The LAPSUS$ Group - A Chaotic Start of Ransomware-free Extortion
A novel cyber threat group called LAPSUS$ (DEV-0537) launched cyberattacks against various organizations such as the Ministry of Health of Brazil, NVIDIA, Samsung, Octa, and Microsoft. Like ransomware gangs, LAPSUS$ exfiltrates confidential data from breached organizations and then threatens to leak or disclose data if the demanded ransom was not paid. However, the LAPSUS$ extortion group has eliminated the file encryption and machine lockout techniques used by traditional ransomware groups. In this blog, we explained the LAPSUS$ threat group in detail.
Picus Labs added attack simulations for LAPSUS$ operations to the Picus Threat Library, and you can test your security controls against LAPSUS$ attacks.
The LAPSUS$ Extortion Group
LAPSUS$ is a cyber extortion group that targets large government and commercial organizations. The LAPSUS group was first seen in December 2021, and their attacks were aimed at organizations in the United Kingdom and South American countries. However, their operations have grown larger and become worldwide. In a short amount of time, the LAPSUS$ threat group has claimed to exfiltrate data from various organizations and demanded money for not disclosing sensitive information to the public.
The main targets are large technology companies that operate in the telecommunications, hardware, software, and game industries. For initial access, the LAPSUS$ group tries to recruit insiders from their potential targets.
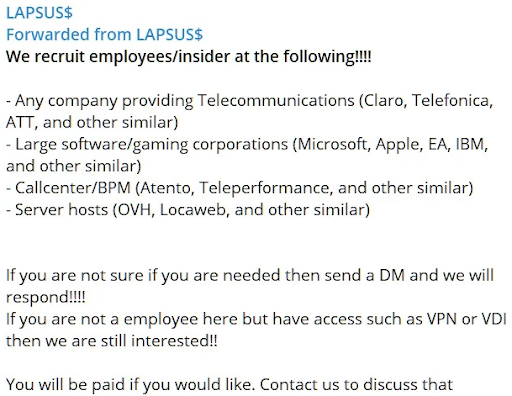
Figure 1: LAPSUS$ group’s recruitment message [1]
Here are some of the claimed victims of the LAPSUS$ cyber threat group.
-
COVID database of the Brazilian Ministry of Health was compromised, and confidential data was stolen.
-
Telecommunications companies Claro, Embratel, and NET were breached, and sensitive data such as customer information, infrastructure data, source code, and wiretap orders were stolen.
-
Rental car company Localiza was a victim of a defacement attack.
-
NVIDIA confirmed that employee credentials and proprietary data such as schematics, drivers, and firmware were stolen and leaked. Also, digital code-sign tools were stolen, and some malware was signed by it.
-
200 GB of proprietary source code from Vodafone was stolen.
-
Samsung was breached, and the source code for authentication mechanisms, bootloaders, and DRM modules was stolen and leaked.
-
Identity and Access Management company Okta was attacked, and the LAPSUS$ group reset the passwords and multi-factor authentication of Okta customers.
-
Ubisoft suffered temporary disruption to some of its games and services.
-
Credential hashes of user and service accounts of LG Electronics were stolen.
-
Source code of Bing, Bing Maps, Cortana was stolen from Microsoft’s internal Azure DevOps servers.
Why Is LAPSUS$ Not a Ransomware Group?
Although they extort money from their victims, the LAPSUS$ group should not be considered a ransomware group for several reasons. Let’s explain a typical ransomware group and how it does not fit the LAPSUS$ group.
1. A typical ransomware group creates a ransomware strain that follows similar adversary TTPs. There is no crypto or locker ransomware that we can associate with the LAPSUS$ group.
2. Ransomware threat actors focus on adversely impacting the availability of the victim’s assets. However, the LAPSUS$ mainly damages the confidentiality of the victim’s assets.
3. The LAPSUS$ extortion gang does not follow the ransomware attack lifecycle.
4. Ransomware groups aim to entirely stop the victim’s operations to force them into paying the demanded ransom. However, LAPSUS$ victims can maintain their daily operations.
5. Exfiltrated confidential data is the primary extortion methodology of the LAPSUS$ group. They do not use the T1486 Data Encrypted for Impact technique as other ransomware groups.
6. In some cases, the LAPSUS$ group conducted destructive cyberattacks and irreversibly damaged the victim’s data. This is an unlikely attack technique for ransomware groups.
Therefore, we call the LAPSUS$ an extortion group.
Test your security controls against LAPSUS$ attacks in minutes NOW!
How Picus Helps Simulate LAPSUS$ Attacks?
Using the Picus Continuous Security Validation Platform, you can test your security controls against the LAPSUS$ attacks. We advise you to simulate LAPSUS$ attacks and determine whether your security controls can prevent them or not. Picus Threat Library includes the following threats to simulate attacks and malicious tools used by the LAPSUS$ group.
|
Threat ID |
Action Name |
Attack Module |
|
45493 |
Lapsus Threat Group Campaign Malware Download Threat |
Network Infiltration |
|
35139 |
Lapsus Threat Group Campaign Malware Email Threat |
Email Infiltration (Phishing) |
MITRE ATT&CK Techniques used by LAPSUS$ Group
Initial Access
T1078 Valid Accounts
T1133 External Remote Services
T1190 Exploit Public-Facing Application
T1199 Trusted Relationship
Persistence
T1547.006 Kernel Modules and Extensions
T1078 Valid Accounts
T1133 External Remote Services
Privilege Escalation
T1547.006 Kernel Modules and Extensions
T1078 Valid Accounts
Defense Evasion
T1027.002 Software Packing
T1497 Virtualization/Sandbox Evasion
T1553.002 Code Signing
T1078 Valid Accounts
Credential Access
T1056.004 Credential API Hooking
T1552 Unsecured Credentials
T1111 Two-Factor Authentication Interception
Discovery
T1497 Virtualization/Sandbox Evasion
T1120 Peripheral Device Discovery
T1082 System Information Discovery
T1012 Query Registry
Collection
T1056.004 Credential API Hooking
Command and Control
T1571 Non-Standart Port
Exfiltration
T1537 Transfer Data to Cloud Account
Impact
T1485 Data Destruction
T1491 Defacement
T1490 Inhibit System Recovery
Indicators of Compromise (IOCs)
|
MD5 |
SHA-1 |
SHA-256 |
|
61089a51d3be666631053d516ad9b827 |
91b88d281ef983296157f8ebfc73958036148194 |
065077fa74c211adf9563f00e57b5daf9594e72cea15b1c470d41b756c3b87e1 |
|
07b7da86d2f548d18462f8d6d869052a |
f9153289b209929130f897ee47710b4c94aa6453 |
2f578cb0d97498b3482876c2f356035e3365e2c492e10513ff4e4159eebc44b8 |
Reference
[1] Microsoft Threat Intelligence Center (MSTIC), Detection and Response Team (DART), and Microsoft 365 Defender Threat Intelligence Team, “DEV-0537 criminal actor targeting organizations for data exfiltration and destruction,” Microsoft Security Blog, Mar. 22, 2022. [Online]. Available: https://www.microsoft.com/security/blog/2022/03/22/dev-0537-criminal-actor-targeting-organizations-for-data-exfiltration-and-destruction/. [Accessed: Mar. 23, 2022]








