Ransomware Incidents Reported to UK Financial Regulator Doubled in 2023
LAST UPDATED ON JANUARY 12, 2024
Picus submitted a Freedom of Information (FoI) request to the UK Financial Conduct Authority (FCA) to understand the degree to which cybercrime has impacted the finance sector in the first six months of 2023. The data we obtained reveals a resurgence in ransomware-related incidents following a quieter 12 months in 2022.
Key findings of our FOI analysis include:
- The FCA received 51 cyber incident reports in H1 2023, up 10% compared to H1 in 2022.
- Twice as many ransomware incidents were reported in H1 2023 (19) compared to the same period in 2022.
- Nearly a third of all cyber incidents reported in H1 2023 were categorized as ransomware (31%). This percentage is up from 11% in H1 2022.
- Far more cyber incidents are reported to the FCA in March than in any other month. Since 2021, 12.8 reports, on average, have been submitted in March. December is the quietest month for FCA cyber incident reports (2.5).
Commenting on the findings, Dr. Suleyman Ozarslan, Co-Founder and VP of PicusLabs said:
“Ransomware remains a scourge for every sector and every security team. Our data reflects a common pattern seen in recent years. Ransomware gangs burst onto the scene, scale up their campaigns, and put a target on their backs. After the coordinated crackdowns and arrests from global government agencies, ransomware activity can start to die down until the next group looks to fill the void left by their predecessor.
“The first six months of 2023 was a hectic period for financial services security teams. This sector has always been one of the biggest targets for both politically and financially motivated cybercriminals. Cl0p Ransomware, for example, is known to target major banks.
“Two major Microsoft vulnerabilities may have also contributed to more incidents than usual this year, as was the case in 2021 when the Hafnium hacking group was actively exploiting another Microsoft Exchange Server bug. The increasing complexity of malware deployed by adversaries may also be a factor. The Picus Red Report 2023 found that modern malware is now capable of performing far more actions across the cyber-kill chain, to more effectively evade defences. More than one-third of malware samples exhibit more than 20 individual Tactics, Techniques and Procedures.
“The numbers for the first half of 2023 are also far higher than the second half of 2022 when cyber incident reports almost ground to a halt by the end of the year. It is interesting to see such consistently low numbers in December. A slight decline in cyber incident reports would reflect the fact that many people are away from the office, but there is such a sizable gap between December and January figures. We know that breaches happen all year round, so the numbers should fall off a cliff in this manner. I don’t know which is worse, if security teams don’t discover incidents in December, or if they choose not to report them until after the holidays.”
Methodology
As part of the FOI request process, Picus received month-by-month data on the number and type of incidents reported to the FCA by financial organizations. This information can be compared to previous FCA data breach statistics, including Picus FOI requests for FCA data in 2021 and 2022.
The FCA regulates the activity of more than 50,000 UK financial services firms. If any of these businesses suffer a material cyber incident, they must notify the FCA immediately. According to the FCA, a material incident is defined as a cyber incident that:
-
Results in significant loss of data, or the availability or control of its IT system
-
Impacts a large number of victims
-
Results in unauthorized access to, or malicious software present on, its information and communication systems.
Cyber incidents increase
The number of cyber incidents reported to the FCA in the first half of 2023 increased slightly (11%) compared to the same period in 2022. However, cyber incidents this year are still significantly lower than the 2021 high. 2021 represents a notable outlier for financial firms being breached by attackers. 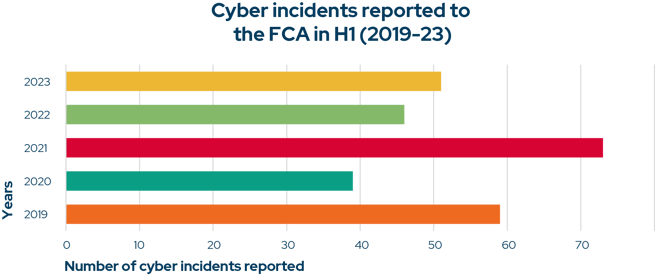
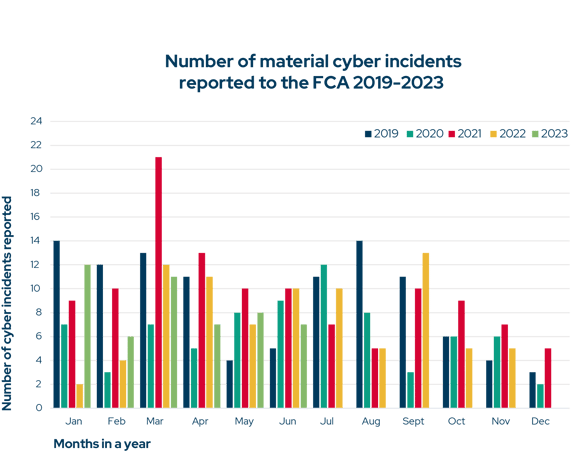
When grouped by month, it becomes clear that FCA cyber incident reports tend to decline throughout the year, and some months are typically far busier for security teams than others. Since 2019, far more cyber incidents have been reported to the FCA in March than any other month – with an average of 12.8.
