Breach and Attack Simulation vs. Security Validation
LAST UPDATED ON JANUARY 06, 2026
What Is Security Validation?
Security validation is the practice of verifying whether an organization’s existing security controls actually prevent, if not, detect, or alert on real-world attack techniques within its own environment.
Rather than relying on configuration status, compliance checklists, or theoretical risk scores, security validation measures how controls perform when faced with real attacker techniques and behaviors. This includes validating technologies such as firewalls, WAFs, EDR/XDR, and SIEM to determine whether attacks are genuinely prevented or detected.
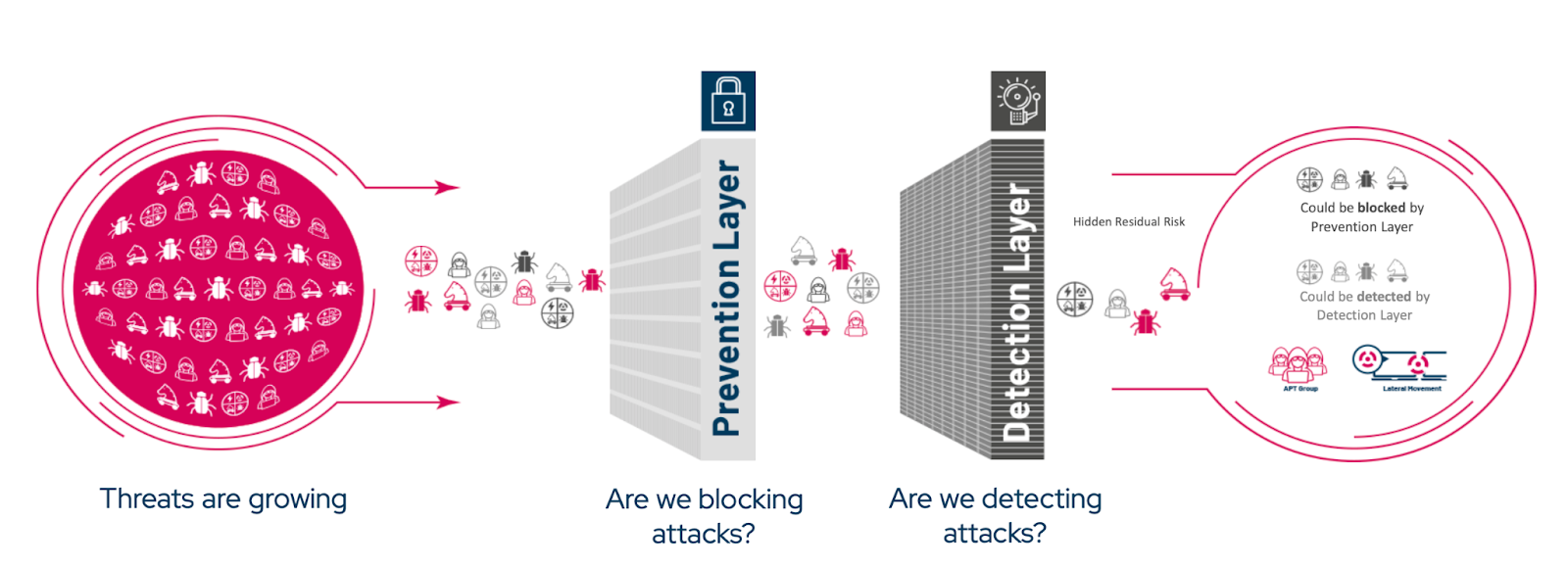
In practice, security validation answers a critical question: If an attacker tried this today, would our defenses work?
Security Validation in the CTEM Framework
|
TL:DR;
|
Within Continuous Threat Exposure Management (CTEM) programs, security validation is the core mechanism of the validation phase.
