The Importance of Continuously Tracking Changes in Your Security Posture
LAST UPDATED ON DECEMBER 26, 2024
Picture this: An attacker launching a full-scale campaign against your organization's infrastructure. How would your defenses hold up in the face of a real-world cyber attack? How resistant are they against cyber threat actors and risks? As a cybersecurity professional, these are the critical questions that probably keep you awake at night.
That's where the importance of validating your security controls from the adversary's perspective becomes evident. It's no longer sufficient to simply patch vulnerabilities and hope for the best. Continuous testing, updating, and optimization of your defenses are crucial in keeping pace with the ever-evolving threat landscape. After all, the cost and time required to recover from a significant cybersecurity incident can be overwhelming.
The Need to Measure Improvement Over Time
Safely simulating real world threats is a proactive approach to test the effectiveness of your security controls in place. For cyber teams, the ability to measure the effectiveness of their security posture and enhancements over time becomes increasingly important. It’s not enough anymore to solely rely on point-in-time assessment exercises such as quarterly penetration tests or yearly red team engagements.
Let’s face it: securing an environment against evolving threats is like hitting a moving target. The ability to prevent and detect threats is constantly fluctuating due to the ever-evolving nature of security threats, and understanding their causes is absolutely critical to staying protected at all times. Generally, there are two main reasons why your security effectiveness could drop:
1) There is a newly emerging threat against which you are not yet protected. It usually takes a few days until your security vendors update their signatures.
2) There has been a change in a security control’s policy and you are suddenly not preventing or detecting a threat which you previously could.
In both of these two cases you not only want to be informed immediately, but you also want to understand where the drop in your ability to defend is coming from.
Introducing Simulation Comparison:
Our newly developed Simulation Comparison feature in our Security Control Validation product empowers you to analyze your threat simulations in all detail. It allows you to not only understand why you may not be protected against a certain threat anymore, but it also helps you to visualize how your security posture is improving after applying specific measures, such as mitigations recommended by The Picus Complete Security Validation Platform.
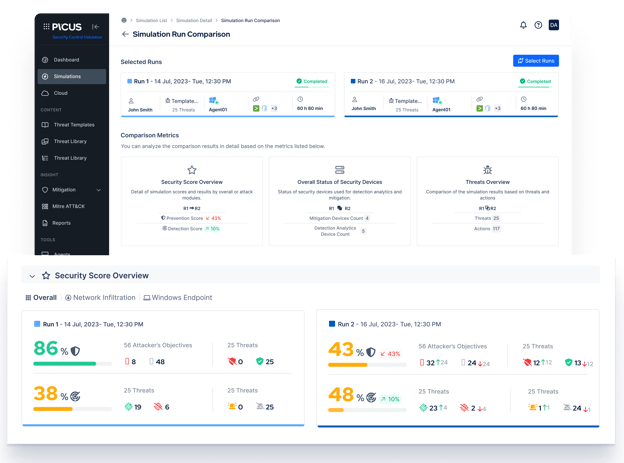
The Picus Platform's Simulation Comparison feature, enabling users to compare two distinct simulation runs side by side. This helps in identifying declines and consistent enhancements in security posture over time.
Some key benefits include:
-
Enables users to compare the results of different simulation runs.
-
Provides insights into the impact of different mitigations on simulation performance.
-
Provides a more comprehensive view of simulation performance, enabling users to make more informed decisions.
Understanding Security Score Fluctuations:
When utilizing our Simulation Comparison feature, you can now gain valuable insights into the reasons behind changes in your security scores. Whether witnessing a drop or an increase, you can filter the results to identify which threats were previously blocked but are now causing issues or vice versa. This visibility empowers you and your security team to pinpoint vulnerabilities, comprehend the impact of security measure changes, and take targeted actions to address any shortcomings.
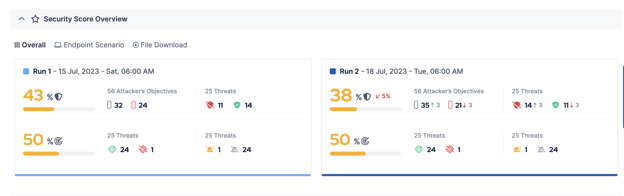
This example illustrates that repeating simulation runs in the future can generate different security score results. For instance, there has been a decrease in the prevention security score from 43% to 38%. Clearly, certain threats, which were previously blocked, are now able to bypass security measures.