December is the quietest month for FCA cyber incidents reports by some distance (only 2.5 reports on average). The disparity between January and December incident numbers suggests that security teams may struggle to identify or report breaches during the holiday period – or choose to wait until it is over.
As for the relatively high number of incidents reported in March 2019, 2021, 2022 and 2023, there is an element of history repeating itself. In 2023, there was a noticeable increase in exploitable zero-day vulnerabilities in widely used software. Among the most critical were CVE-2023-23397 affecting Microsoft Office Outlook, and CVE-2023-24880 impacting Microsoft Windows. This may be a significant contributing factor to increased cyber incidents in H1 2023. This was also the case in March 2021 when the Hafnium hacking group was actively exploiting the highly-publicized Microsoft Exchange Server vulnerabilities. It remains the single biggest month for FCA cyber incident reports.
Resurgent Ransomware in the finance sector
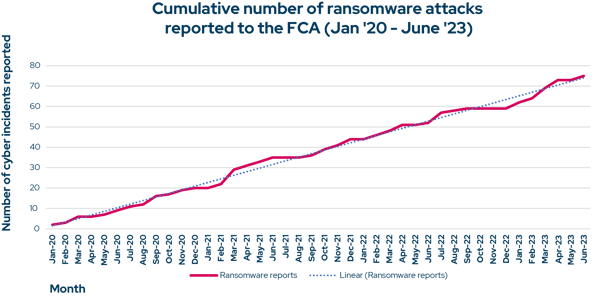
30% of cyber incidents reported to the FCA in the first half of 2023 were ransomware attacks. This figure is up significantly from only 11% in the previous year. The cumulative chart below shows that virtually no ransomware incidents were reported to the FCA between July 2022 to December 2022, during an unusually quiet period.
Final thoughts
Dr. Suleyman Ozarslan
“The bad news is that ransomware has always been a low-risk and high-reward business model for financially motivated cyber threat actors. These adversaries will always target financial institutions due to the value of their assets. They are also incredibly difficult to stop at scale. As governments clamp down on active ransomware groups, new ones will appear in their place. As security teams patch their systems and develop strategies for detecting and preventing existing ransomware strains, sophisticated new campaigns will emerge.
“The good news is that UK banks and other financial organizations are among the most well-prepared to prevent ransomware. As threats continue to evolve, organizations must remain vigilant. They must remember that preventing ransomware is much more cost-effective and desirable than recovering from a successful attack. This requires proactively hardening defenses and validating that security controls and processes are effective at defending against the latest risks.
“When a new threat or ransomware group appears, banks must test their defenses against it immediately. If any gaps or vulnerabilities are identified, existing security tools must be updated and optimized accordingly. New tools and processes may also be required. Banks must adopt this continual approach to threat exposure management, or risk being breached and filing reports to the FCA, ICO and police.”
Download the Picus Security whitepaper Optimizing your Cyber Security Readiness for Financial Organizations to learn more about how financial firms can validate and continually enhance their cyber readiness.
About Picus
Picus Security helps security teams consistently and accurately validate their security posture. Our Security Validation Platform simulates real-world threats to evaluate the effectiveness of security controls, identify high-risk attack paths to critical assets, and optimize threat prevention and detection capabilities.
As the pioneer of Breach and Attack Simulation, we specialize in delivering the actionable insights our customers need to be threat-centric and proactive.
Picus has been named a ‘Cool Vendor’ by Gartner and is recognized by Frost & Sullivan as a leader in the Breach and Attack Simulation (BAS) market.


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