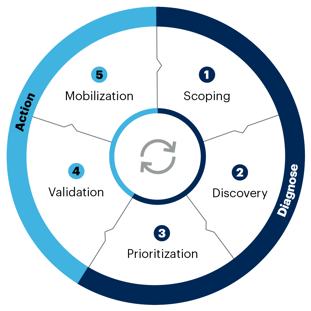
Figure 1: CTEM Process by Gartner
Once exposures are identified and prioritized based on asset criticality and severity metrics such as CVSS and EPSS, validation distinguishes between theoretical risk and exposures that attackers can actually exploit within the organization’s unique business context and existing prevention and detection controls. This allows organizations to focus remediation on what truly matters, rather than spreading effort across every reported vulnerability.
Security validation can be delivered in an automated manner through Adversarial Exposure Validation (AEV) technologies, including Breach and Attack Simulation (BAS) tools and Automated Penetration Testing. These tools provide direct evidence of how defenses perform against realistic attack scenarios.
This blog focuses specifically on BAS, how it differs from traditional security assessments and how it supports CTEM by enabling continuous, scalable security validation.
The Goal of a Security Validation Practice
The primary goal of security validation is to distinguish real, attacker-feasible risk from theoretical risk.
By continuously validating exposures against real attack techniques, organizations gain an accurate, evidence-based view of their security posture. This allows teams to:
- Prioritize remediation based on actual attack success, not CVSS & EPSS scores alone
- Reduce noise from non-exploitable vulnerabilities
- Validate the effectiveness of existing security investments
- Adapt defenses as threats, tools, and environments change
Ultimately, security validation replaces assumptions with proof, forming the foundation of effective exposure management, and modern cyber risk reduction strategies.
-1.png?width=242&height=177&name=image%20(1)-1.png)
2X Prevention with BAS
How to leverage Breach and Attack Simulation to optimize your security
controls and block twice as many threats in 90 days.
Traditional Security Validation Methods and Their Limits
Traditional security validation approaches such as red teaming, penetration testing, and vulnerability assessment remain important components of a mature security program. However, these methods are inherently limited in their ability to provide continuous, comprehensive validation in modern, rapidly changing environments. This section compares traditional security validation methods with BAS to highlight how BAS addresses these limitations and enables continuous, evidence-based security validation.
Breach and Attack Simulation vs. Penetration Testing
TL;DR: Manual penetration testing provides deep, human-led insight into a limited set of attack paths but delivers only a point-in-time snapshot that doesn’t scale across modern environments. BAS continuously and safely validates security controls at scale by emulating real-world attacker techniques, turning theoretical risk into evidence-based, continuously verified exposure reduction.
|
Category |
Manual Penetration Testing |
Breach and Attack Simulation (BAS) |
|
Primary Focus |
Human-led exploitation of discovered security weaknesses through expert-driven testing, creative exploit chaining, and contextual attacker decision-making. |
Automated adversarial emulation and simulation used to validate the effectiveness of implemented security controls in preventing, detecting, or alerting on real-world attacker techniques. |
|
Coverage |
Limited coverage, typically 10–15 percent of a domain. Does not scale across thousands of identities, assets, and trust relationships (operationally infeasible). |
Broad coverage across the integrated security controls. Tests attacker techniques across the full kill chain at scale. |
|
Key Enablers |
Human expertise, experience, and custom tools or exploitation scripts/binaries. Results depend heavily on individual tester skill. |
Automated adversarial attack scenarios mapped to real-world TTPs across network, host, application, and data layers, continuously updated through threat intelligence and designed for safe execution in production. |
|
Frequency |
Conducted annually or a few times per year due to cost, operational impact (business discontinuity risk due to network load), and manual effort. Produces a point-in-time snapshot. |
Runs continuously or on demand. Provides an always-current view of exposure and control effectiveness. |
|
Automation & Consistency |
Fully manual. Results vary by tester and engagement. Re-testing requires a new engagement. |
Fully automated (with support for customization) and repeatable. Runs consistently at any time with stable quality, under a fixed subscription model (e.g., modules and agent count) rather than per-test engagement. |
|
Stealth, Noise & Operational Impact |
Often noisy and resource-intensive due to aggressive scanning and active exploitation, generating network stress, alerts, and operational friction that limit how frequently and broadly testing can be performed. |
Designed to be completely safe. Simulates & emulates attacker/malware behaviors without destructive exploitation, minimizing network noise and allowing frequent execution in production. |
|
Depth vs Breadth |
Strong depth through creative, exploratory testing and novel vulnerability exploitation methods. Limited breadth. |
Strong breadth across known and emerging attacker techniques observed in the wild. Supports zero-day campaigns and emerging threats (e.g., malware and threat groups) within a 24-hour SLA when a reliable, publicly available proof of concept exists. Complements, rather than replaces, human creativity. |
