Web Application Attack Module
The Picus Web Application Attack Module simulates real-world web attacks to test your security controls. Identify gaps, validate the effectiveness of your WAF, and strengthen your web application security.
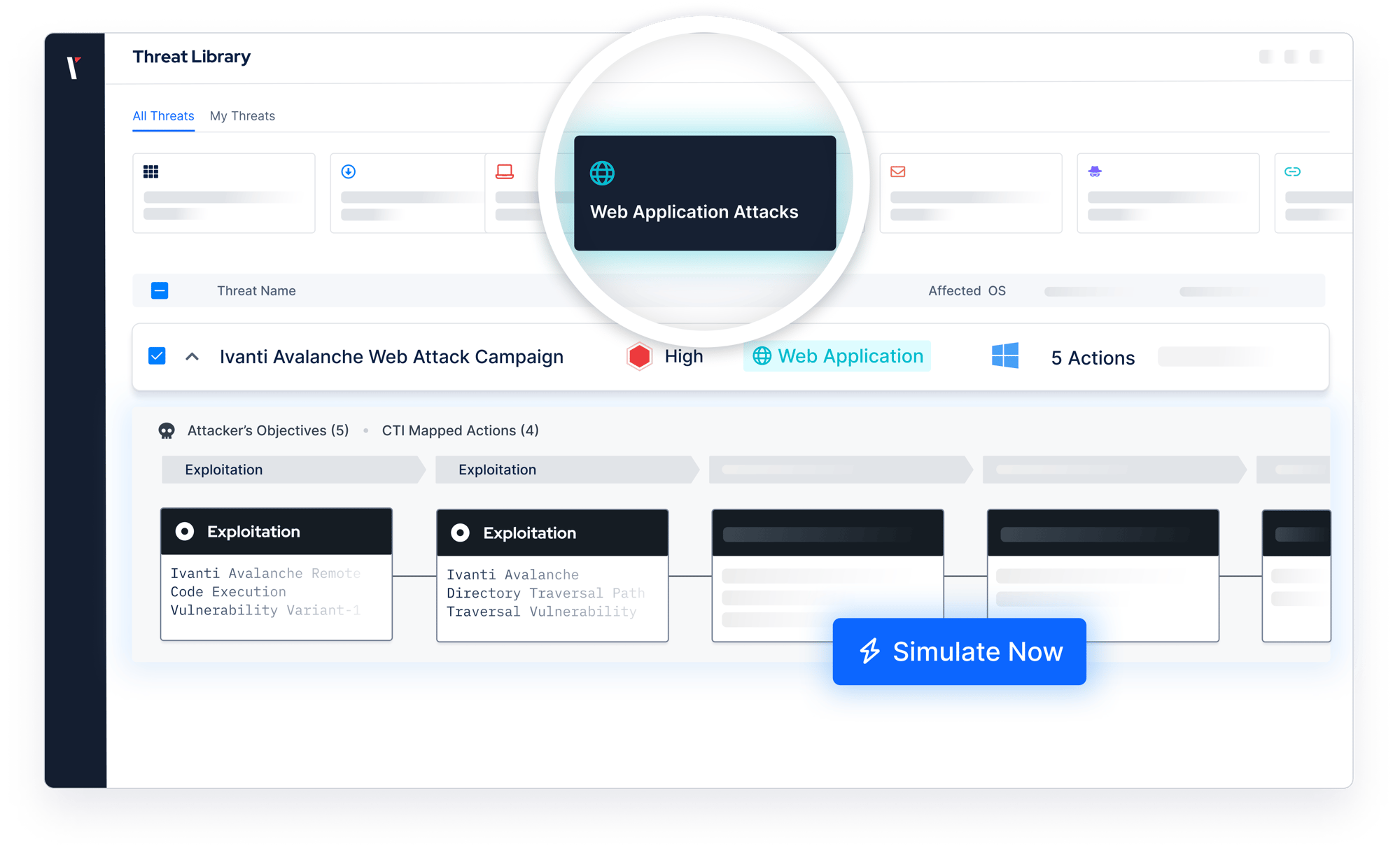
Why Validate Your Web Application Security?
The effectiveness of Web Application Security Controls can degrade over time due to misconfigurations, evolving threats, and policy changes. Without continuous validation, organizations risk exposing critical applications to cyberattacks. Web security testing ensures that WAFs, IPS, Web Security Gateways (WSGs), and other defenses remain effective against real-world threats
-
Web applications are prime attack targets – Hackers exploit vulnerabilities to steal data, inject malware, and bypass authentication.
-
Security configurations degrade over time – Misconfigurations, outdated policies, and overlooked exceptions create security gaps.
-
Regulatory compliance requires ongoing validation – Many industries mandate regular security testing to meet compliance requirements.
-
Keeping up with evolving threats is essential – Cybercriminals constantly develop new attack techniques, making frequent validation crucial.
Enhance Your Web Security
with Automated Testing
The Picus Web Application Attack Module strengthens web application security by simulating real-world threats to test and identify gaps in Web Application Firewalls (WAFs), Intrusion Prevention Systems (IPS), Web Security Gateways (WSGs), and other security controls. Automate security validation, uncover misconfigurations, and gain actionable mitigation insights to fortify your defenses.
Access 260+ web threats and 2,150+ attack actions, including SQL Injection (SQLi), Cross-Site Scripting (XSS), Path Traversal, and Remote Code Execution.
Test web security controls from top vendors like F5, Fortinet, Citrix, AWS, and Azure with tailored attack templates.
Ensure your security controls remain effective by testing them against the latest real-world threats.
Identify security gaps caused by misconfigurations and vulnerabilities before attackers can exploit them.
Continuously assess web security controls across various web security technologies with minimal to no manual effort.

Improve Your Web Security Testing
with Actionable Insights
.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)








.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.