Continuous Security Validation refers to a proactive security assessment approach, providing consistent assessment and validation of an organization's defenses. This automated process enables the identification of policy mismatches and overlapping security controls, detection and mitigation gaps in defense solutions.
In this blog, we examine the Continuous Security Validation, its importance to organizations, the lifecycle that constructs it and explain how automatizing this process will improve your overall security posture.
What Is Continuous Security Validation?
Continuous security validation is a proactive security assessment approach that replicates real-world attacks to test the effectiveness of security controls. It helps organizations identify misconfigurations, excessive privileges, and other weaknesses that attackers commonly exploit.
It helps organizations identify vulnerabilities in the security infrastructure by simulating potential threats, thereby enabling them to mitigate identified gaps and validate the effectiveness of security measures. This approach ensures that the organization's cybersecurity posture is resilient, up-to-date, and capable of defending against both existing and emerging threats.
Why Is Continuous Security Validation Important?
Continuous Security Validation is crucial because it enables organizations to continuously test the effectiveness of their security controls and identify potential attack vectors before attackers can exploit them. This proactive approach ensures that defenses remain robust and adaptive to evolving threats, helping organizations stay ahead of cyberattackers and data breaches.
Through cybersecurity validation, organizations can gain a clear understanding of how their security controls perform against real-world threats. This not only strengthens their overall security posture but also helps verify and refine existing defenses to reduce vulnerabilities. By adopting Continuous Security Validation, organizations can address six key aspects of cybersecurity, enhancing their ability to detect, respond to, and mitigate risks effectively.
a. Identifying the Policy Mismatches in Security Controls: Continuous Security Validation can help organizations identify the policy mismatches in their security controls by simulating potential threats. This allows organizations to see exactly where their defenses may be lacking and to improve their security measures accordingly.
b. Increasing the Effectiveness of Security Solutions: Continuous Security Validation can help organizations increase the effectiveness of their security solutions by identifying gaps in the organization's rules base and ensuring that detection rules are correctly identifying threats. Consequently, Continuous Security Validation can help to improve the performance of security solutions such as NGFW, SIEM, IPS & IDS, EDR, DLP and XDR.
c. Prioritizing Security Efforts: Continuous Security Validation can help organizations prioritize their security efforts by visualizing gaps and providing data on which threats a particular mitigation measure can block. This information can help organizations to focus their security efforts on the most critical areas.
d. Monitoring Changes in Detection Coverage: Continuous Security Validation can help organizations monitor changes in detection coverage by continuously testing the effectiveness of detective security controls and visualizing trends in detection coverage. This information can help organizations to quickly address any sudden changes or drops in their detection abilities.
e. Validating Applied Mitigations: Exposure Management platforms provide a way for organizations to validate that the security measures they have implemented are working as intended. This information can help organizations to ensure that their security measures are effective and that they are not being bypassed by attackers.
f. Enhancing Log Management Practices: Continuous Security Validation can help organizations enhance their log management practices by validating that the necessary logs to detect attacks are being collected. This information can help organizations to improve their threat detection, mitigation, and incident investigation capabilities.
By implementing Continuous Security Validation, organizations can improve their cybersecurity posture and protect themselves from cyberattacks.
The Continuous Security Validation Lifecycle?
A typical life-cycle of a Continuous Security Validation consists of four key steps: discover, validate, prioritize and optimize.
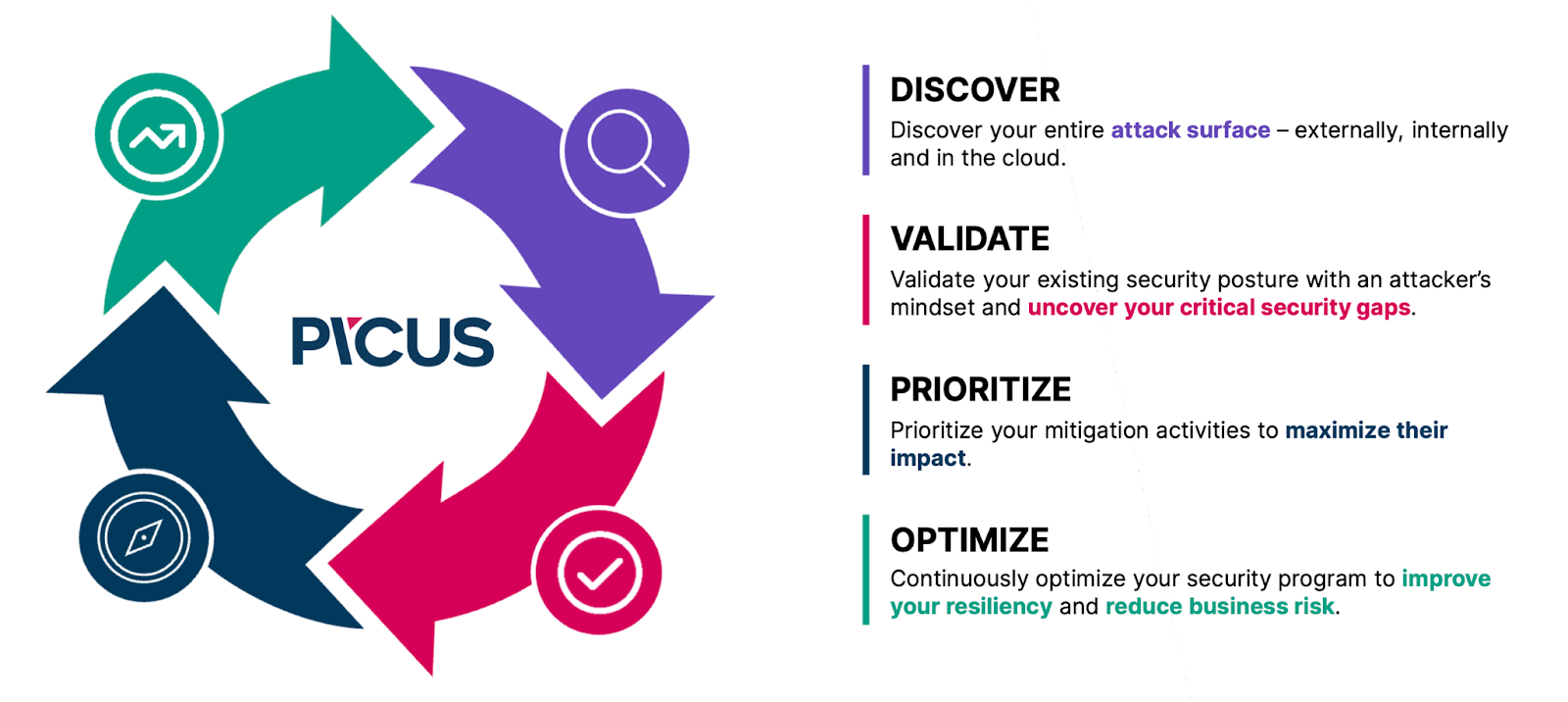