|
Validation Capability |
Demonstrates exploitability during the test window but does not continuously validate controls or remediation. |
Continuously validates whether controls block, if not detect, or alert on attacker techniques and automatically retests fixes (remediation validation). |
|
Value & Context |
Produces high-quality findings but across a limited scope. Human-led testing can validate only a small subset of vulnerabilities, making it difficult to use as a validation tool for smarter exposure prioritization tool across the environment. |
Provides contextual, evidence-based validation showing which exposures can be silently exploited by specific adversarial techniques in real-world breaches. |
|
Role in CTEM |
Supports deep, expert-driven investigation but is not designed to operationalize continuous or broad validation, as human-led testing cannot scale across the volume of exposures in modern environments |
Operationalizes the validation step of CTEM by continuously validating how security controls respond when real-world attacker techniques attempt to exploit exposures pre-prioritized by scoring systems such as CVSS and EPSS, converting score-based prioritization into validated, evidence-driven prioritization. |
|
Overall Role |
Point-in-time expert assessment suited for complex scenarios, audits, or regulatory requirements. |
Continuous, scalable security validation that strengthens exposure management end to end. |
Breach and Attack Simulation vs. Vulnerability Scanning
TL;DR: Vulnerability scanning discovers large volumes of potential issues but lacks the context to determine which ones are actually exploitable or impactful in a real environment. BAS validates real-world exploitability by safely emulating attacker behavior, cutting through noise to prove which vulnerabilities truly matter and whether existing controls effectively stop them.
|
Category |
Vulnerability Scanning |
Breach and Attack Simulation (BAS) |
|
Purpose |
Identifies known issues such as missing patches, misconfigurations, or outdated software via signatures and configuration checks. |
Validates whether security controls actually prevent, detect, and alert on real-world attack techniques in the organization’s environment. |
|
Detection vs Validation |
Detects potential vulnerabilities but cannot confirm real exploitability or business impact in a context. |
Safely validates real exploitability and impact by running adversarial behaviors. Confirms whether controls such as NGFW, WAF, IPS, and EDR block attacks or detect and alert on real-world TTPs. |
|
Context & Prioritization |
Treats vulnerabilities in isolation, often resulting in long lists of theoretical risks. |
Adds adversarial context. Shows which attack kill chain techniques can be successfully executed or are blocked in the organizational environment, and converts raw findings into validated, prioritized exposures. |
|
False Positives / Noise |
Generates large volumes of alerts; can overwhelm teams with false positives or minor issues. (Up to 40% of scanner alarms are false positives.) |
Reduces noise by validating exploitability, filtering out theoretical or already mitigated findings and allowing teams to focus on exposures that can realistically be abused. |
|
Volume Challenge (40K+ CVEs/year) |
CVSS or EPSS may label 61% of CVEs as critical without considering environmental exploitability (no context of implemented security controls). Causes alert fatigue and misprioritization. |
Validates real-world risk by showing which CVEs are actually exploitable in the organization’s environment and which are effectively prevented, even if scored critical (CVSS). Conversely, it can reveal how lower-scored CVEs can be chained to reach high-impact assets, preventing real threats from being buried under theoretical ones. |
|
Remediation Guidance |
Often provides generic advice such as “apply vendor patch.” Limited environment specific guidance. |
Provides actionable, tailored mitigation steps such as specific firewall rules, compensating controls, or disabling vulnerable protocols. Can integrate with SOAR or patch tools for automated remediation. |
|
Depth vs Breadth |
Broad coverage but shallow understanding; identifies issues but cannot confirm exploit chains or post compromise impact. |
Covers a wide range of attacker techniques across the kill chain (breadth) and validates how those techniques behave in practice, whether they are blocked, detected, or silently succeed. |
|
Integration Role |
Works rather as a discovery tool. Generates input data. |
Uses scanner findings as inputs and operationalizes the validation step of CTEM by proving which “critical” findings are actually exploitable and whether lower-scored findings can lead to a business-critical risk. |
|
Outcome |
Produces a list of potential issues; remediation is often manual and slow. |
Produces validated, prioritized exposures and confirms that fixes work through automated retesting. Strengthens exposure management end to end. |
Breach and Attack Simulation vs. Red Teaming
TL;DR: Red teaming delivers deep, high-fidelity insight into whether a skilled adversary can achieve real objectives, but it is intentionally scoped and episodic. BAS complements red teaming by continuously and safely validating security controls at scale, ensuring defenses remain effective against known and emerging attacker techniques between human-led engagements.
