicious Attachment Blocking
Security Control Validation examines the email gateway's ability to block emails containing malicious attachments, such as those carrying malware or exploiting known vulnerabilities. This may involve sending test emails with different types of malicious payloads and monitoring the gateway's performance in preventing these attachments from reaching the user's inbox.
URL Filtering
Security Control Validation assesses the email gateway's ability to identify and block malicious URLs embedded within emails, which may lead to compromised websites or drive-by downloads. This evaluation includes testing the gateway's URL filtering capabilities against a range of malicious and benign URLs to measure its accuracy and effectiveness.
Data Loss Prevention (DLP) Integration
Security Control Validation verifies the email gateway's integration with Data Loss Prevention (DLP) solutions to prevent sensitive information from being accidentally or intentionally transmitted via email. This assessment may involve simulating various scenarios where sensitive data is sent via email and evaluating the gateway's ability to detect and block such transmissions.
In summary, by examining the performance and configurations of these security controls, Security Control Validation can identify weaknesses and areas that require improvement, helping organizations strengthen their cybersecurity posture and better protect their digital assets from evolving threats.
What Are the Key Components of an Effective Security Control Validation Program?
An effective Security Control Validation program consists of several key components that work together to ensure a comprehensive and robust assessment of an organization's security posture. These key components include:
- Threat Intelligence,
- Comprehensive Testing Methodology,
- Continuous and On-Demand Assessment,
- Automation and Scalability,
- In-Depth Analysis and Reporting,
- Integration with Security Frameworks,
- Customization and Flexibility
Threat Intelligence
A strong Security Control Validation program relies on up-to-date and accurate cyber threat intelligence (CTI) to simulate real-world attack scenarios and techniques.
Figure 6. Picus Security Control Validation Threat Library.
This information enables the program to test the organization's defenses against the latest threats and vulnerabilities, providing a relevant and realistic assessment of the security controls.
Comprehensive Testing Methodology
An effective Security Control Validation program uses a comprehensive testing methodology that covers various attack vectors, security controls, and stages of the cyber kill chain. This ensures a holistic evaluation of the organization's security posture and the effectiveness of its prevention, detection, and response capabilities.
Continuous and On-Demand Assessments
A robust Security Control Validation program incorporates both continuous and on-demand assessments, allowing organizations to maintain an up-to-date security score and stay informed about their security posture. This enables timely identification and remediation of vulnerabilities or weaknesses in the security controls.
Automation and Scalability
An effective Security Control Validation program leverages automation and scalability to efficiently assess a large number of security controls across multiple environments, reducing the time and resources required for manual testing. This also ensures consistency and repeatability in the testing process.
In-Depth Analysis and Reporting
A successful Security Control Validation program provides in-depth analysis and reporting that includes not only the identification of vulnerabilities and weaknesses but also actionable recommendations for improvement. This allows organizations to prioritize their remediation efforts and make informed decisions about their security investments.
Integration with Security Frameworks
An effective Security Control Validation program seamlessly integrates with established security frameworks, such as the MITRE ATT&CK Framework or NIST Cybersecurity Framework.
Figure 7. MITRE ATT&CK Integration in Picus Complete Security Control Validation Platform.
This alignment enables organizations to map their security controls to industry best practices and standards, ensuring a comprehensive and consistent approach to security control validation.
Customization and Flexibility
A robust Security Control Validation program offers customization and flexibility to adapt to an organization's specific needs, risk tolerance, and unique security architecture. This ensures that the program can effectively evaluate the organization's security controls and provide relevant insights for improvement.
How Do Organizations Identify and Prioritize Critical Security Controls for Validation?
To identify and prioritize critical security controls for validation, organizations need to employ a methodical approach that involves conducting Security Control Validation simulations and analyzing the results. This approach is critical for organizations to ensure that their security controls remain effective against evolving cyber threats.
The Security Control Validation simulations provide a comprehensive view of the effectiveness of different security solutions, such as WAFs, IPS/IDS, and mail gateway solutions, in preventing and detecting various cyber threats. The scores generated by the simulations offer valuable insights that enable organizations to make informed decisions regarding the remediation of their security controls.
For instance, if an emerging threat or zero-day vulnerability is identified, and the current security solutions fail to detect or alert the simulated attack, this would indicate an immediate need for critical remediation. Such remediation efforts may include updating signatures, YARA rules, or implementing additional security measures to protect the organization's infrastructure against cyber threats.
Furthermore, organizations can prioritize their security controls based on the criticality of their assets, threat vectors, and compliance requirements. For example, organizations in the healthcare industry may prioritize their security controls differently from those in the financial services sector due to varying compliance requirements and threat landscapes.
To ensure the effectiveness of their security controls, organizations should regularly conduct Security Control Validation simulations and update their security solutions to address emerging threats and vulnerabilities. This approach enables organizations to maintain a robust security posture and protect their assets from cyber threats.
Conclusion
Security Control Validation is an essential part of an organization's cybersecurity strategy. By conducting regular Security Control Validation exercises, organizations can ensure that their security controls are effective in combating rapidly changing cyber threats. The Security Control Validation process is intended to test and validate the effectiveness of security controls, identify potential weaknesses or vulnerabilities, and provide actionable recommendations for improvement. If organizations want to achieve a high level of cybersecurity resilience, they must integrate Security Control Validation into their security practices.
Frequently Asked Questions (FAQs)
What Types of Security Events and Incidents Can Security Control Validation Help Identify?
How Is Threat Intelligence Used in Security Control Validation Exercises?
How Can Security Control Validation Help Organizations Meet Compliance and Regulatory Requirements?
[1]T. Finnane, “Panaseer 2022 Security Leaders Peer Report,” Panaseer, Nov. 30, 2021. [Online]. Available: https://panaseer.com/reports-papers/report/2022-security-leaders-peer-report/. [Accessed: May 23, 2023]