Figure 1. Continuous Security Validation Lifecycle
The life-cycle starts with an extensive discovery process to map out an organization's entire attack surface, including both external and internal assets, as well as those in the cloud.
Once all the organizational assets are cataloged, it's essential to validate your security posture against cyber threats that particularly target your sector or region. This process mimics the mindset of a potential attacker, examining your organization from both internal and external perspectives to uncover possible paths an attacker might use to access sensitive assets. These could include a domain admin account, a critical database with customer PII, and more.
Just as in chess, not all pieces in your game hold equal value. In the second step, you've validated the critical security gaps that require immediate attention. It's then crucial to prioritize these gaps based on the business-critical risk they pose to your organization. Prioritization is vital as it aids in managing resources efficiently to mitigate the risks that could cause the most severe damage to your business.
Having prioritized the security gaps that require immediate attention in the previous step, it's now time to mitigate them. This phase might involve implementing vendor-specific or generic prevention signatures to prevent cyber threats from executing malicious actions, or deploying vendor-specific rules for detection.
Continuous Security Validation vs. Traditional Security Assessment Solutions
Traditional security assessment approaches such as vulnerability scanning, penetration testing, and red teaming, differ from Continuous Security Validation platforms in a number of ways based on the details you provided:
a. Coverage of Threat Landscape
Traditional methods, while valuable, may not cover the entirety of the potential threat landscape. On the other hand, Continuous Security Validation platforms allow an organization to continuously simulate a vast array of potential threats and gain insights on how its security controls would respond to those threats.
b. Frequency and Timeliness
Traditional assessment methods such as vulnerability scanning, penetration testing, and red teaming are often performed periodically due to their labor-intensive and manual nature. This approach can lead to substantial gaps between assessments, during which security controls may become outdated or ineffective against emerging threats.
Continuous Security Validation platforms operate continuously, offering real-time insights into security posture and readiness, thereby maintaining an up-to-date defense against threats.
b. Prevention and Detection Layer Security with BAS
Traditional security assessments focus on identifying vulnerabilities that could be exploited in an attack. They might not provide complete insights into the performance of preventive security controls, like Next-Generation Firewalls (NGFW), Intrusion Prevention Systems (IPS), Anti-virus (AV), and others.
Similarly, the efficacy of detective security controls, such as SIEM, Intrusion Detection Systems (IPS), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR), might not be fully evaluated.
Consequently, traditional security assessments, such as vulnerability scanning and penetration testing, may not provide a complete picture of residual risks.

Figure 2. Breach and Attack Simulation Decreases Residual Risks
On the other hand, Continuous Security Validation solutions simulate attacks to assess both the prevention and detection capabilities of an organization’s security infrastructure.
Through continuous and comprehensive simulations, Continuous Security Validation platforms help organizations identify these residual risks, enabling an organization to further strengthen their security posture.
d. Actionable Insights
Finally, traditional approaches may not provide specific guidance on how to improve security effectiveness. However, Continuous Security Validation platforms can precisely detect gaps in security controls and offer guidance on where and what actions can be taken to fix these gaps, thereby enhancing cybersecurity resilience.
Therefore, while traditional methods still have their place in a comprehensive security program, a Continuous Security Validation platform provides more continuous, comprehensive, and actionable insights, helping an organization to improve its security controls' effectiveness and increase cyber resilience.


-3.png?width=353&height=200&name=image%20(79)-3.png)





.png?width=353&height=200&name=what-is-exposure-assessment-blog-preview%20(1).png)