|
Category |
Red Teaming |
Breach and Attack Simulation (BAS) |
|
Primary Focus |
Human-led, objective-driven adversary emulation that tests people, process, and technology by pursuing real attacker goals. |
Automated adversarial emulation and simulation to validate whether security controls prevent, detect, or alert on real-world attacker techniques. |
|
Coverage |
Selective and scoped. Focuses on high-value assets, trust boundaries, and critical business paths. |
Broad and scalable coverage across the environment, validating controls across the full kill chain. |
|
Key Enablers |
Expert operators, stealth tradecraft, custom tooling, social engineering, and adaptive decision-making. |
Automated attack scenarios mapped to real-world TTPs, continuously updated and safe for production execution. |
|
Frequency |
Periodic (quarterly, semi-annual, annual). Produces a deep but time-bound assessment. |
Continuous or on demand. Maintains an always-current validation baseline. |
|
Automation & Consistency |
Fully manual. Results depend on operator skill, creativity, and engagement scope. |
Fully automated and repeatable with consistent quality and coverage. |
|
Stealth & Operational Impact |
Intentionally stealthy. Designed to evade detection and minimize noise, often indistinguishable from real adversary activity. Requires governance and executive awareness, not because it is noisy, but because it is real. |
Non-destructive and explicitly safe by design. Generates controlled telemetry without risk to production operations. |
|
Depth vs. Breadth |
Deep exploration of unknown attack paths, novel techniques, and human/system interactions. Limited breadth by design. |
Broad coverage of known and emerging attacker techniques at scale. Limited creativity but high consistency. |
|
Validation Capability |
Proves whether attackers can achieve objectives under real conditions, but not intended for continuous control revalidation. |
Continuously validates whether controls block, detect, or alert on attacker techniques and re-tests after remediation. |
|
Value & Context |
High-fidelity insight into real attacker success paths, organizational response gaps, and defensive blind spots. |
Evidence-based, control-level validation showing which exposures remain exploitable despite defenses. |
|
Role in CTEM |
Episodic, high-impact validation supporting maturity assessments and advanced scenarios. |
Operationalizes the Validation phase of CTEM continuously and at scale. |
|
Overall Role |
Simulates a real adversary operating quietly inside the environment to test true resilience. |
Provides continuous assurance that defenses remain effective against known attacker behaviors. |

BAS vs Traditional Methods
Are your security assessment methods truly keeping pace, or do you need a game-changer in your arsenal?
Breach and Attack Simulation for Continuous Security Validation
BAS enables continuous security validation by safely executing real-world attacker techniques in an organization’s live environment. Rather than assessing security controls based on assumptions, configurations, or static risk scores, BAS assessments provide direct evidence of whether those controls actually prevent, detect, or alert on adversarial activity.
Unlike point-in-time testing methods, BAS runs continuously or on demand, allowing organizations to validate their security posture as environments, configurations, and threat techniques change. This ensures that security validation reflects current operational reality, not last quarter’s assessment.
