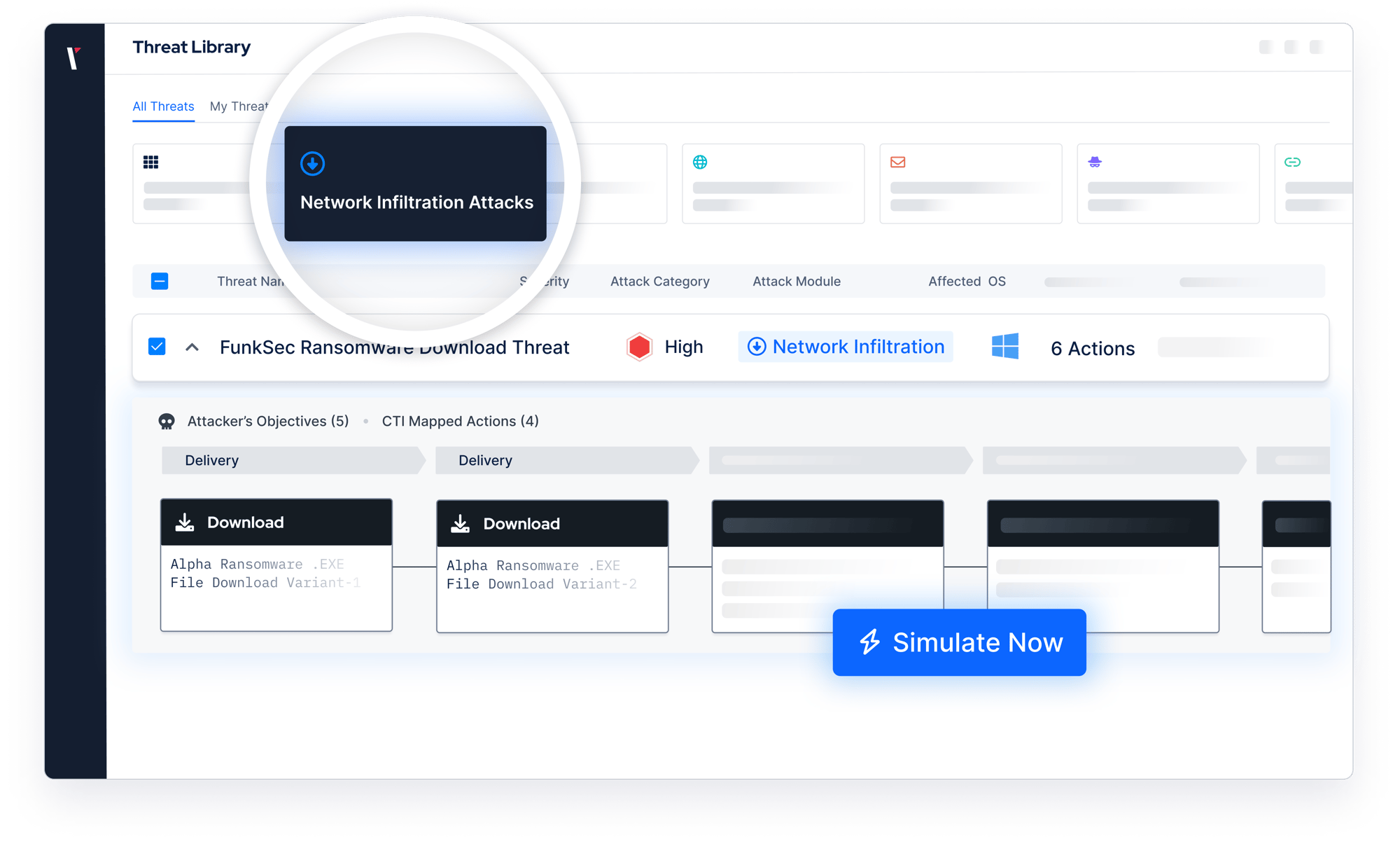
Network Infiltration Module
Picus Network Infiltration Module simulates real-world attacks to test your security controls. Identify gaps, validate firewall and IPS effectiveness, and strengthen your network security.
Why Validate Your Network Security?
Traditional security measures can degrade over time due to misconfigurations, policy exceptions, and evolving threats. Without continuous validation, organizations may unknowingly expose their networks to risks. Network security testing ensures your firewalls, IPS, and endpoint security solutions remain effective against real-world attacks.
-
User devices are a primary target – Phishing attacks and malware infections can compromise your network.
-
Security configurations weaken over time – Temporary rules and forgotten exclusions lead to vulnerabilities.
-
Manual security validation is resource-intensive – Most organizations lack the manpower to test security controls continuously.
-
Automation is the solution – Picus Network Infiltration Module continuously validates security controls, ensuring they perform as expected.
Strengthen Your Security
with Automated Network Testing
Picus Network Infiltration Module enhances network security by simulating real-world threats to test firewalls, intrusion prevention systems (IPS), and endpoint security controls. Automate network security testing, uncover misconfigurations, and get actionable mitigation insights to improve your defense strategy.
Detect security gaps caused by misconfigurations and vulnerabilities before attackers can exploit them.
Continuously validate NGFW, IPS, and EDR controls without the need for manual testing.
Ensure your security controls remain effective by testing them against the latest real-world threats.
Simulate attacks in a risk-free environment without disrupting business operations.
Gain insights into how well your security team detects and mitigates network threats.

Improve Your Network Security Testing with Actionable Insights

.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)







.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.