Realizing that you can't stop a threat that you used to be able to control makes you wonder: What's different now? This is like a big clue that something has changed. Potential factors contributing to this change could include updates in threat tactics, techniques, or procedures (TTPs), alterations in your security controls, or new attack vectors that bypass your existing defenses. By delving deeper into the context surrounding the unblocked threat, you can unveil the specific elements that have led to this shift. This helps you find out exactly why you can't block the threat anymore. Once you know this, you can come up with a plan to handle the new threat and make your defenses stronger.
The image above serves as an excellent example for demonstrating to our users the causes of security score fluctuations. For instance, a notable decrease in the security score indicates the presence of threats that were previously blockable but are no longer being successfully blocked. By filtering the search accordingly, you can identify the specific threat that you are currently unable to block. In this scenario, it appears that the user was previously successful in blocking the Phoenix Cryptolocker Ransomware Download Threat, but is currently unable to do so.
Quantifying Security Improvements:
Our Simulation Comparison feature doesn't just provide data—it enables you to communicate the value of your efforts. Demonstrate the effectiveness of newly implemented measures and drive ongoing enhancements to your cybersecurity defenses. Gain a clear grasp of how these measures elevate your security scores, offering tangible results and validation for your security enhancements.
Referencing the earlier mention that the user used to be able to block the Phoenix Cryptolocker Ransomware Download Threat but can't anymore, upon deeper investigation, Picus Security provides vendor-specific suggestions to address this. When you choose your vendor, you can see the measures they recommend for dealing with the threat. By running the simulation again after making these changes, users can see real proof of the improvements and validation for their enhanced security. Implementing these suggested measures results in a higher security score, which strongly demonstrates the success of your security enhancements.
17 STEPS
1. First, log in to The Picus Complete Security Validation Platform and navigate to the Simulations Tab
2. All the simulations you have created are listed here, and you can simply click on the one you wish to analyze. For the purpose of this guide, let's choose Stockholm-Daily as our selected simulation.
3. Great! Now, on the simulation details page, you will see a "Compare Run" button. Please go ahead and click on it.
4. Now, choose the simulation runs you want to compare.
5. Let's compare Jul 18 and Jul 15, 2023 simulation runs.
6. Click Compare
7. On this page, you can compare the results of your simulation runs over time to understand how changes in simulation parameters impact the performance across various aspects. For more detailed insights, scroll down.
8. In this example, your security score has dropped from 43% to 38%. It looks like a previously blocked threat is no longer being addressed. To find out why, scroll down to the Threats Overview section.
9. Let's now filter down the Prevention Results to identify the threats that you were previously able to block but can no longer block. This will help you understand the reason behind the drop in your security score.
10. Choose the filter option "Blocked to Not Blocked."
11. Click Apply
12. On the results page, it appears that there are 3 main threats that you used to block but no longer do. One of them is the "Phoenix Cryptolocker Ransomware Download Threat" Let's investigate it further.
13. Click on the red Not Blocked icon for further information.
14. Now, you can see an overview. Click on the Prevention tab to access the Picus vendor-based mitigation suggestions.
15. You can learn how you can block this threat again going forward by receiving specific mitigation recommendations. Select the vendor you are using. Let's assume you are using Checkpoint.
16. By clicking on the vendor, you can see the related ID number and signature name. Clicking further will provide more detailed information.
17. That's it! By re-simulating, you can observe tangible results and validate your security enhancements as you apply these mitigation recommendations, resulting in an increased security score.
Here's an interactive tutorial
** Best experienced in Full Screen (click the icon in the top right corner before you begin) **
In conclusion, our newly launched Simulation Comparison feature will empower you to gain actionable insights, measure security improvements, identify emerging threats, and optimize your security measures.
Our mission at Picus security is to equip you with the necessary tools to navigate the ever-changing landscape of emerging threats. We empower you to validate the effectiveness of your prevention and detection controls through 24/7 safe simulations of real-world threat attacks.
Are you interested in trying our attack simulation capabilities for free?
Click here to start your 14-day free trial today or book a demo with one of our Picus experts


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