At its core, BAS answers three critical questions:
- Can an attacker successfully execute this technique in our environment?
- Which security controls stop or detect it?
- Where do real, exploitable gaps remain?
Which Security Controls Can be Validated by BAS?
BAS can validate the effectiveness of security controls deployed across all major layers of an organization’s environment. By safely emulating real-world attacker techniques, BAS tests whether these controls correctly prevent, detect, or alert on malicious activity under adversarial conditions.
This includes validating network security controls, endpoint protections, application-layer defenses, email and data security solutions, as well as cross-layer platforms responsible for detection, orchestration, and response. BAS confirms not only that these controls are deployed, but that they are correctly configured and function as intended against real attack techniques.
The table below summarizes the types of security controls that BAS can validate across the environment.
|
Layer |
Solutions |
|
Network |
NGFW, IPS, IDS, VPN, NAC, SWG |
|
Host |
EPP, EDR, HIPS, HIDS, Anti-Virus Software, Anti-Malware Software |
|
Application |
WAF, SEG |
|
Data |
DLP |
|
Cross Layer Solutions |
|
|
SIEM, SOAR, XDR |
|
For more information, visit our latest whitepaper on how BAS can be fit into your organization’s multi-layered security strategy.
Which Adversarial Techniques Can Be Emulated With BAS?
BAS platforms run predefined and continuously updated attack scenarios that reflect real-world TTPs. These scenarios typically include:
Attack Scenarios Tested
- Network infiltration attacks (malware download)
- Endpoint attacks (Windows, Linux, macOS, Kubernetes)
- Web application exploitation (both agent-based, and agentless)
- Email infiltration attacks
- Data exfiltration attacks
- URL filtering bypass attempts
Attack Vectors Emulated
To execute these scenarios, BAS tools employ multiple adversary techniques, including but not limited to:
- Malware and ransomware delivery simulations
- Atomic attack techniques (for example, credential dumping)
- Exploitation of known vulnerabilities and misconfigurations
- Threat group and Advanced Persistent Threat (APT) emulation
Why BAS Enables Continuous Security Validation
By continuously replaying real attack techniques and measuring defensive outcomes, BAS transforms security validation from a periodic exercise into an ongoing operational discipline. Each control change, detection update, or configuration adjustment can be revalidated immediately, closing the gap between security investment and real-world effectiveness.
The result is a security program grounded in evidence, not assumptions, where remediation is driven by confirmed exposure and validated control gaps rather than theoretical risk.
Key Advantages of Breach and Attack Simulation for Security Validation
BAS tools represent one of the most effective approaches to security validation because it continuously proves whether defenses actually work against real attacker behavior. Their value goes beyond discovery, delivering evidence-based validation and immediate risk reduction.
Continuous and Automated Validation
BAS moves security validation from point-in-time testing to continuous assessment. As environments, configurations, and threats evolve, BAS continuously validates whether implemented controls still perform as expected. This is essential in modern, fast-changing infrastructures where new exposures emerge daily and configuration drift is inevitable.
Realistic, Threat-Informed Attack Simulations
BAS safely simulates real-world attacker TTPs, mapped to active threat groups and emerging campaigns, without disrupting production. These simulations closely mirror how adversaries operate in practice, allowing organizations to evaluate whether controls truly prevent, detect, log, and alert under realistic conditions.
Coverage Across the Full Cyber Kill Chain
Unlike tools that focus on isolated weaknesses, BAS validates controls across the entire attack lifecycle, including initial access, execution, persistence, lateral movement, command and control, and impact. By aligning results with frameworks such as MITRE ATT&CK, BAS provides a holistic view of defensive readiness and highlights exactly where attacks succeed or fail.
Ready-to-Apply, Actionable Mitigation Guidance
This is where BAS delivers unique operational value. BAS does not stop at identifying gaps; it provides immediately usable remediation guidance, including:
- Vendor-specific prevention signatures (NGFW, IPS, WAF, EDR)
- Detection engineering content (SIEM, XDR, EDR rules)
- Verified mitigation recommendations that are pre-tested against the simulated attack
This allows teams to move directly from validation to remediation, dramatically reducing mean time to fix and eliminating guesswork.
Cost-Effective and Scalable Security Validation
Manual penetration testing and red teaming are valuable but expensive, resource-intensive, and infrequent. BAS automates repeatable validation at scale, reducing reliance on constant manual effort while enabling frequent, consistent testing. This makes continuous validation financially sustainable and operationally realistic.
Adaptability to Emerging Threats
Modern BAS platforms continuously integrate new threat intelligence, including ransomware campaigns, actively exploited vulnerabilities, and real-world adversary behavior. This ensures organizations validate defenses against today’s threats, not last year’s attack techniques.
Quantifiable Metrics for Risk and Exposure Reduction
BAS produces measurable, defensible metrics that show:
- What percentage of attacks are blocked
- What bypasses prevention but is detected
- What succeeds without detection
These metrics enable CISOs to demonstrate measurable risk reduction over time, justify investments, and communicate security effectiveness in business-relevant terms.
Why BAS Is Core to CTEM for Security Validation
Security Validation as the Powerhouse of CTEM
Most CTEM programs fail for one simple reason: they generate prioritized lists, not proof.
Discovery and prioritization are well understood. Asset inventories, vulnerability scanners, attack surface management, and risk scoring all do a decent job of answering “what could be risky.”
What executives actually need answered is different:
|
"Which of these risks can actually hurt us right now?" |
That question is answered in the validation phase of CTEM. And validation is not a single technique, tool, or vendor category. It is a discipline.
Validation ≠ Automated Pentesting ≠ BAS
One of the biggest sources of confusion in CTEM programs is the assumption that validation equals pentesting, or that BAS replaces pentesting. Neither is true.
Validation answers three distinct questions, each served by different techniques:
|
Differentiators |
Best-Fit Method |
|
Delivers deep vulnerability and attack path validation snapshots, highlighting security posture risks. Finding-based reporting; open weaknesses, attack paths, remediation summary, and systemic issues. |
Automated Pentesting (PTA) |
|
Ideal for continuous baselining and consistent tracking of posture improvements or regressions. Reports both blocking and non-blocking outcomes; not only weaknesses but strengths. Prevention and Detection based ATT&CK coverage, Threat Group, Attack Vector, Security Control Device based metrics are commonly used. |
Breach and Attack Simulation (BAS) |
CTEM expects organizations to combine these methods, not choose between them.
Action Plan for CTEM: Do You Need BAS, Automated Pentesting, or Both?
CTEM is cyclical and continuous. BAS and Automated Pentesting are complementary, not substitutes.
Recommended CTEM validation flow
- Start with BAS
- Establish defensive baseline
- Validate detection & prevention
- Catch drift and blind spots early
- Add Automated Pentesting
- Validate high-risk exposures
- Prove attack paths
- Quantify business impact
- Feed both results back into prioritization & mobilization
Why this matters
- BAS without pentesting → “We think we’re safe”
- Pentesting without BAS → “We found paths, but why didn’t controls stop them?”
- Together → Evidence-driven exposure reduction
Picus Security Control Validation (SCV) as the Best BAS Solution
Breach and Attack Simulation only delivers value when it produces clear, repeatable proof that security controls actually work in real environments. Picus Security Control Validation (SCV) is purpose-built for this exact mission.
Picus SCV goes beyond running simulations. It continuously validates prevention, detection, and response controls across the full attack lifecycle, mapped to real-world adversary behaviors and aligned with CTEM outcomes. Security teams use Picus to:
- Prove which attacks are actually blocked, detected, or missed
- Continuously validate controls without disrupting production
- Eliminate false priorities by confirming what is truly exploitable
- Turn findings into vendor-specific, actionable remediation
- Track defensive improvement over time with evidence-based metrics
Rather than replacing automated pentesting or red teaming, Picus SCV completes the validation layer of CTEM, giving CISOs the confidence to focus resources where they reduce real exposure; not theoretical risk.

.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)







